| Subtotal | $0.00 |
| Subtotal | $0.00 |
This is not recommended unless requested explicitly. Disabling SHA-1 on Windows Server results in a great number of incompatible clients!
SHA-1 hash function was deprecated by CA/B Forum due to the consideration that this hash function became practically vulnerable to collision attacks. At the time of writing, Google Chrome treats the connection as the one secured by obsolete cryptography, if the negotiated cipher suite implies SHA-1 hash function for message authentication.
Unless you desperately require to forbid the server usage of SHA-1 cipher suites, there is an option to leave support for SHA-1 enabled, but configure the server preferences to use ciphers with a more secure hash function in the first place. See the next section of this article for the corresponding how-to.
Win + R >> regedit
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\Schannel\Hashes
Right-click on Hashes >> New >> Key
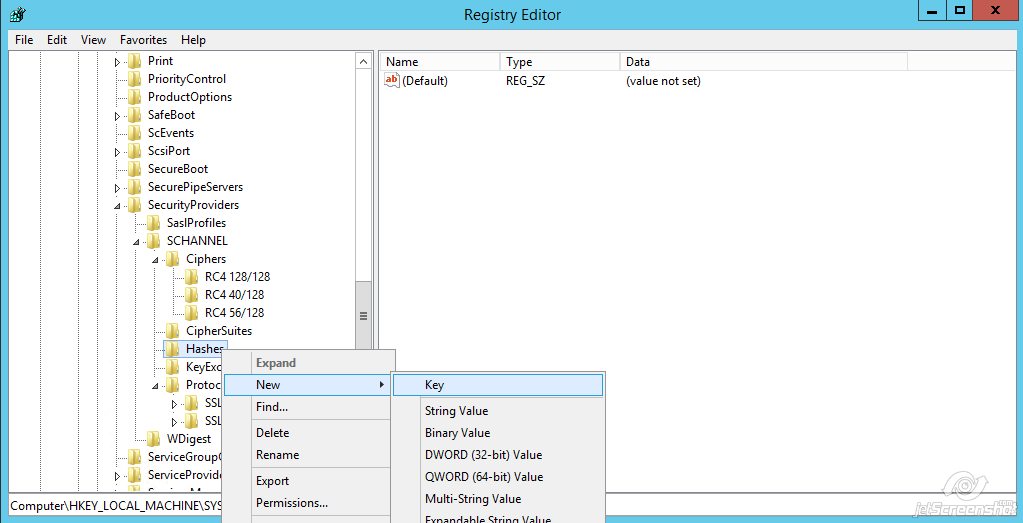
Name the key 'SHA'
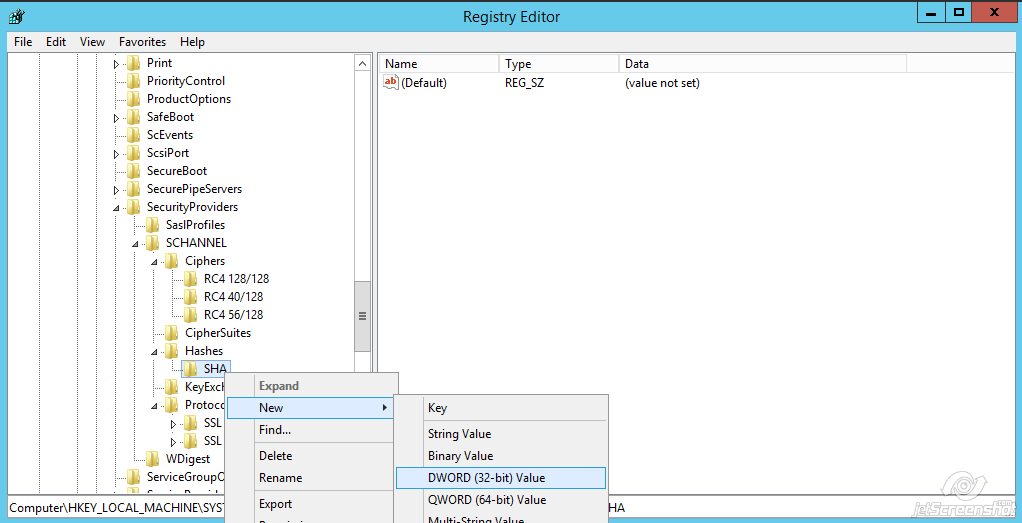
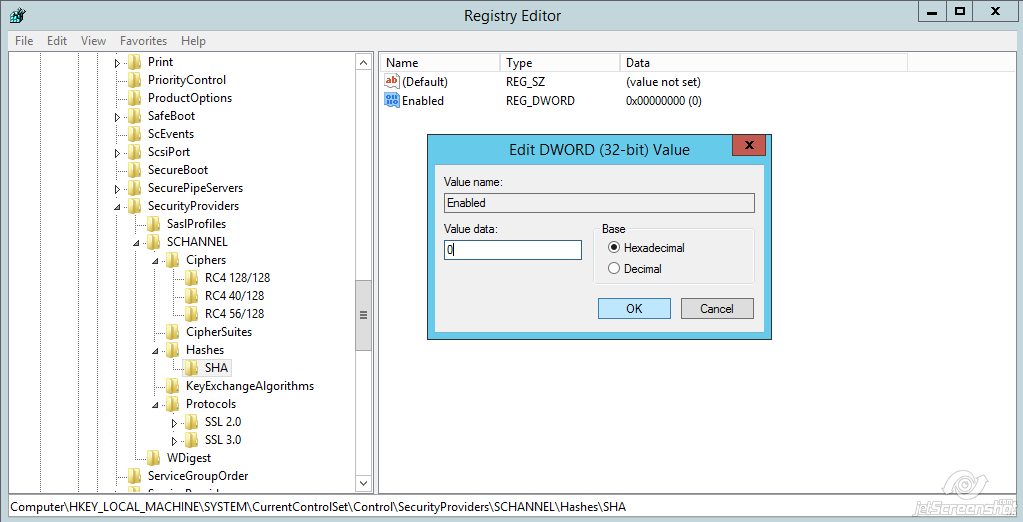
Name the value 'Enabled'
Need help? We're always here for you.