There are two sides of DNSSEC - Signing and Validation; together, they provide an increased level of security offered by DNSSEC. Both sides are necessary for the overall deployment, but both are implemented separately.
Signing
Your domain is "signed" by the operator of the nameservers that are authoritative for your domain. These nameservers can be operated by a DNS provider, by your registrar with whom you registered the domain (that also provides a default DNS service) or by a web hosting provider who provides DNS hosting or your own authoritative DNS servers (or those of someone else who is publishing the domain on your behalf).
Essentially, on the signing side of DNSSEC, the process looks like this:
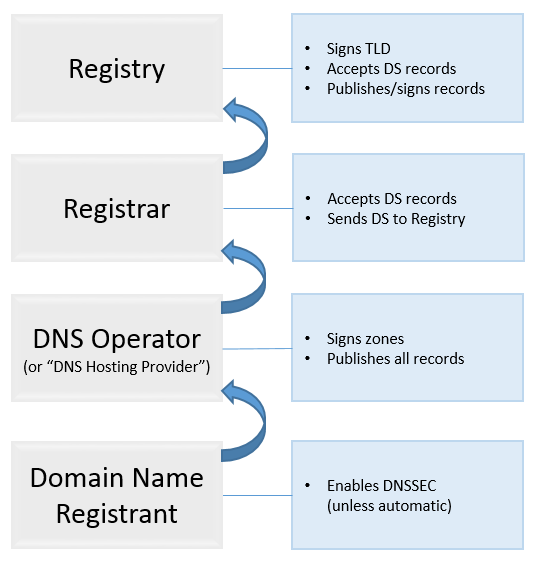
1. A domain name registrant enables DNSSEC on the side of DNS the domain uses.
2. A DNS Operator that hosts DNS records signs them with DNSSEC keys.
As a part of the process, they will generate a DS (Delegation Signer) record that must be provided to the parent zone (typically, a top-level domain (TLD)) to complete the "global chain of trust". (It is a chain of lookups validated by the domain name's digital signature that secures the request through all lookup nodes. This ensures that no rogue or illicit player can slip into the lookup path and redirect the lookup to a bogus site.)
At the moment, you can run DNSSEC on the following nameservers:
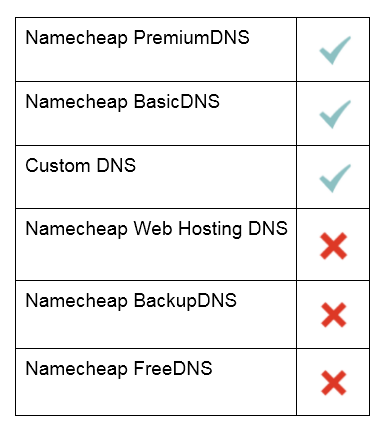
NOTE: Currently, there is no possibility to run DNSSEC on the Namecheap PremiumDNS nameservers for domain names that are not registered with Namecheap. Also, DNSSEC is not supported for the domains pointed to our Shared/Reseller packages.
3. A domain name registrant has to provide this DS record to the domain registrar. The registrar’s system has to be able to accept DS records and pass them up.
The option to manage DNSSEC is not available for the following TLDs:
.africa, .cm, .com.sg, .de, .eu, .nl, .ph, .sg, .so, .to, .com.au, .net.au, .org.au, handshake domains
4. The Registrar then provides this DS record to the Registry that operates the TLD (the TLD in question must be DNSSEC-compatible in this case).
Here’s how the DNSSEC signing process looks like:
Validation
Validation is performed by DNSSEC-validating DNS resolvers. It can be performed by a DNS resolver running at any point in your network, including a web browser, an instant messaging client or a mail server or client. It can also be a DNS resolver on your local computer built into your operating system, the DNS resolvers provided by your Internet Service Provider (ISP) or public DNS resolvers such as DNS resolvers operated by Google’s Public DNS.
During validation your domain’s DNSSEC signatures are cryptographically checked. As a part of validation, the DNS resolver also checks the "global chain of trust", from the DNS root server all the way down to the domain to ensure that the information has not been modified. Ideally, DNSSEC validation will occur as close as possible to the end user (either a person or a device).
That's it!
If you have any questions, feel free to contact our Support Team.

