{"/api/v1/ncpl/currencies/getAll":{"body":[{"Name":"U.S. Dollar","Code":"USD","Symbol":"$","Separator":".","Culture":"en-US"},{"Name":"Euro","Code":"EUR","Symbol":"€","Separator":",","Culture":"en-US"},{"Name":"British Pound","Code":"GBP","Symbol":"£","Separator":".","Culture":"en-US"},{"Name":"Canadian Dollars","Code":"CAD","Symbol":"C$","Separator":".","Culture":"en-US"},{"Name":"Australian Dollars","Code":"AUD","Symbol":"A$","Separator":".","Culture":"en-US"},{"Name":"Indian Rupees","Code":"INR","Symbol":"Rs","Separator":".","Culture":"en-US"},{"Name":"China Yuan RMB","Code":"CNY","Symbol":"¥","Separator":".","Culture":"en-US"}],"status":200,"statusText":"OK"},"/api/v1/ncpl/usermanagement/uiuser/getHeaderUserInfo:\"{\\\"hideSupportPin\\\":true}\"":{"body":{"__ctxId":"20A7E072BFC347F6ADD838BD21622691","__isError":true,"__errorType":"Nc.Platform.Abstractions.UnauthorizedException","Http_WWW_Authenticate":"Bearer","StatusCode":"Unauthorized","LogLevel":3,"Message":"","InnerException":null,"HelpLink":null,"Source":"Nc.Security.Middleware"},"status":401,"statusText":"Unauthorized"},"/api/v1/ncpl/cart/user/getShoppingCartSummary:\"{\\\"finalTotalOnly\\\":true}\"":{"body":null,"status":200,"statusText":"OK"}}{"/api/v1/ncpl/simplekb/getarticle:\"{\\\"articleId\\\":9752,\\\"categoryId\\\":38}\"":{"body":{"Id":9752,"FriendlyId":"","ArticleTypeId":0,"Title":"How do I get A+ rating in SSLLabs?","ArticleName":"How do I get A+ rating in SSLLabs?","ArticleSummary":null,"PreponedSummary":false,"Approved":true,"Body":"DQoJCTxwPlNlY3VyaXR5IGlzIGEgYmFzaWMgcmVxdWlyZW1lbnQgb2YgYW55IHByb2plY3QgaW4gdGhlIElUIGluZHVzdHJ5LiBSYXBpZCBkZXZlbG9wbWVudCBvZiBuZXcgdGVjaG5vbG9naWVzLCBzdHJpY3QgY29tcGxpYW5jZSBzdGFuZGFyZHMsIGFuZCBldm9sdmluZyB0aHJlYXRzIGZyb20gaGFja2VycyBtYWtlIGl0IGVzc2VudGlhbCB0byBrZWVwIHlvdXIgYnVzaW5lc3PigJkgc2VjdXJpdHkgdG9vbHMgdXAtdG8tZGF0ZSBhbmQgYXMgc3Ryb25nIGFzIHBvc3NpYmxlLjwvcD4NCgkJPHA+TmFtZWNoZWFwIGlzIHByb3VkIHRvIHByb3ZpZGUgaXRzIGN1c3RvbWVycyB3aXRoIHRoZSBtb3N0IHN0YXRlLW9mLXRoZS1hcnQgb25saW5lIHNlY3VyaXR5IHNvbHV0aW9ucyBhdmFpbGFibGUuIEl04oCZcyBvdXIgam9iIHRvIG1ha2Ugc3VyZSBhbGwgb3VyIGN1c3RvbWVycyBhcmUgd2VsbC1wcm90ZWN0ZWQgYW5kIHNlY3VyZSBhdCBldmVyeSBsZXZlbC48L3A+DQoJCTxwPlRoaXMgYXJ0aWNsZSB3aWxsIGd1aWRlIHlvdSB0aHJvdWdoIHRoZSBtYWluIHBvaW50cyBvZiBoaWdoLWxldmVsIHNlY3VyaXR5LCBhcyB3ZWxsIGFzIHNob3cgeW91IGhvdyB0byBlbmhhbmNlIHRoZSBzZWN1cml0eSBvZiB5b3VyIElUIGJ1c2luZXNzLCB0aGVyZWJ5IGJ1aWxkaW5nIGN1c3RvbWVyIGNvbmZpZGVuY2UgYW5kIGxveWFsdHkuPC9wPg0KCQk8cD5JZiB5b3UgaGF2ZW7igJl0IGFscmVhZHksIHdlIHJlY29tbWVuZCBmaXJzdCB2aXNpdGluZyBvdXIgS25vd2xlZGdlYmFzZSB0byBsZWFybiBtb3JlIGFib3V0IFNTTHM6IDxhIGhyZWY9Imh0dHBzOi8vd3d3Lm5hbWVjaGVhcC5jb20vc3VwcG9ydC9rbm93bGVkZ2ViYXNlL2FydGljbGUuYXNweC83ODYvMzgvd2hhdC1pcy1hbi1zc2wtY2VydGlmaWNhdGUtYW5kLXdoYXQtaXMtaXQtdXNlZC1mb3IiIHRhcmdldD0iX2JsYW5rIj53aGF0IHRoZXnigJlyZSB1c2VkIGZvcjwvYT4gYW5kICA8YSBocmVmPSJodHRwczovL3d3dy5uYW1lY2hlYXAuY29tL3N1cHBvcnQva25vd2xlZGdlYmFzZS9hcnRpY2xlLmFzcHgvNzk1LzY5L2hvdy10by1pbnN0YWxsLXNzbC1jZXJ0aWZpY2F0ZXMiIHRhcmdldD0iX2JsYW5rIj5ob3cgdG8gaW5zdGFsbCBvbmUgb24gYSBzZXJ2ZXI8L2E+LiA8L3A+DQoJCTxwPkluIG91ciByZXZpZXcsIHdlIHdpbGwgdXNlIDxhIGhyZWY9Imh0dHBzOi8vd3d3LnNzbGxhYnMuY29tL3NzbHRlc3QvIiB0YXJnZXQ9Il9ibGFuayI+U1NMTGFiczwvYT4gYXMgYSB0ZXN0aW5nIHByb2plY3Qgb2YgPGEgaHJlZj0iaHR0cHM6Ly93d3cucXVhbHlzLmNvbS8iIHRhcmdldD0iX2JsYW5rIj5RdWFseXM8L2E+LCBhIGNvbXBhbnkgdGhhdCBwcm92aWRlcyBzdHJhdGVnaWMgc2VjdXJpdHkgc29sdXRpb25zLiBXZSB3aWxsIHVzZSB0aGVpciBBKyBpbmRpY2F0b3IgYXMgdGhlIGluZHVzdHJ5IGhpZ2ggc3RhbmRhcmQgaW4gU1NMIHNlY3VyaXR5IGFuZCB3aWxsIHRyeSB0byBtZWV0IGl0cyByZXF1aXJlbWVudHMuIFRoZSBTU0xMYWJzIGNoZWNrZXIgY292ZXJzIHR3byBzdWJzdGFudGlhbCBwYXJ0cyBvZiB0aGUgaW52ZXN0aWdhdGlvbjogPGI+QXV0aGVudGljYXRpb248L2I+LCB3aGljaCByZWZsZWN0cyBkZXRhaWxzIGFib3V0IGluc3RhbGxlZCBTU0wgY2VydGlmaWNhdGUgYW5kIGFkZGl0aW9uYWwgY2VydGlmaWNhdGVzIHByb3ZpZGVkIGJ5IGEgc2VydmVyLCBhbmQgPGI+Q29uZmlndXJhdGlvbjwvYj4sIHdoaWNoIHNob3dzIHNlcnZlciBzZXR0aW5ncyBmb3Igc2VjdXJlIG5lZ290aWF0aW9uIHVzZWQgaW4gY2xpZW50LXNlcnZlciBpbnRlcmFjdGlvbi48L3A+DQoJCTxwPg0KCQkJCTxiPkF1dGhlbnRpY2F0aW9uPC9iPg0KCQk8L3A+DQoJCTxwPlRoZSBmaXJzdCBibG9jayBvZiBBdXRoZW50aWNhdGlvbiBpcyBjYWxsZWQgPGk+U2VydmVyIEtleSBhbmQgQ2VydGlmaWNhdGUgIzE8L2k+LiBJdHMgbWFpbiBwb2ludHMgYXJlIGNlcnRpZmljYXRlIHZhbGlkaXR5LCBrZXkgdHlwZSBhbmQgc2l6ZSB1c2VkIHRvIGdlbmVyYXRlIGFuIFNTTCAob3VyIHN5c3RlbSBhY2NlcHRzIGJvdGggUlNBIGFuZCBFQ0Mga2V5cyksIHNpZ25hdHVyZSBhbGdvcml0aG0sIGFuZCB3aGV0aGVyIG9yIG5vdCBhbiBTU0wgY2VydGlmaWNhdGUgaXMgdHJ1c3RlZC48L3A+DQoJCTxwPlNTTCBjZXJ0aWZpY2F0ZXMgZW5jcnlwdCBkYXRhIGJlaW5nIGV4Y2hhbmdlZCBiZXR3ZWVuIHNlcnZlciBhbmQgYnJvd3NlciB3aXRoIHRoZSBoZWxwIG9mIGhhc2ggZnVuY3Rpb24uIFNIQS0xIHdhcyB0aGUgbW9zdCBhY3RpdmVseSB1c2VkIGhhc2ggZnVuY3Rpb24uPC9wPg0KCQk8cD5BY2NvcmRpbmcgdG8gdGhlIDxhIGhyZWY9Imh0dHBzOi8vY2FiZm9ydW0ub3JnLyIgdGFyZ2V0PSJfYmxhbmsiPkNlcnRpZmljYXRlIEF1dGhvcml0eSBhbmQgQnJvd3NlciBGb3J1bTwvYT4sICB3aGljaCBkZXZlbG9wcyBhbmQgZXN0YWJsaXNoZXMgcmVxdWlyZW1lbnRzIGZvciBDZXJ0aWZpY2F0ZSBBdXRob3JpdGllcyB0byBpc3N1ZSBwdWJsaWNseSB0cnVzdGVkIGNlcnRpZmljYXRlcywgU0hBLTEgc2lnbmF0dXJlIGFsZ29yaXRobSBpcyBiZWluZyBwaGFzZWQgb3V0IGFzIG9mIE5vdmVtYmVyIDIwMTQuIFRoaXMgbWFrZXMgaXQgbmVjZXNzYXJ5IGZvciBjZXJ0aWZpY2F0ZXMgdG8gYmUgaXNzdWVkIGluIFNIQS0yIHNvIHRoYXQgYWxsIGJyb3dzZXJzIHNob3cgbm8gd2FybmluZ3MuIE91ciBzeXN0ZW0gaXNzdWVzIGNlcnRpZmljYXRlcyBpbiBTSEEtMiBhdXRvbWF0aWNhbGx5LiBGb3IgdGhvc2UgY3VzdG9tZXJzIHdobyBpc3N1ZWQgdGhlaXIgU1NMcyBiZWZvcmUgdGhlIGVmZmVjdGl2ZSBkYXRlIG9mIHRyYW5zaXRpb24sIDxhIGhyZWY9Imh0dHBzOi8vd3d3Lm5hbWVjaGVhcC5jb20vc3VwcG9ydC9rbm93bGVkZ2ViYXNlL2FydGljbGUuYXNweC84MTEvNzAvaG93LWRvLWktcmVpc3N1ZS1teS1zc2wtY2VydGlmaWNhdGUiIHRhcmdldD0iX2JsYW5rIj5yZWlzc3VhbmNlPC9hPiBpcyBuZWVkZWQgdG8gZ2V0IHVwZGF0ZWQgYW5kIHZhbGlkIGNlcnRpZmljYXRlcy4gWW91IGNhbiBjaGVjayB3aGljaCBoYXNoaW5nIGFsZ29yaXRobSB0aGUgY2VydGlmaWNhdGUgaXMgaXNzdWVkIGluIHdpdGggdGhlIGhlbHAgb2YgPGEgaHJlZj0iaHR0cHM6Ly9zaGFhYWFhYWFhYWFhYWEuY29tLyIgdGFyZ2V0PSJfYmxhbmsiPnRoaXMgdG9vbDwvYT4uPC9wPg0KCQk8cD4NCgkJCQk8aW1nIGNsYXNzPSJrYi1pbWFnZSIgc3JjPSJodHRwczovL05hbWVjaGVhcC5zaW1wbGVrYi5jb20vU2l0ZUNvbnRlbnRzLzItN0MyMkQ1MjM2QTQ1NDNFQjgyN0YzQkQ4OTM2RTE1M0UvbWVkaWEvc3NsbGFiczEucG5nIiBhbHQ9InNzbGxhYnMxIiB3aWR0aD0iNzc3IiBoZWlnaHQ9IjUxMCIgYm9yZGVyPSIwIiAvPg0KCQk8L3A+DQoJCTxwPkFub3RoZXIgaW1wb3J0YW50IHBvaW50IChoaWdobGlnaHRlZCBpbiBncmVlbiBpbiB0aGUgc2NyZWVuc2hvdCBhYm92ZSkgaXMgd2hldGhlciB0aGUgc2VydmVyIHJldHVybmVkIGNlcnRpZmljYXRlcyBpc3N1ZWQgYnkgQ2VydGlmaWNhdGUgQXV0aG9yaXR5IGR1cmluZyB0aGUgdGVzdC4gSW50ZXJtZWRpYXRlIENBIGNlcnRpZmljYXRlcyBhcmUgdXNlZCB0byBsaW5rIHRoZSBkb21haW4gY2VydGlmaWNhdGUgdG8gdGhlIHRydXN0ZWQgQ2VydGlmaWNhdGUgQXV0aG9yaXR5LiBUaGV5IHNob3VsZCBhbHNvIGJlIGluc3RhbGxlZCBvbiB0aGUgc2VydmVyIGZvciB0aGUgY2VydGlmaWNhdGUgdG8gYmUgcmVjb2duaXplZCBhcyB0cnVzdGVkIGluIGFsbCBicm93c2Vycy48L3A+DQoJCTxwPlR3byBvdGhlciBibG9ja3Mgb2YgQXV0aGVudGljYXRpb24gc2hvdyB1cyB0aGVzZSBJbnRlcm1lZGlhdGUgY2VydGlmaWNhdGVzIGFuZCB0aGUgcGF0aHMgdG8gdGhlbSBjb25zdHJ1Y3RlZCBkdXJpbmcgY2xpZW50LXNlcnZlciBpbnRlcmFjdGlvbi4gQSByb290IGNlcnRpZmljYXRlIGlzIHNlbGYtc2lnbmVkLCBtZWFuaW5nIGl0IGlzIG5vdCBzaWduZWQgYnkgYW5vdGhlciBlbnRpdHkgdGhhdCBoYXMgYmVlbiBnaXZlbiBhdXRob3JpdHkuIFRoZSByb290IGNlcnRpZmljYXRlIGdldHMgYXV0aG9yaXR5IHRocm91Z2ggdGhlIHJvb3QgY2VydGlmaWNhdGUgcHJvZ3JhbSBtYW5hZ2VkIGJ5IHRoZSBvcGVyYXRpbmcgc3lzdGVtIG9yIGJyb3dzZXIgZGV2ZWxvcGVyLiBBbGwgcm9vdCBjZXJ0aWZpY2F0ZXMgaXNzdWVkIGJ5IENBcyBhcmUga2VwdCBpbiB0aGUgdHJ1c3Qgc3RvcmVzIG9mIGJyb3dzZXJzLCBzbyB0aGVyZSBpcyBubyBuZWVkIHRvIGluc3RhbGwgYSByb290IFNTTCBvbiB0aGUgc2VydmVyLjwvcD4NCgkJPHA+SXQgc2hvdWxkIGJlIG5vdGVkIHRoYXQgaWYgYSByb290IFNTTCBpcyBpbnN0YWxsZWQgYW5kIHNlbnQgYnkgYSBzZXJ2ZXIsIGl0IHdpbGwgYmUgc2hvd24gd2l0aCB0aGlzIG1lc3NhZ2U6PC9wPg0KCQk8cD4NCgkJCQk8aW1nIGNsYXNzPSJrYi1pbWFnZSIgc3JjPSJodHRwczovL05hbWVjaGVhcC5zaW1wbGVrYi5jb20vU2l0ZUNvbnRlbnRzLzItN0MyMkQ1MjM2QTQ1NDNFQjgyN0YzQkQ4OTM2RTE1M0UvbWVkaWEvc3NsbGFiczIucG5nIiBhbHQ9InNzbGxhYnMyIiB3aWR0aD0iNzYwIiBoZWlnaHQ9IjMzMCIgYm9yZGVyPSIwIiAvPg0KCQk8L3A+DQoJCTxwPlNTTExhYnMgcmVmbGVjdHMgaXQgYXMg4oCYY2hhaW4gaXNzdWVz4oCZOjwvcD4NCgkJPHA+DQoJCQkJPGltZyBjbGFzcz0ia2ItaW1hZ2UiIHNyYz0iaHR0cHM6Ly9OYW1lY2hlYXAuc2ltcGxla2IuY29tL1NpdGVDb250ZW50cy8yLTdDMjJENTIzNkE0NTQzRUI4MjdGM0JEODkzNkUxNTNFL21lZGlhL3NzbGxhYnMzLnBuZyIgYWx0PSJzc2xsYWJzMyIgd2lkdGg9IjY4MyIgaGVpZ2h0PSI3NyIgYm9yZGVyPSIwIiAvPg0KCQk8L3A+DQoJCTxwPlRoaXMgaXMgbm90IGFuIGVycm9yLiBJdCBpbmNyZWFzZXMgbmV0d29yayBsYXRlbmN5IGR1cmluZyB0aGUgU1NMIGhhbmRzaGFrZSBhbmQgaXMgbm90IGNvbnNpZGVyZWQgYW4gaXNzdWUgYWNjb3JkaW5nIHRvIDxhIGhyZWY9Imh0dHBzOi8vd3d3LmlldGYub3JnL3JmYy9yZmM1MjQ2LnR4dCIgdGFyZ2V0PSJfYmxhbmsiPlJGQyA1MjQ2PC9hPi4gPC9wPg0KCQk8cD5TU0xMYWJzIGFsc28gY2hlY2tzIGlmIHRoZSBpbnRlcm1lZGlhdGUgY2VydGlmaWNhdGVzIGFyZSB2YWxpZCB1c2luZyBzZXZlcmFsIGtleSBwb2ludHM6IGV4cGlyYXRpb24gZGF0ZSwga2V5LCBpc3N1ZXIsIGFuZCBzaWduYXR1cmUgYWxnb3JpdGhtLiBTaW5jZSB0aGUgc2lnbmF0dXJlIG9uIGEgcm9vdCBjZXJ0aWZpY2F0ZSBpcyBub3QgdmVyaWZpZWQgKGFzIHRoZSBzb2Z0d2FyZSB0cnVzdHMgdGhlIHJvb3QgY2VydGlmaWNhdGUgcHVibGljIGtleSBkaXJlY3RseSksIHRoZXJlIGlzIG5vdGhpbmcgdG8gd29ycnkgYWJvdXQgaWYgYSByb290IFNTTCBpcyBpc3N1ZWQgaW4gU0hBLTEuIEEgc2VsZi1zaWduZWQgcm9vdCBTU0wgaXMgbWFya2VkIHdpdGggYSBncmVlbiA8aT7igJhJbiB0cnVzdCBzdG9yZeKAmTwvaT4gcGhyYXNlLCBib3RoIGluIDxpPuKAmEFkZGl0aW9uYWwgY2VydGlmaWNhdGVz4oCZPC9pPiBhbmQgPGk+4oCYQ2VydGlmaWNhdGlvbiBQYXRoc+KAmTwvaT4gYmxvY2tzOjwvcD4NCgkJPHA+DQoJCQkJPGltZyBjbGFzcz0ia2ItaW1hZ2UiIHNyYz0iaHR0cHM6Ly9OYW1lY2hlYXAuc2ltcGxla2IuY29tL1NpdGVDb250ZW50cy8yLTdDMjJENTIzNkE0NTQzRUI4MjdGM0JEODkzNkUxNTNFL21lZGlhL3NzbGxhYnM0LnBuZyIgYWx0PSJzc2xsYWJzNCIgd2lkdGg9IjYzOCIgaGVpZ2h0PSI4NyIgYm9yZGVyPSIwIiAvPg0KCQk8L3A+DQoJCTxwPlNvLCBpbiBvcmRlciB0byBwcm9jZWVkIHN1Y2Nlc3NmdWxseSB3aXRoIEF1dGhlbnRpY2F0aW9uLCBhIHZhbGlkIFNTTCBjZXJ0aWZpY2F0ZSB3aXRoIHRoZSByaWdodCBrZXkgc2l6ZSAoYXQgbGVhc3QgMjA0OC1iaXQgZm9yIFJTQSBhbmQgMjU2LWJpdCBmb3IgRUNEU0EpIGFuZCBhIFNIQS0yIGhhc2hpbmcgYWxnb3JpdGhtIGlzc3VlZCBieSBhIHRydXN0ZWQgQ2VydGlmaWNhdGUgQXV0aG9yaXR5IHNob3VsZCBiZSB1c2VkLiBBIGNvbXBsZXRlIENBIGJ1bmRsZSwgaW5jbHVkaW5nIGFsbCBpbnRlcm1lZGlhdGUgY2VydGlmaWNhdGVzLCBtdXN0IGJlIGluc3RhbGxlZCB0b28uPC9wPg0KCQk8cD4NCgkJCQk8Yj5Db25maWd1cmF0aW9uPC9iPg0KCQk8L3A+DQoJCTxwPlRoaXMgcGFydCBpbmNsdWRlcyB0aGUgZm9sbG93aW5nIHNlZ21lbnRzOiA8aT5Qcm90b2NvbHM8L2k+IHVzZWQgYnkgYSBzZXJ2ZXIgdG8gZXN0YWJsaXNoIHNlY3VyZSBjb25uZWN0aW9uOyBhdmFpbGFibGUgPGk+Q2lwaGVyIFN1aXRlczwvaT4sIGZyb20gd2hpY2ggYSBicm93c2VyIG9yIGNsaWVudCBzb2Z0d2FyZSBjYW4gc2VsZWN0IGF0IHRoZSBtb21lbnQgb2Ygc2Vzc2lvbiBzZXR1cDsgU1NMIDxpPkhhbmRzaGFrZSBTaW11bGF0aW9uPC9pPiB3aGljaCBzaG93cyBob3cgdGhlIGNvbm5lY3Rpb24gd291bGQgb2NjdXIgd2l0aCBkaWZmZXJlbnQgc29mdHdhcmUgYW5kIHdoaWNoIHByb3RvY29sIHZlcnNpb24sIGNpcGhlcnMsIGFuZCBlbmNyeXB0aW9uIGxldmVsIHdvdWxkIGJlIHVzZWQ7IDxpPk1pc2NlbGxhbmVvdXM8L2k+LCB3aGljaCBpbmNsdWRlcyBnZW5lcmFsIGluZm9ybWF0aW9uOyBhbmQgb25lIG9mIHRoZSBtb3N0IGltcG9ydGFudCBibG9ja3Mg4oCTIDxpPlByb3RvY29sIERldGFpbHM8L2k+LCBpbiB3aGljaCB3ZSBjYW4gc2VlIHNlY3VyaXR5IGZsYXdzIHRoYXQgc2hvdWxkIGJlIGZpeGVkIG9uIHNlcnZlciBzaWRlLjwvcD4NCgkJPHA+DQoJCQkJPGk+UHJvdG9jb2xzPC9pPg0KCQk8L3A+DQoJCTxwPlRoZXJlIGFyZSBmaXZlIGF2YWlsYWJsZSBwcm90b2NvbCB2ZXJzaW9ucyBmb3IgU1NMIGNvbm5lY3Rpb246IFNTTCAyLCBTU0wgMywgVExTIDEuMCwgVExTIDEuMSwgYW5kIFRMUyAxLjIuIEN1cnJlbnRseSwgVExTIDEuMiBpcyB0aGUgbGF0ZXN0IHZlcnNpb24gYW5kIGlzIGNvbnNpZGVyZWQgdGhlIG1vc3Qgc2VjdXJlIDxpPlRyYW5zcG9ydCBMYXllciBTZWN1cml0eSAoVExTKSBwcm90b2NvbCwgYWxsb3dpbmcgY2xpZW50L3NlcnZlciBhcHBsaWNhdGlvbnMgdG8gICBjb21tdW5pY2F0ZSBpbiBhIHdheSB0aGF0IGlzIGRlc2lnbmVkIHRvIHByZXZlbnQgZWF2ZXNkcm9wcGluZywgdGFtcGVyaW5nIG9yIG1lc3NhZ2UgZm9yZ2VyeTwvaT4uIFs8YSBocmVmPSJodHRwczovL3d3dy5pZXRmLm9yZy9yZmMvcmZjNTI0Ni50eHQiIHRhcmdldD0iX2JsYW5rIj5SRkMgNTI0NjwvYT5dLiA8L3A+DQoJCTxwPlNTTExhYnMgaGlnaGxpZ2h0cyBUTFMgMS4yIHdpdGggZ3JlZW46PC9wPg0KCQk8cD4NCgkJCQk8aW1nIGNsYXNzPSJrYi1pbWFnZSIgc3JjPSJodHRwczovL05hbWVjaGVhcC5zaW1wbGVrYi5jb20vU2l0ZUNvbnRlbnRzLzItN0MyMkQ1MjM2QTQ1NDNFQjgyN0YzQkQ4OTM2RTE1M0UvbWVkaWEvc3NsbGFiczUucG5nIiBhbHQ9InNzbGxhYnM1IiB3aWR0aD0iNjQ1IiBoZWlnaHQ9IjEzOCIgYm9yZGVyPSIwIiAvPg0KCQk8L3A+DQoJCTxwPk5hbWVjaGVhcCBzaGFyZWQgaG9zdGluZyBhY2NvdW50cyBhcmUgY29uZmlndXJlZCB0byBhY2NlcHQgYWxsIGNvbm5lY3Rpb25zIHVzaW5nIFRMUyB2ZXJzaW9ucyBvbmx5LiBJdCBpcyBiZXR0ZXIgdG8gaGF2ZSBhbGwgVExTIHZlcnNpb25zIGVuYWJsZWQgaW4gb3JkZXIgdG8gcHJldmVudCBjb21wYXRpYmlsaXR5IGlzc3VlcyB3aXRoIGxlZ2FjeSBzb2Z0d2FyZS9hcHBzLiBFbmFibGluZyBTU0x2MyB3aWxsIGFsbG93IGN1c3RvbWVycyB3aXRoIElFIDYgdG8gdmlzaXQgeW91ciB3ZWJzaXRlIG92ZXIgSFRUUFMgYnV0IHdpbGwgbWFrZSBhIHNlcnZlciB2dWxuZXJhYmxlIHRvIDxhIGhyZWY9Imh0dHBzOi8vcG9vZGxlLmlvLyIgdGFyZ2V0PSJfYmxhbmsiPlBPT0RMRSBhdHRhY2s8L2E+LiA8L3A+DQoJCTxwPkNpcGhlciBzdWl0ZXMgYXJlIGRpc3BsYXllZCBpbiBzZXJ2ZXItcHJlZmVycmVkIG9yZGVyIGZyb20gdGhlIHN0cm9uZ2VzdCB0byB3ZWFrZXN0IHRoYXQgYXJlIGF2YWlsYWJsZSBpbiBjbGllbnQtc2VydmVyIHNlY3VyZSBpbnRlcmFjdGlvbi4gTGV04oCZcyB0YWtlIGEgbG9vayB3aGF0IHRoZXNlIHN0cmluZ3MgY29uc2lzdCBvZjo8L3A+DQoJCTxwPg0KCQkJCTxpbWcgY2xhc3M9ImtiLWltYWdlIiBzcmM9Imh0dHBzOi8vTmFtZWNoZWFwLnNpbXBsZWtiLmNvbS9TaXRlQ29udGVudHMvMi03QzIyRDUyMzZBNDU0M0VCODI3RjNCRDg5MzZFMTUzRS9tZWRpYS9nZXRfYV9yYXRpbmdfMDcuanBnIiBhbHQ9ImdldF9hX3JhdGluZ18wNyIgd2lkdGg9Ijc0OSIgaGVpZ2h0PSIxNzkiIGJvcmRlcj0iMCIgLz4NCgkJPC9wPg0KCQk8cD5OYW1lY2hlYXAgb2ZmZXJzIG91ciBjdXN0b21lcnMgb25seSBzdHJvbmcgY2lwaGVyIHN1aXRlcyB3aXRoIGFsbCBvdXIgZnVsbHktbWFuYWdlZCBzZXJ2ZXJzLiBCZWxvdyBpcyB0aGUgZXhhbXBsZSBvZiB0aGUgY2lwaGVyIHN1aXRlIGZvciBzaGFyZWQgYW5kIHJlc2VsbGVyIGhvc3RpbmcgcGxhbnM6PC9wPg0KCQk8cD4NCgkJCQk8aW1nIGNsYXNzPSJrYi1pbWFnZSIgc3JjPSJodHRwczovL05hbWVjaGVhcC5zaW1wbGVrYi5jb20vU2l0ZUNvbnRlbnRzLzItN0MyMkQ1MjM2QTQ1NDNFQjgyN0YzQkQ4OTM2RTE1M0UvbWVkaWEvc3NsbGFiczcucG5nIiBhbHQ9InNzbGxhYnM3IiB3aWR0aD0iNjgwIiBoZWlnaHQ9IjQyNCIgYm9yZGVyPSIwIiAvPg0KCQk8L3A+DQoJCTxwPkN1c3RvbWVycyB3aXRoIHNlbGYtbWFuYWdlZCBWUFMgYW5kIGRlZGljYXRlZCBzZXJ2ZXJzIHNob3VsZCBtYW5hZ2UgY2lwaGVyIHN1aXRlcyB0aGVtc2VsdmVzLjwvcD4NCgkJPHA+U1NMIGhhbmRzaGFrZSBzaW11bGF0aW9uIGlzIGJlaW5nIGNhcnJpZWQgb3V0IHN1Y2Nlc3NmdWxseSB3aXRoIG1vc3QgY2xpZW50IHNvZnR3YXJlIGV4Y2VwdCBmb3IgY2xpZW50cyB3aGljaCBkbyBub3Qgc3VwcG9ydCA8YSBocmVmPSJodHRwczovL3d3dy5uYW1lY2hlYXAuY29tL3N1cHBvcnQva25vd2xlZGdlYmFzZS9hcnRpY2xlLmFzcHgvOTI1OSIgdGFyZ2V0PSJfYmxhbmsiPlNlcnZlciBOYW1lIEluZGljYXRpb24gKFNOSSk8L2E+LiBTaW5jZSBhbGwgTmFtZWNoZWFwIHNlcnZlcnMgaGF2ZSBTTkkgZW5hYmxlZCBieSBkZWZhdWx0LCBTU0wgY29ubmVjdGlvbiB3aXRoIEFuZHJvaWQgMi4zLjcsIEludGVybmV0IEV4cGxvcmVyIDYgYW5kIDggb24gV2luZG93cyBYUCwgIGFuZCBKYXZhIDZ1NDUgd2lsbCBmYWlsIHVubGVzcyB0aGUgdXNlciA8YSBocmVmPSJodHRwczovL3d3dy5uYW1lY2hlYXAuY29tL3N1cHBvcnQva25vd2xlZGdlYmFzZS9hcnRpY2xlLmFzcHgvODkvMjEvaG93LWRvLWktb3JkZXItYS1kZWRpY2F0ZWQtaXAiIHRhcmdldD0iX2JsYW5rIj5vcmRlcmVkIGEgZGVkaWNhdGVkIElQIGFkZHJlc3M8L2E+LjwvcD4NCgkJPHA+VGhlIGFmb3JlbWVudGlvbmVkIHZlcnNpb25zIG9mIEludGVybmV0IEV4cGxvcmVyIGFuZCBPcGVuU1NMIHBhY2thZ2UgMC45Ljh5IGRvIG5vdCBzdXBwb3J0IEZvcndhcmQgU2VjcmVjeSwgdGhpcyBzaG91bGQgYmUgYWRqdXN0ZWQgb24gc2VydmVyIGFzIHdlbGwuIFZpc2l0IG91ciBLbm93bGVkZ2ViYXNlIHRvIDxhIGhyZWY9Imh0dHBzOi8vd3d3Lm5hbWVjaGVhcC5jb20vc3VwcG9ydC9rbm93bGVkZ2ViYXNlL2FydGljbGUuYXNweC85NjUyLzM4L3BlcmZlY3QtZm9yd2FyZC1zZWNyZWN5LXdoYXQtaXQtaXMvIiB0YXJnZXQ9Il9ibGFuayI+bGVhcm4gbW9yZSBhYm91dCBQZXJmZWN0IEZvcndhcmQgU2VjcmVjeTwvYT4gYW5kIDxhIGhyZWY9Imh0dHBzOi8vd3d3Lm5hbWVjaGVhcC5jb20vc3VwcG9ydC9rbm93bGVkZ2ViYXNlL2FydGljbGUuYXNweC85NjUzLzM4L2hvdy10by1jaGVjay13aGV0aGVyLXRoZS1zZXJ2ZXItc3VwcG9ydHMtZm9yd2FyZC1zZWNyZWN5LyIgdGFyZ2V0PSJfYmxhbmsiPmhvdyB0byBjaGVjayB3aGV0aGVyIGEgc2VydmVyIHByb3ZpZGVzIGl0PC9hPi4gRm9yIGN1c3RvbWVycyB3aXRoIHRoaXJkLXBhcnR5IGhvc3Rpbmcgc2VydmVycywgaW5zdHJ1Y3Rpb25zIGZvciBkZXBsb3lpbmcgRlMgY2FuIGJlIGZvdW5kIDxhIGhyZWY9Imh0dHBzOi8vY29tbXVuaXR5LnF1YWx5cy5jb20vYmxvZ3Mvc2VjdXJpdHlsYWJzLzIwMTMvMDYvMjUvc3NsLWxhYnMtZGVwbG95aW5nLWZvcndhcmQtc2VjcmVjeSIgdGFyZ2V0PSJfYmxhbmsiPmhlcmU8L2E+IGFuZCA8YSBocmVmPSJodHRwczovL2NvbW11bml0eS5xdWFseXMuY29tL2Jsb2dzL3NlY3VyaXR5bGFicy8yMDEzLzA4LzA1L2NvbmZpZ3VyaW5nLWFwYWNoZS1uZ2lueC1hbmQtb3BlbnNzbC1mb3ItZm9yd2FyZC1zZWNyZWN5IiB0YXJnZXQ9Il9ibGFuayI+aGVyZTwvYT4uIFNlcnZlcnMgYmFzZWQgaW4gTmFtZWNoZWFwIGRhdGFjZW50ZXJzIGhhdmUgdGhlIEZTIGZlYXR1cmUgZW5hYmxlZCB3aXRoIG1vZGVybiB2ZXJzaW9ucyBvZiBicm93c2VycyBvbiBtb3N0IG9mIHRoZW0uPC9wPg0KCQk8cD4NCgkJCQk8aW1nIGNsYXNzPSJrYi1pbWFnZSIgc3JjPSJodHRwczovL05hbWVjaGVhcC5zaW1wbGVrYi5jb20vU2l0ZUNvbnRlbnRzLzItN0MyMkQ1MjM2QTQ1NDNFQjgyN0YzQkQ4OTM2RTE1M0UvbWVkaWEvc3NsbGFiczgucG5nIiBhbHQ9InNzbGxhYnM4IiB3aWR0aD0iNjcyIiBoZWlnaHQ9IjkyIiBib3JkZXI9IjAiIC8+DQoJCTwvcD4NCgkJPHA+RmluYWxseSwgd2UgY29tZSB0byA8aT5Qcm90b2NvbCBEZXRhaWxzPC9pPiwgcGVyaGFwcyB0aGUgbW9zdCBpbnRlcmVzdGluZyBhbmQgaW1wb3J0YW50IHNlZ21lbnQuIEN1c3RvbWVycyB3aG8gdXNlIE5hbWVjaGVhcOKAmXMgZnVsbHktbWFuYWdlZCBob3N0aW5nIHBsYW5zIGRvbuKAmXQgaGF2ZSB0byB3b3JyeSBhYm91dCBzZXJ2ZXIgY29uZmlndXJhdGlvbnMgc2luY2Ugb3VyIFRlY2huaWNhbCBUZWFtIGtlZXBzIHRoZW0gdXAtdG8tZGF0ZSwgdHJhY2tzIGFsbCBhbm5vdW5jZWQgd2Vha25lc3NlcywgYW5kIGltbWVkaWF0ZWx5IGRlcGxveXMgZml4ZXMgZm9yIHRoZW0uIEFuIOKAmEHigJkgZ3JhZGUgc2hvdWxkIGJlIHNob3duIGJ5IGRlZmF1bHQgd2hlbiBhIHZhbGlkIFNTTCBjZXJ0aWZpY2F0ZSB3aXRoIGFsbCBJbnRlcm1lZGlhdGUgQ0EgY2VydGlmaWNhdGVzIGlzIGluc3RhbGxlZC48L3A+DQoJCTxwPlRoZSBjb3ZldGVkIOKAnEEr4oCdIGdyYWRlIG9uIFNTTExhYnMgY2FuIGJlIGFjaGlldmVkIGJ5IGVuYWJsaW5nIG9mIEhTVFMgcG9saWN5IG9uIGEgc2VydmVyLiBIU1RTIHRlY2huaXF1ZSBpcyBleHBsYWluZWQgPGEgaHJlZj0iaHR0cHM6Ly93d3cubmFtZWNoZWFwLmNvbS9zdXBwb3J0L2tub3dsZWRnZWJhc2UvYXJ0aWNsZS5hc3B4Lzk3MTIvNjkvaHR0cC1zdHJpY3QtdHJhbnNwb3J0LXNlY3VyaXR5IiB0YXJnZXQ9Il9ibGFuayI+aGVyZTwvYT4uIEluIGEgbnV0c2hlbGwsIEhTVFMgaXMgYSA8aT5tZWNoYW5pc20gZW5hYmxpbmcgd2ViIHNpdGVzIHRvIGRlY2xhcmUgdGhlbXNlbHZlcyBhY2Nlc3NpYmxlIG9ubHkgdmlhIHNlY3VyZSBjb25uZWN0aW9ucywgYW5kL29yIGZvciB1c2VycyB0byBiZSBhYmxlIHRvIGRpcmVjdCB0aGVpciB1c2VyIGFnZW50KHMpIHRvIGludGVyYWN0IHdpdGggZ2l2ZW4gc2l0ZXMgb25seSBvdmVyIHNlY3VyZSBjb25uZWN0aW9uczwvaT4gYXMgaW5kaWNhdGVkIGluIDxhIGhyZWY9Imh0dHBzOi8vdG9vbHMuaWV0Zi5vcmcvaHRtbC9yZmM2Nzk3IiB0YXJnZXQ9Il9ibGFuayI+UkZDIDY3OTc8L2E+LjwvcD4NCgkJPHA+QWNjb3JkaW5nbHksIGEgc2VydmVyIGNhbiBzZW5kIGEgc3BlY2lhbCBoZWFkZXIgaW4gSFRUUFMgcmVxdWVzdCB0byBjbGllbnQgc29mdHdhcmUgYXNraW5nIHRvIHVzZSBmb3JjZWQgc2VjdXJlIGNvbm5lY3Rpb24uIE9uY2UgSFNUUyBwb2xpY3kgaXMgZW5hYmxlZCwgeW91IHdpbGwgc2VlIHRoYXQgbXVjaC1kZXNpcmVkIG1lc3NhZ2U6PC9wPg0KCQk8cD4NCgkJCQk8aW1nIGNsYXNzPSJrYi1pbWFnZSIgc3JjPSJodHRwczovL05hbWVjaGVhcC5zaW1wbGVrYi5jb20vU2l0ZUNvbnRlbnRzLzItN0MyMkQ1MjM2QTQ1NDNFQjgyN0YzQkQ4OTM2RTE1M0UvbWVkaWEvc3NsbGFiczkucG5nIiBhbHQ9InNzbGxhYnM5IiB3aWR0aD0iODE1IiBoZWlnaHQ9IjM4MCIgYm9yZGVyPSIwIiAvPg0KCQk8L3A+DQoJCTxwPlRMUyBvbmx5IHByb3RvY29sIHZlcnNpb25zLCBtb2Rlcm4gY2lwaGVyIHN1aXRlcywgYW5kIG1pdGlnYXRpb25zIGZvciBhbGwga25vd24gU1NMIHZ1bG5lcmFiaWxpdGllcyBtdXN0IGJlIGFwcGxpZWQgY2FyZWZ1bGx5IHRvIHBhc3MgQ29uZmlndXJhdGlvbiBibG9jayBjaGVja2luZyBzdWNjZXNzZnVsbHkuPC9wPg0KCQk8cD5TbywgbGV04oCZcyBzdW1tYXJpemUgd2hhdCB3ZeKAmXZlIGxlYXJuZWQ6IFNpbmNlIE5hbWVjaGVhcOKAmXMgZnVsbHktbWFuYWdlZCBob3N0aW5nIHNlcnZlcnMgaGF2ZSBhbGwgdGhlIG5lY2Vzc2FyeSBzZXR0aW5ncyBwcmUtY29uZmlndXJlZCwgYWxsIG91ciBjdXN0b21lcnMgbmVlZCB0byBkbyB0byBnZXQgYW4g4oCYQSvigJkgZ3JhZGUgb24gU1NMTGFicyBpcyB0byBpbnN0YWxsIGEgdmFsaWQgU1NMIGNlcnRpZmljYXRlIHdpdGggQ0EgYnVuZGxlIGFuZCBjb25maWd1cmUgSFNUUyBpbiA8Y29kZT4uaHRhY2Nlc3M8L2NvZGU+LjwvcD4NCgkJPHA+U2V2ZXJhbCBrZXkgcG9pbnRzIHN0aWxsIHNob3VsZCBiZSBtZW50aW9uZWQgZm9yIGN1c3RvbWVycyB3aXRoIHRoaXJkLXBhcnR5IGhvc3Rpbmcgc2VydmVycywgaG93ZXZlci4gSW4gb3JkZXIgdG8gc2V0IGdvb2Qgc2VydmVyIGNvbmZpZ3VyYXRpb24sIHlvdeKAmWxsIG5lZWQgdG8gZG8gYSBmZXcgdGhpbmdzOjwvcD4NCgkJPHVsPg0KCQkJCTxsaT5EaXNhYmxlIGJvdGggU1NMdjIgYW5kIFNTTHYzIHdoaWNoIGFyZSB2dWxuZXJhYmxlIHRvIDxhIGhyZWY9Imh0dHBzOi8vd3d3LnNjaG5laWVyLmNvbS9wYXBlci1zc2wucGRmIiB0YXJnZXQ9Il9ibGFuayI+Q2lwaGVyc3VpdGUgcm9sbGJhY2sgYXR0YWNrPC9hPiBhbmQgPGEgaHJlZj0iaHR0cHM6Ly9wb29kbGUuaW8vIiB0YXJnZXQ9Il9ibGFuayI+UE9PRExFPC9hPi48L2xpPg0KCQkJCTxsaT5EaXNhYmxlIFRMUyAxLjAgY29tcHJlc3Npb24gd2hpY2ggaXMgdnVsbmVyYWJsZSB0byA8YSBocmVmPSJodHRwOi8vc2VjdXJpdHkuc3RhY2tleGNoYW5nZS5jb20vcXVlc3Rpb25zLzE5OTExL2NyaW1lLWhvdy10by1iZWF0LXRoZS1iZWFzdC1zdWNjZXNzb3IvMTk5MTQjMTk5MTQiIHRhcmdldD0iX2JsYW5rIj5DUklNRTwvYT4uPC9saT4NCgkJCQk8bGk+RGlzYWJsZSB3ZWFrIGNpcGhlcnMgKERFUyBhbmQgZXNwZWNpYWxseSA8YSBocmVmPSJodHRwczovL2NvbW11bml0eS5xdWFseXMuY29tL2Jsb2dzL3NlY3VyaXR5bGFicy8yMDEzLzAzLzE5L3JjNC1pbi10bHMtaXMtYnJva2VuLW5vdy13aGF0IiB0YXJnZXQ9Il9ibGFuayI+UkM0PC9hPiksIHByZWZlciBtb2Rlcm4gY2lwaGVycyAoPGEgaHJlZj0iaHR0cHM6Ly9lbi53aWtpcGVkaWEub3JnL3dpa2kvQWR2YW5jZWRfRW5jcnlwdGlvbl9TdGFuZGFyZCIgdGFyZ2V0PSJfYmxhbmsiPkFFUzwvYT4pLCBtb2Rlcm4gbW9kZXMgb2Ygb3BlcmF0aW9uICg8YSBocmVmPSJodHRwczovL2VuLndpa2lwZWRpYS5vcmcvd2lraS9HYWxvaXMvQ291bnRlcl9Nb2RlIiB0YXJnZXQ9Il9ibGFuayI+R0NNPC9hPikgYW5kIHByb3RvY29scyAoPGEgaHJlZj0iaHR0cHM6Ly9lbi53aWtpcGVkaWEub3JnL3dpa2kvVHJhbnNwb3J0X0xheWVyX1NlY3VyaXR5I1RMU18xLjIiIHRhcmdldD0iX2JsYW5rIj5UTFMgMS4yPC9hPikuPC9saT4NCgkJCQk8bGk+RGlzYWJsZSBFeHBvcnQgY2lwaGVyIHN1aXRlcyB2dWxuZXJhYmxlIHRvIDxhIGhyZWY9Imh0dHBzOi8vZnJlYWthdHRhY2suY29tLyIgdGFyZ2V0PSJfYmxhbmsiPkZSRUFLIGF0dGFjazwvYT4uPC9saT4NCgkJCQk8bGk+RGVwbG95IEVsbGlwdGljLUN1cnZlIERpZmZpZS1IZWxsbWFuIGtleSBleGNoYW5nZSBtZWNoYW5pc20gYW5kIHVzZSBzdHJvbmcgREggZ3JvdXAgd2hpY2ggYWxsb3cgcHJldmVudGluZyBuZXcgPGEgaHJlZj0iaHR0cHM6Ly93ZWFrZGgub3JnLyIgdGFyZ2V0PSJfYmxhbmsiPkxvZ2phbSBhdHRhY2s8L2E+LjwvbGk+DQoJCQkJPHA+VGhhdOKAmXMgYWxsISBXZSB3aXNoIHlvdSBnb29kIGx1Y2sgYW5kIHNlY3VyaXR5IGluIHlvdXIgYnVzaW5lc3MuPC9wPg0KCQk8L3VsPg0K","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"2024-03-27T13:50:27.0000000","LiveDateTime":"1754-02-02T00:00:00.0000000","CreatedDateTime":"2016-04-28T07:38:38.0000000","ApprovalDatetime":"2016-04-29T06:53:01.0000000","RequestCount":44216,"MarkedAsNew":false,"MarkedAsFeatured":false,"RatingValue":3,"CategoryPaths":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryPathDto","Level":1,"CategoryId":14,"CategoryName":"SSL Certificates"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryPathDto","Level":2,"CategoryId":38,"CategoryName":"SSL General"}],"AssociatedCategories":[{"CategoryId":38,"CategoryName":"SSL General","CategoryDisplayName":"SSL CertificatesSSL General"}],"AssociatedTags":[],"RelatedArticles":[],"AssociatedMedias":[],"PreferredCategoryId":0,"RootParentCategoryName":"","RootParentCategoryId":0},"status":200,"statusText":"OK"},"/api/v1/ncpl/simplekb/getcategorybycategoryid:\"{\\\"categoryId\\\":38}\"":{"body":{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryDto","Description":"QmFzaWMgaW5mb3JtYXRpb24gb24gU1NMIGNlcnRpZmljYXRlcw==","ParentCategoryId":14,"Parent_Category_Name":"SSL Certificates","FriendlyId":null,"ApprovedYN":true,"TreatAsTopicYN":false,"CreatedDateTime":"07/25/2008 16:58:37","CurrentCategoryPaths":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryPathDto","Level":1,"CategoryId":14,"CategoryName":"SSL Certificates"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryPathDto","Level":2,"CategoryId":38,"CategoryName":"SSL General"}],"RelatedCategories":[],"AssociatedArticles":[{"ArticleId":9503,"Title":"What is an ECC (Elliptic Curve Cryptography) certificate?","ArticleName":"What is an ECC (Elliptic Curve Cryptography) certificate?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/23/2019"},{"ArticleId":9504,"Title":"How do I get an ECC certificate via Namecheap?","ArticleName":"How do I get an ECC certificate via Namecheap?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"02/06/2025"},{"ArticleId":9507,"Title":"Why an EV certificate is better for an ecommerce website than a Domain Validation one?","ArticleName":"Why an EV certificate is better for an ecommerce website than a Domain Validation one?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"07/24/2020"},{"ArticleId":9508,"Title":"What is the difference between very high, high, medium and low assurance certificates?","ArticleName":"What is the difference between very high, high, medium and low assurance certificates?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"02/15/2024"},{"ArticleId":9509,"Title":"Your site shows 256-bit encryption and my site shows 128-bit, why?","ArticleName":"Your site shows 256-bit encryption and my site shows 128-bit, why?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"08/27/2019"},{"ArticleId":9511,"Title":"How 2–5-year SSL certificates work","ArticleName":"How 2–5-year SSL certificates work","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":"03/14/2015 04:00:00","FeaturedTillDate":"03/09/2015 04:00:00","ModifiedDateTime":"04/15/2024"},{"ArticleId":9588,"Title":"What is Certificate Transparency?","ArticleName":"What is Certificate Transparency?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"02/06/2025"},{"ArticleId":9595,"Title":"HTTP to HTTPS redirection on IIS","ArticleName":"HTTP to HTTPS redirection on IIS","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"10/25/2019"},{"ArticleId":9596,"Title":"HTTP Strict Transport Security (HSTS)","ArticleName":"HTTP Strict Transport Security (HSTS)","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"11/08/2023"},{"ArticleId":9597,"Title":"HTTP Public Key Pinning (HPKP)","ArticleName":"HTTP Public Key Pinning (HPKP)","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"03/06/2024"},{"ArticleId":9598,"Title":"Disabling SSLv3","ArticleName":"Disabling SSLv3","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"11/08/2023"},{"ArticleId":9599,"Title":"Disabling RC4","ArticleName":"Disabling RC4","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"11/08/2023"},{"ArticleId":9600,"Title":"Disabling SHA-1","ArticleName":"Disabling SHA-1","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"03/27/2024"},{"ArticleId":9601,"Title":"Cipher Suites Configuration and forcing Perfect Forward Secrecy on Windows","ArticleName":"Cipher Suites Configuration and forcing Perfect Forward Secrecy on Windows","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"03/17/2021"},{"ArticleId":9602,"Title":"OCSP Stapling","ArticleName":"OCSP Stapling","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"11/08/2023"},{"ArticleId":9650,"Title":"I can see SHA-1 fingerprint/thumbprint on my certificate. Is my certificate actually SHA-2?","ArticleName":"I can see SHA-1 fingerprint/thumbprint on my certificate. Is my certificate actually SHA-2?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/23/2019"},{"ArticleId":9652,"Title":"Perfect Forward Secrecy. What it is?","ArticleName":"Perfect Forward Secrecy. What it is?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/07/2022"},{"ArticleId":9653,"Title":"How to check whether the server supports Forward Secrecy","ArticleName":"How to check whether the server supports Forward Secrecy","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"06/22/2023"},{"ArticleId":9682,"Title":"How to push SSL certificates from one Namecheap account to another one","ArticleName":"How to push SSL certificates from one Namecheap account to another one","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"02/06/2025"},{"ArticleId":9707,"Title":"HSTS: General information","ArticleName":"HSTS: General information","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/24/2019"},{"ArticleId":9708,"Title":"Prerequisites for Namecheap Shared hosting to enable HSTS","ArticleName":"Prerequisites for Namecheap Shared hosting to enable HSTS","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/24/2019"},{"ArticleId":9709,"Title":"How to enable HSTS on Namecheap shared hosts","ArticleName":"How to enable HSTS on Namecheap shared hosts","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"11/10/2023"},{"ArticleId":9710,"Title":"How to enable HSTS on third-party servers","ArticleName":"How to enable HSTS on third-party servers","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"11/08/2023"},{"ArticleId":9711,"Title":"How to check if HSTS is enabled","ArticleName":"How to check if HSTS is enabled","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/24/2019"},{"ArticleId":9727,"Title":"What is SSL certificate encryption strength?","ArticleName":"What is SSL certificate encryption strength?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/24/2019"},{"ArticleId":9752,"Title":"How do I get A+ rating in SSLLabs?","ArticleName":"How do I get A+ rating in SSLLabs?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"03/27/2024"},{"ArticleId":9770,"Title":"How to use .htaccess to redirect to https in cPanel","ArticleName":"How to use .htaccess to redirect to https in cPanel","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"11/10/2023"},{"ArticleId":9782,"Title":"Security tips for business","ArticleName":"Security tips for business","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"05/12/2021"},{"ArticleId":9783,"Title":"1024 bit certificates","ArticleName":"1024 bit certificates","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/13/2022"},{"ArticleId":9800,"Title":"Advantages of having an SSL certificate","ArticleName":"Advantages of having an SSL certificate","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/07/2023"},{"ArticleId":9805,"Title":"Setting HTTPS redirect on a Nginx web-server","ArticleName":"Setting HTTPS redirect on a Nginx web-server","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/24/2019"},{"ArticleId":9821,"Title":"Apache Redirect to HTTPS","ArticleName":"Apache Redirect to HTTPS","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"06/19/2020"},{"ArticleId":9952,"Title":"Supported key sizes and signature algorithms in CSRs","ArticleName":"Supported key sizes and signature algorithms in CSRs","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":"12/05/2017 05:00:00","ModifiedDateTime":"07/27/2023"},{"ArticleId":9953,"Title":"IIS Redirect HTTP to HTTPS","ArticleName":"IIS Redirect HTTP to HTTPS","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":"11/28/2017 05:00:00","ModifiedDateTime":"12/06/2022"},{"ArticleId":9968,"Title":"How to check the certificate revocation status","ArticleName":"How to check the certificate revocation status","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":"01/26/2018 05:00:00","ModifiedDateTime":"09/24/2019"},{"ArticleId":9969,"Title":"HPKP pinning","ArticleName":"HPKP pinning","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"03/06/2024"},{"ArticleId":9991,"Title":"CAA Record and why it is needed (SSL related)","ArticleName":"CAA Record and why it is needed (SSL related)","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":"04/30/2018 04:00:00","ModifiedDateTime":"09/07/2022"},{"ArticleId":10081,"Title":"Comodo CA rebrands as Sectigo","ArticleName":"Comodo CA rebrands as Sectigo","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"01/25/2019"},{"ArticleId":10100,"Title":"Cipher Suites Configuration for Apache, Nginx","ArticleName":"Cipher Suites Configuration for Apache, Nginx","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/07/2022"},{"ArticleId":10503,"Title":"How to remove an SSL from a Namecheap account","ArticleName":"How to remove an SSL from a Namecheap account","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"03/11/2025"},{"ArticleId":10504,"Title":"What is AutoSSL and how to use it?","ArticleName":"What is AutoSSL and how to use it?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"03/18/2025"},{"ArticleId":10557,"Title":"Decoder.link user guide","ArticleName":"Decoder.link user guide","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/15/2025"},{"ArticleId":10595,"Title":"Understanding How SSL Encryption Works","ArticleName":"Understanding How SSL Encryption Works","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"04/05/2023"},{"ArticleId":10597,"Title":"What is SSL and TLS","ArticleName":"What is SSL and TLS","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/07/2023"},{"ArticleId":10747,"Title":"What is MPIC (Multi-Perspective Issuance Corroboration)","ArticleName":"What is MPIC (Multi-Perspective Issuance Corroboration)","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/15/2025"},{"ArticleId":9293,"Title":"I need to secure some of the subdomains of my domain name","ArticleName":"I need to secure some of the subdomains of my domain name","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/24/2019"},{"ArticleId":9294,"Title":"I need to secure two, three or more domain names with the same certificate","ArticleName":"I need to secure two, three or more domain names with the same certificate","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"03/17/2021"},{"ArticleId":9464,"Title":"Can I download an issued certificate on your site?","ArticleName":"Can I download an issued certificate on your site?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"11/12/2024"},{"ArticleId":786,"Title":"What is an SSL certificate and what is it used for?","ArticleName":"What is an SSL certificate and what is it used for?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"07/24/2023"},{"ArticleId":334,"Title":"What is Certificate Authority (CA)?","ArticleName":"What is Certificate Authority (CA)?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/24/2019"},{"ArticleId":9415,"Title":"SSL certificate migration from the SHA-1 to SHA-2 algorithm","ArticleName":"SSL certificate migration from the SHA-1 to SHA-2 algorithm","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"03/27/2024"},{"ArticleId":9467,"Title":"How do I check my hashing algorithm?","ArticleName":"How do I check my hashing algorithm?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"03/27/2024"},{"ArticleId":9484,"Title":"I want to test your service do you have trial certificates?","ArticleName":"I want to test your service do you have trial certificates?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"04/28/2025"},{"ArticleId":789,"Title":"Can I use a single SSL certificate for multiple subdomains?","ArticleName":"Can I use a single SSL certificate for multiple subdomains?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"03/17/2021"},{"ArticleId":787,"Title":"How to inform your clients that you use SSL","ArticleName":"How to inform your clients that you use SSL","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/07/2023"},{"ArticleId":464,"Title":"What is a wildcard certificate?","ArticleName":"What is a wildcard certificate?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"05/07/2024"},{"ArticleId":790,"Title":"Types of certificates offered at Namecheap","ArticleName":"Types of certificates offered at Namecheap","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"10/01/2019"},{"ArticleId":9469,"Title":"Are your certificates private or shared? What is the difference?","ArticleName":"Are your certificates private or shared? What is the difference?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"10/26/2015"},{"ArticleId":9466,"Title":"Can I get a certificate if I use an online web-hosting (Wix, Weebly, Tumblr, etc.)?","ArticleName":"Can I get a certificate if I use an online web-hosting (Wix, Weebly, Tumblr, etc.)?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"01/20/2021"},{"ArticleId":9473,"Title":"Can I use your SSL certificates for FTP and SQL?","ArticleName":"Can I use your SSL certificates for FTP and SQL?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"11/22/2018"},{"ArticleId":9481,"Title":"I have a certificate at another vendor; will there be an issue, if I activate one with you for the same common name?","ArticleName":"I have a certificate at another vendor; will there be an issue, if I activate one with you for the same common name?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"10/26/2015"},{"ArticleId":982,"Title":"Domain Validated certificates","ArticleName":"Domain Validated certificates","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"03/17/2021"},{"ArticleId":886,"Title":"Chained and single Root certificates","ArticleName":"Chained and single Root certificates","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"03/17/2021"},{"ArticleId":885,"Title":"SSL certificate warranty","ArticleName":"SSL certificate warranty","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"03/17/2021"}],"AssociatedTags":[],"CategoryId":38,"CategoryName":"SSL General"},"status":200,"statusText":"OK"},"/api/v1/ncpl/simplekb/getcategories:\"{\\\"parentCategoryId\\\":0,\\\"getTree\\\":true}\"":{"body":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2216,"CategoryName":"Spam Protection"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2217,"CategoryName":"Renewal"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2218,"CategoryName":"cPanel SSL Plugin"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2219,"CategoryName":"PHP Configuration"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2221,"CategoryName":"Multi-Domain SSL Certificates"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2222,"CategoryName":"Cancellation"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2223,"CategoryName":"Browser errors"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2224,"CategoryName":"Site Seal, Logo"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2225,"CategoryName":"SEO"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2226,"CategoryName":"Email Migration"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2211,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2227,"CategoryName":"SSL Resellers"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":true,"Description":"","ImageUrl":"/assets/img/pictograms/150/cloud-red.png","ShortDesc":"","CategoryId":2228,"CategoryName":"Apps","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2228,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2251,"CategoryName":"Supersonic CDN"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2228,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2298,"CategoryName":"Site Maker"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2228,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":177,"CategoryName":"Google Workspace (formerly G Suite)"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2211,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2229,"CategoryName":"Hosting Resellers"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2232,"CategoryName":"DNSSEC"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2234,"CategoryName":"Google Workspace (formerly G Suite)"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2237,"CategoryName":"Host records setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2238,"CategoryName":"SSL installation errors"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/easywp-red.png","ShortDesc":"","CategoryId":2239,"CategoryName":"EasyWP","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2280,"CategoryName":"Getting Started"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2279,"CategoryName":"General Information"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2281,"CategoryName":"WordPress Migration"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2282,"CategoryName":"Plugins and Themes"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2284,"CategoryName":"WordPress Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2285,"CategoryName":"SFTP and Database access"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2286,"CategoryName":"Domains questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2288,"CategoryName":"Billing questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2287,"CategoryName":"SSL questions"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2228,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2251,"CategoryName":"Supersonic CDN"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2252,"CategoryName":"InterWorx questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2253,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2254,"CategoryName":"Domains How-To"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2253,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2255,"CategoryName":"Hosting How-To"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2253,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2257,"CategoryName":"Sales & Payments How-To"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2253,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2258,"CategoryName":"cPanel Email How-To"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2260,"CategoryName":"Private Email Contacts and Calendars Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2253,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2262,"CategoryName":"EasyWP How-To"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"https://download.namecheap.com/assets/img/domainvault-red@2x.png","ShortDesc":"","CategoryId":2289,"CategoryName":"Domain Vault","SubCategories":[]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2290,"CategoryName":"CSR code"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2291,"CategoryName":"Webuzo questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2292,"CategoryName":"Browser Extensions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2293,"CategoryName":"Automated SSL management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2228,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2298,"CategoryName":"Site Maker"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":27,"CategoryName":"Getting Started"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/support-red.png","ShortDesc":"","CategoryId":5,"CategoryName":"General & Support","SubCategories":[]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":7,"CategoryName":"Billing FAQ"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2209,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":8,"CategoryName":"Transfer Information"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":22,"CategoryName":"Hosting Information"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":38,"CategoryName":"SSL General"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":9,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":45,"CategoryName":"Account Security"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":46,"CategoryName":"Domain Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2211,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":63,"CategoryName":"Namecheap API"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2228,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":177,"CategoryName":"Google Workspace (formerly G Suite)"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2179,"CategoryName":"Private Email: General Information"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2274,"CategoryName":"General"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2280,"CategoryName":"Getting Started"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2279,"CategoryName":"General Information"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2215,"CategoryName":"Private Email: Mailbox Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2211,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2196,"CategoryName":"WHMCS module for SSL"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/savings-red.png","ShortDesc":"","CategoryId":2200,"CategoryName":"Checkout & Billing","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":7,"CategoryName":"Billing FAQ"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2201,"CategoryName":"Domains Billing"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":21,"CategoryName":"Hosting Billing"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":71,"CategoryName":"SSL Certificates Billing"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2177,"CategoryName":"Private Email"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2201,"CategoryName":"Domains Billing"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":67,"CategoryName":"Activation"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2209,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":83,"CategoryName":"Transfer to Namecheap"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":9,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":43,"CategoryName":"Profile Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":10,"CategoryName":"DNS Questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":29,"CategoryName":"cPanel questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":21,"CategoryName":"Hosting Billing"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":11,"CategoryName":"Dynamic DNS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":9,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":44,"CategoryName":"Account Access"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2209,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":84,"CategoryName":"Transfer to another provider"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":68,"CategoryName":"Validation"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2182,"CategoryName":"cPanel: Software Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2214,"CategoryName":"Email Forwarding"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2270,"CategoryName":"Routers"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2281,"CategoryName":"WordPress Migration"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2282,"CategoryName":"Plugins and Themes"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2272,"CategoryName":"TV"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2187,"CategoryName":"cPanel: WordPress"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2209,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":219,"CategoryName":"Canceled Transfers"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":71,"CategoryName":"SSL Certificates Billing"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2176,"CategoryName":"Private Email: DNS Settings"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":69,"CategoryName":"Installation"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/reseller-red.png","ShortDesc":"","CategoryId":34,"CategoryName":"Domains","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2232,"CategoryName":"DNSSEC"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2234,"CategoryName":"Google Workspace (formerly G Suite)"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2237,"CategoryName":"Host records setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":46,"CategoryName":"Domain Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":10,"CategoryName":"DNS Questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":11,"CategoryName":"Dynamic DNS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":35,"CategoryName":"Registrations"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2207,"CategoryName":"Renewal questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":36,"CategoryName":"Domains with extended attributes"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":51,"CategoryName":"FreeDNS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":15,"CategoryName":"Namecheap Market"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2208,"CategoryName":"3rd Party Services Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2278,"CategoryName":"Handshake TLDs"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":35,"CategoryName":"Registrations"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":70,"CategoryName":"Reissuance"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/protection-red.png","ShortDesc":"","CategoryId":37,"CategoryName":"Domain Privacy Protection","SubCategories":[]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2177,"CategoryName":"Private Email"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2178,"CategoryName":"Private Email: Webmail Features"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2207,"CategoryName":"Renewal questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2210,"CategoryName":"cPanel Add-ons"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2273,"CategoryName":"Gaming Consoles"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2284,"CategoryName":"WordPress Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2285,"CategoryName":"SFTP and Database access"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2268,"CategoryName":"macOS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2175,"CategoryName":"Private Email: Client Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/status-red.png","ShortDesc":"","CategoryId":2209,"CategoryName":"Domain Transfers","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2209,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":8,"CategoryName":"Transfer Information"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2209,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":83,"CategoryName":"Transfer to Namecheap"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2209,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":84,"CategoryName":"Transfer to another provider"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2209,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":219,"CategoryName":"Canceled Transfers"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":48,"CategoryName":"VPS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":36,"CategoryName":"Domains with extended attributes"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":true,"Description":"","ImageUrl":"/assets/img/pictograms/150/server-red.png","ShortDesc":"","CategoryId":12,"CategoryName":"Hosting","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2219,"CategoryName":"PHP Configuration"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2225,"CategoryName":"SEO"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2252,"CategoryName":"InterWorx questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2291,"CategoryName":"Webuzo questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":27,"CategoryName":"Getting Started"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":22,"CategoryName":"Hosting Information"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":29,"CategoryName":"cPanel questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2182,"CategoryName":"cPanel: Software Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2187,"CategoryName":"cPanel: WordPress"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2210,"CategoryName":"cPanel Add-ons"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":48,"CategoryName":"VPS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2188,"CategoryName":"Dedicated Server"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":30,"CategoryName":"WHM questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":32,"CategoryName":"DNS settings"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":103,"CategoryName":"LVE (CloudLinux)"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":89,"CategoryName":"SSH Access"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":205,"CategoryName":"FTP questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2180,"CategoryName":"MySQL questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2199,"CategoryName":"Hosting Migration"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2194,"CategoryName":"Tips & Tricks"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":239,"CategoryName":"WHMCS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":33,"CategoryName":"SSL Installation"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2171,"CategoryName":"Private Email: Active Sync (Exchange) Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2188,"CategoryName":"Dedicated Server"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2269,"CategoryName":"iOS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2286,"CategoryName":"Domains questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2288,"CategoryName":"Billing questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2271,"CategoryName":"Linux"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":30,"CategoryName":"WHM questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":31,"CategoryName":"cPanel Email FAQs"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":51,"CategoryName":"FreeDNS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/email-red.png","ShortDesc":"","CategoryId":93,"CategoryName":"Email service","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2216,"CategoryName":"Spam Protection"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2226,"CategoryName":"Email Migration"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2260,"CategoryName":"Private Email Contacts and Calendars Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2179,"CategoryName":"Private Email: General Information"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2215,"CategoryName":"Private Email: Mailbox Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2214,"CategoryName":"Email Forwarding"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2176,"CategoryName":"Private Email: DNS Settings"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2178,"CategoryName":"Private Email: Webmail Features"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2175,"CategoryName":"Private Email: Client Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2171,"CategoryName":"Private Email: Active Sync (Exchange) Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":31,"CategoryName":"cPanel Email FAQs"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2186,"CategoryName":"cPanel Email: Client Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2204,"CategoryName":"Private Email: Video Overview"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":32,"CategoryName":"DNS settings"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":15,"CategoryName":"Namecheap Market"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2186,"CategoryName":"cPanel Email: Client Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2266,"CategoryName":"Windows"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2287,"CategoryName":"SSL questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2267,"CategoryName":"Android"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2208,"CategoryName":"3rd Party Services Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2204,"CategoryName":"Private Email: Video Overview"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/security-red.png","ShortDesc":"","CategoryId":14,"CategoryName":"SSL Certificates","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2217,"CategoryName":"Renewal"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2218,"CategoryName":"cPanel SSL Plugin"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2221,"CategoryName":"Multi-Domain SSL Certificates"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2222,"CategoryName":"Cancellation"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2223,"CategoryName":"Browser errors"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2224,"CategoryName":"Site Seal, Logo"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2238,"CategoryName":"SSL installation errors"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2290,"CategoryName":"CSR code"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2293,"CategoryName":"Automated SSL management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":38,"CategoryName":"SSL General"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":67,"CategoryName":"Activation"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":68,"CategoryName":"Validation"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":69,"CategoryName":"Installation"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":70,"CategoryName":"Reissuance"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":true,"Description":"","ImageUrl":"/assets/img/pictograms/150/performance-red.png","ShortDesc":"","CategoryId":9,"CategoryName":"My Account","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":9,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":45,"CategoryName":"Account Security"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":9,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":43,"CategoryName":"Profile Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":9,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":44,"CategoryName":"Account Access"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2278,"CategoryName":"Handshake TLDs"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":103,"CategoryName":"LVE (CloudLinux)"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/affiliates-red.png","ShortDesc":"","CategoryId":55,"CategoryName":"Affiliates","SubCategories":[]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":89,"CategoryName":"SSH Access"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/tools-red.png","ShortDesc":"","CategoryId":2211,"CategoryName":"API & Resellers","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2211,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2227,"CategoryName":"SSL Resellers"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2211,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2229,"CategoryName":"Hosting Resellers"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2211,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":63,"CategoryName":"Namecheap API"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2211,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2196,"CategoryName":"WHMCS module for SSL"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/timer-red.png","ShortDesc":"","CategoryId":2212,"CategoryName":"Legacy Products","SubCategories":[]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":205,"CategoryName":"FTP questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2180,"CategoryName":"MySQL questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2199,"CategoryName":"Hosting Migration"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/premiumdns-red.png","ShortDesc":"","CategoryId":2231,"CategoryName":"PremiumDNS","SubCategories":[]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2194,"CategoryName":"Tips & Tricks"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"https://static.nc-img.com/live-resource/icons/knowledgebase/fastVPN_icon-150px.png","ShortDesc":"","CategoryId":2265,"CategoryName":"FastVPN","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2292,"CategoryName":"Browser Extensions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2274,"CategoryName":"General"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2270,"CategoryName":"Routers"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2272,"CategoryName":"TV"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2273,"CategoryName":"Gaming Consoles"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2268,"CategoryName":"macOS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2269,"CategoryName":"iOS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2271,"CategoryName":"Linux"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2266,"CategoryName":"Windows"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2267,"CategoryName":"Android"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":239,"CategoryName":"WHMCS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":33,"CategoryName":"SSL Installation"}],"status":200,"statusText":"OK"}}Security is a basic requirement of any project in the IT industry. Rapid development of new technologies, strict compliance standards, and evolving threats from hackers make it essential to keep your business’ security tools up-to-date and as strong as possible.
Namecheap is proud to provide its customers with the most state-of-the-art online security solutions available. It’s our job to make sure all our customers are well-protected and secure at every level.
This article will guide you through the main points of high-level security, as well as show you how to enhance the security of your IT business, thereby building customer confidence and loyalty.
If you haven’t already, we recommend first visiting our Knowledgebase to learn more about SSLs: what they’re used for and how to install one on a server.
In our review, we will use SSLLabs as a testing project of Qualys, a company that provides strategic security solutions. We will use their A+ indicator as the industry high standard in SSL security and will try to meet its requirements. The SSLLabs checker covers two substantial parts of the investigation: Authentication, which reflects details about installed SSL certificate and additional certificates provided by a server, and Configuration, which shows server settings for secure negotiation used in client-server interaction.
Authentication
The first block of Authentication is called Server Key and Certificate #1. Its main points are certificate validity, key type and size used to generate an SSL (our system accepts both RSA and ECC keys), signature algorithm, and whether or not an SSL certificate is trusted.
SSL certificates encrypt data being exchanged between server and browser with the help of hash function. SHA-1 was the most actively used hash function.
According to the Certificate Authority and Browser Forum, which develops and establishes requirements for Certificate Authorities to issue publicly trusted certificates, SHA-1 signature algorithm is being phased out as of November 2014. This makes it necessary for certificates to be issued in SHA-2 so that all browsers show no warnings. Our system issues certificates in SHA-2 automatically. For those customers who issued their SSLs before the effective date of transition, reissuance is needed to get updated and valid certificates. You can check which hashing algorithm the certificate is issued in with the help of this tool.
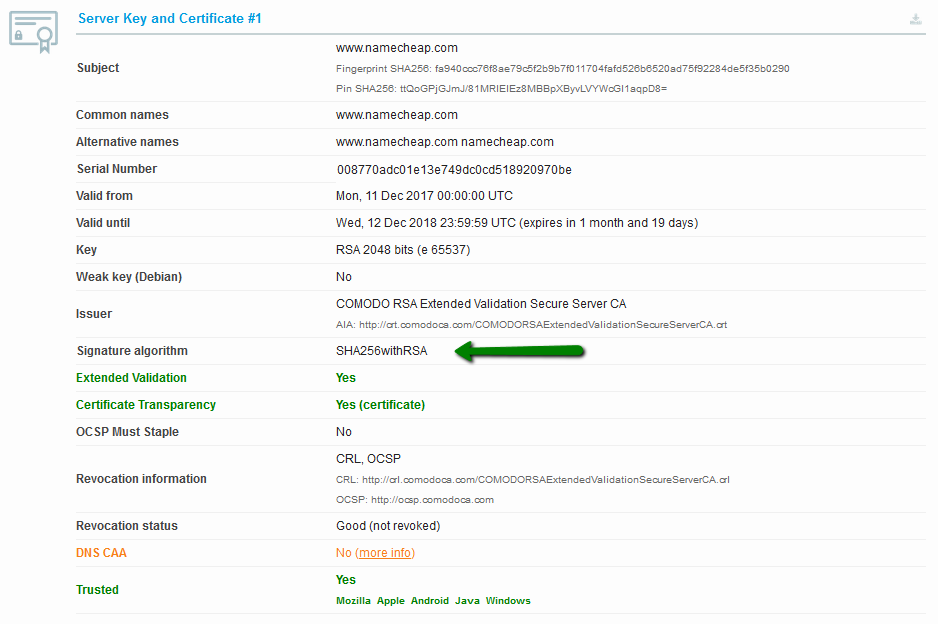
Another important point (highlighted in green in the screenshot above) is whether the server returned certificates issued by Certificate Authority during the test. Intermediate CA certificates are used to link the domain certificate to the trusted Certificate Authority. They should also be installed on the server for the certificate to be recognized as trusted in all browsers.
Two other blocks of Authentication show us these Intermediate certificates and the paths to them constructed during client-server interaction. A root certificate is self-signed, meaning it is not signed by another entity that has been given authority. The root certificate gets authority through the root certificate program managed by the operating system or browser developer. All root certificates issued by CAs are kept in the trust stores of browsers, so there is no need to install a root SSL on the server.
It should be noted that if a root SSL is installed and sent by a server, it will be shown with this message:
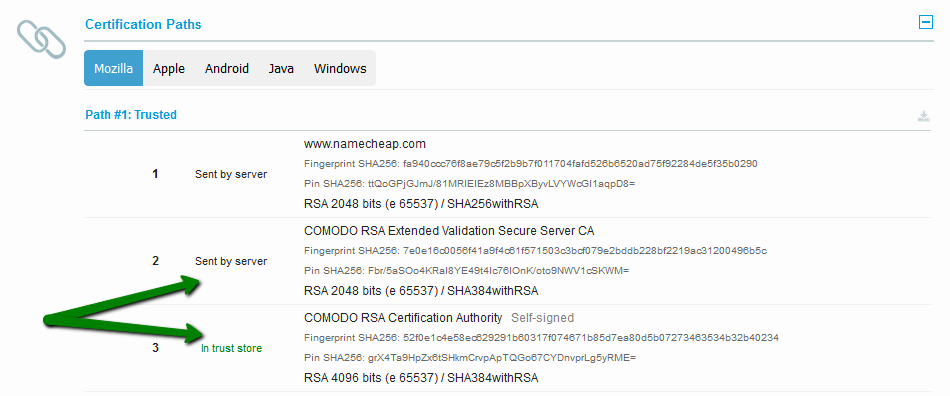
SSLLabs reflects it as ‘chain issues’:
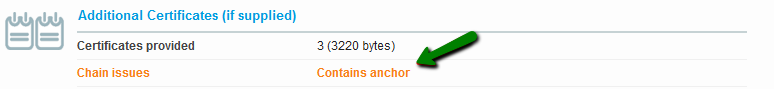
This is not an error. It increases network latency during the SSL handshake and is not considered an issue according to RFC 5246.
SSLLabs also checks if the intermediate certificates are valid using several key points: expiration date, key, issuer, and signature algorithm. Since the signature on a root certificate is not verified (as the software trusts the root certificate public key directly), there is nothing to worry about if a root SSL is issued in SHA-1. A self-signed root SSL is marked with a green ‘In trust store’ phrase, both in ‘Additional certificates’ and ‘Certification Paths’ blocks:
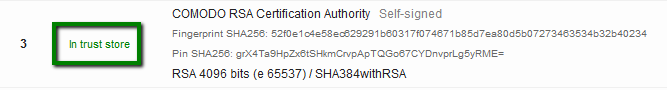
So, in order to proceed successfully with Authentication, a valid SSL certificate with the right key size (at least 2048-bit for RSA and 256-bit for ECDSA) and a SHA-2 hashing algorithm issued by a trusted Certificate Authority should be used. A complete CA bundle, including all intermediate certificates, must be installed too.
Configuration
This part includes the following segments: Protocols used by a server to establish secure connection; available Cipher Suites, from which a browser or client software can select at the moment of session setup; SSL Handshake Simulation which shows how the connection would occur with different software and which protocol version, ciphers, and encryption level would be used; Miscellaneous, which includes general information; and one of the most important blocks – Protocol Details, in which we can see security flaws that should be fixed on server side.
Protocols
There are five available protocol versions for SSL connection: SSL 2, SSL 3, TLS 1.0, TLS 1.1, and TLS 1.2. Currently, TLS 1.2 is the latest version and is considered the most secure Transport Layer Security (TLS) protocol, allowing client/server applications to communicate in a way that is designed to prevent eavesdropping, tampering or message forgery. [RFC 5246].
SSLLabs highlights TLS 1.2 with green:

Namecheap shared hosting accounts are configured to accept all connections using TLS versions only. It is better to have all TLS versions enabled in order to prevent compatibility issues with legacy software/apps. Enabling SSLv3 will allow customers with IE 6 to visit your website over HTTPS but will make a server vulnerable to POODLE attack.
Cipher suites are displayed in server-preferred order from the strongest to weakest that are available in client-server secure interaction. Let’s take a look what these strings consist of:
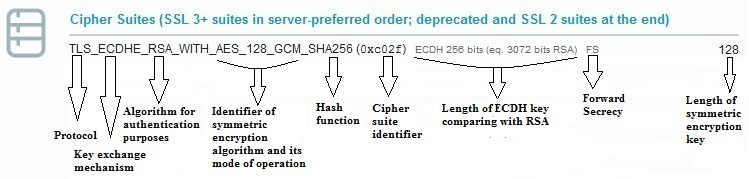
Namecheap offers our customers only strong cipher suites with all our fully-managed servers. Below is the example of the cipher suite for shared and reseller hosting plans:
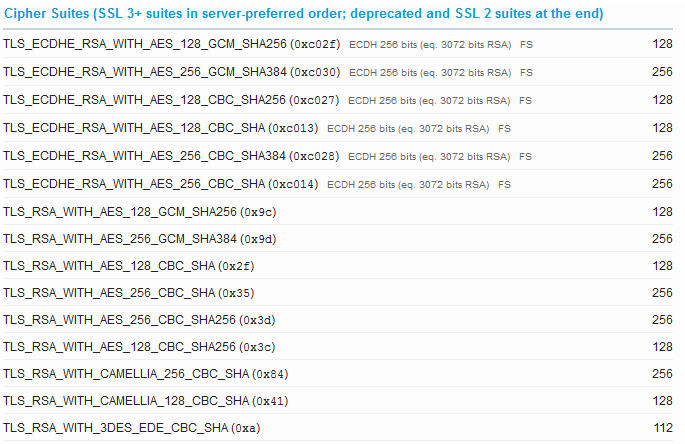
Customers with self-managed VPS and dedicated servers should manage cipher suites themselves.
SSL handshake simulation is being carried out successfully with most client software except for clients which do not support Server Name Indication (SNI). Since all Namecheap servers have SNI enabled by default, SSL connection with Android 2.3.7, Internet Explorer 6 and 8 on Windows XP, and Java 6u45 will fail unless the user ordered a dedicated IP address.
The aforementioned versions of Internet Explorer and OpenSSL package 0.9.8y do not support Forward Secrecy, this should be adjusted on server as well. Visit our Knowledgebase to learn more about Perfect Forward Secrecy and how to check whether a server provides it. For customers with third-party hosting servers, instructions for deploying FS can be found here and here. Servers based in Namecheap datacenters have the FS feature enabled with modern versions of browsers on most of them.
Finally, we come to Protocol Details, perhaps the most interesting and important segment. Customers who use Namecheap’s fully-managed hosting plans don’t have to worry about server configurations since our Technical Team keeps them up-to-date, tracks all announced weaknesses, and immediately deploys fixes for them. An ‘A’ grade should be shown by default when a valid SSL certificate with all Intermediate CA certificates is installed.
The coveted “A+” grade on SSLLabs can be achieved by enabling of HSTS policy on a server. HSTS technique is explained here. In a nutshell, HSTS is a mechanism enabling web sites to declare themselves accessible only via secure connections, and/or for users to be able to direct their user agent(s) to interact with given sites only over secure connections as indicated in RFC 6797.
Accordingly, a server can send a special header in HTTPS request to client software asking to use forced secure connection. Once HSTS policy is enabled, you will see that much-desired message:
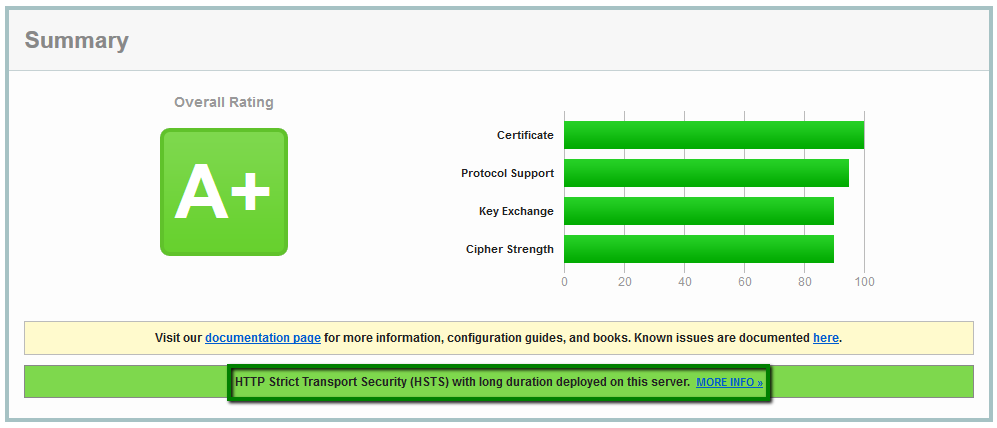
TLS only protocol versions, modern cipher suites, and mitigations for all known SSL vulnerabilities must be applied carefully to pass Configuration block checking successfully.
So, let’s summarize what we’ve learned: Since Namecheap’s fully-managed hosting servers have all the necessary settings pre-configured, all our customers need to do to get an ‘A+’ grade on SSLLabs is to install a valid SSL certificate with CA bundle and configure HSTS in .htaccess.
Several key points still should be mentioned for customers with third-party hosting servers, however. In order to set good server configuration, you’ll need to do a few things:
That’s all! We wish you good luck and security in your business.
{}Need help? We're always here for you.
{}