| Subtotal | $0.00 |
| Subtotal | $0.00 |
The error message differs depending on browsers. The most popular ones are listed below:
Firefox:
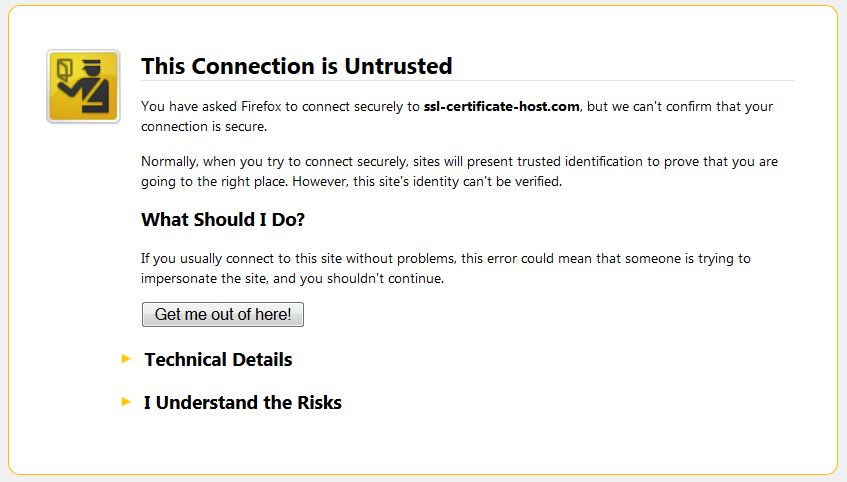
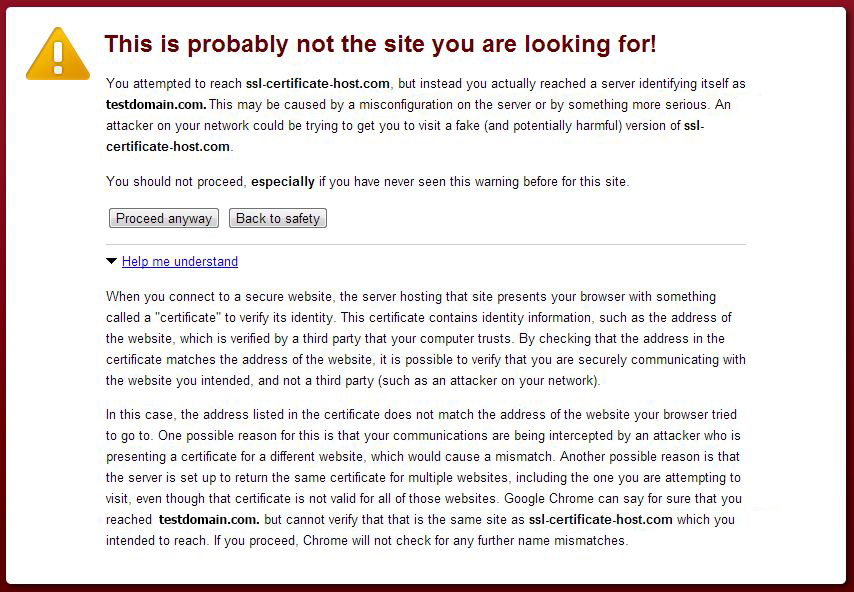
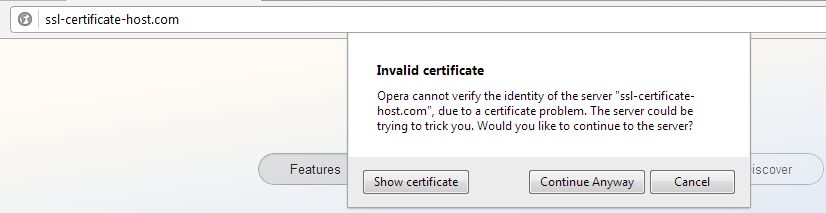
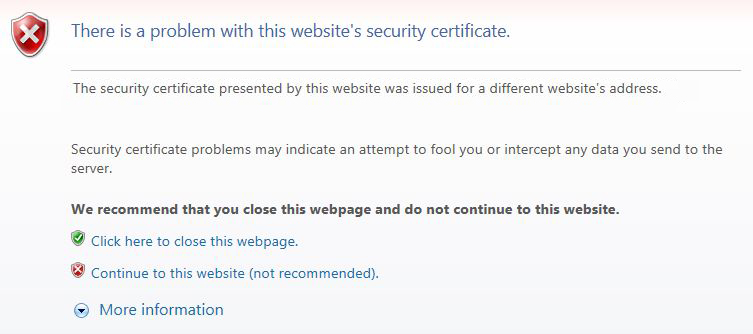
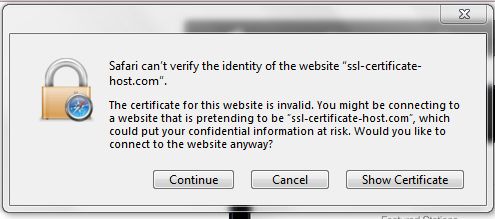
Usually a dedicated IP is required in order to install the SSL certificate. If there is already a certificate installed within the same IP address, the browser will establish a connection to the original certificate installed within the IP address.
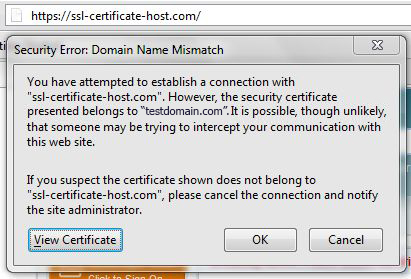
During the establishment of an SSL/TLS session, the client's browser compares the Common Name the primary certificate is issued for, with the domain name the browser tries to resolve. If the Common Name differs from the domain name the request was sent to, the Common Name mismatch warning occurs.
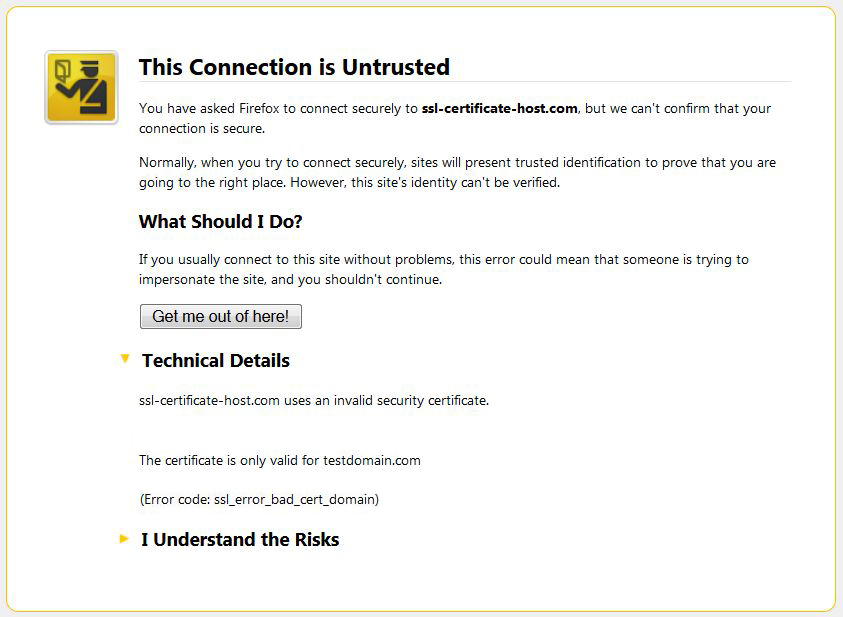
The warning claims that the certificate that has been picked up by request is issued for domaintest.com. This occurred because the domain name in the request did not match the domain name the certificate is issued for. If your web host, as well as we do, provides SNI (Server Name indication) that allows to host several certificates on the same IP address, you will not need an additional IP address. The same warning can appear if the certificate for the hostname you are trying to reach (in our case ssl-certificate-host.com) is not installed on the server even with SNI enabled.
The Error Code is not always the same; it can also be sec_error_untrusted_issuer in Firefox, like on the screenshot below:
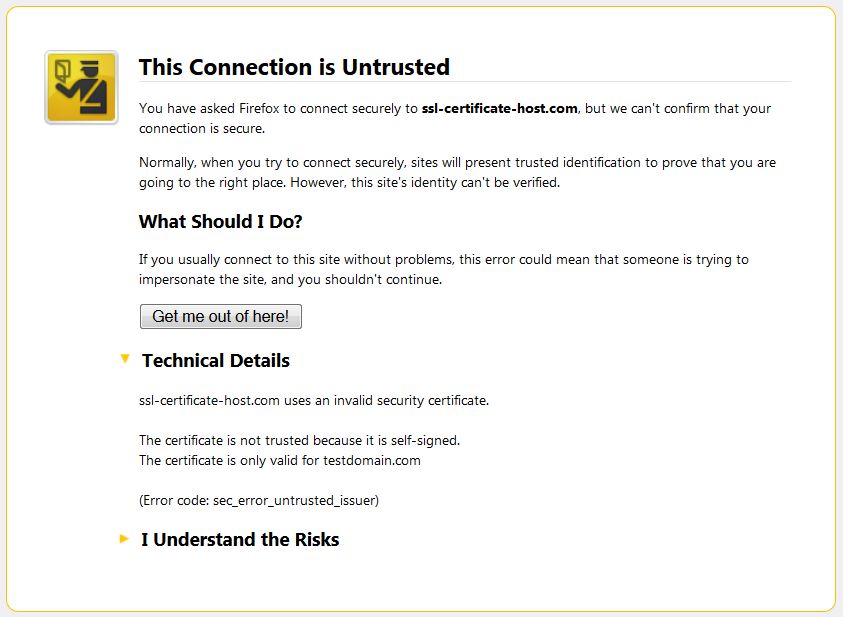
The error code sec_error_untrusted_issuer instead of ssl_error_bad_cert_domain in this case means that the primary certificate for this IP address (cert for testdomain.com) is not issued by a trusted Certificate Authority (i.e. it’s self-signed).
Solution:
If you face such an error, please contact your hosting provider in order to obtain a dedicated IP for your website. Once you get a dedicated IP, you can install the certificate within this IP. Before requesting a dedicated IP you may verify with your web host if they support SNI technology.
Make sure your certificate is installed properly on your server. You should note that most of the installation checkers would not be able to show an installed certificate correctly unless it has a dedicated IP or SNI technology is set for it correctly.
The Common Name mismatch warning may occur if a wildcard certificate is installed via cPanel or WHM for the bare domain only, while one tries to establish an https connection to a subdomain of the domain the wildcard certificate is issued for. Wildcard certificates are supposed to cover the naked domain name and subdomains of the same level. However, if a wildcard certificate is installed for a bare domain via cPanel or WHM, subdomains will not be secured automatically. If a shared IP was used (even with SNI technology) the request cannot find the certificate with a matching Common Name therefore, request picks up a primary certificate that resolves under the IP address the domain name in request resolves to.
In case of a dedicated IP the details of a mismatch warning may be confusing a little bit, but the process is the same - the request will find your wildcard certificate as a primary one and consider it as a not matching one, as the subdomain name is not encoded in the certificate’s body.
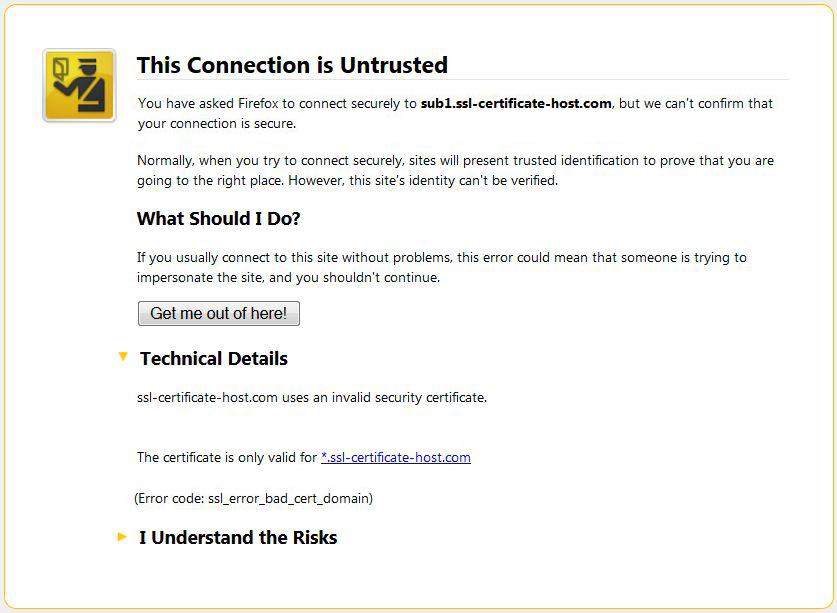
Solution: This issue occurs due to technical withdrawals of cPanel and WHM, there are several ways to solve it:
a) install the certificate for each subdomain via WHM/cPanel
b) if you have root access to the server, please install it directly on the server editing a VirtualHost file. You can find more information regarding this question here.
The error occurs if one tries to establish an https connection for an IP address. Regular SSL certificates can be issued only for a FQDN (Fully Qualified Domain Name). Even if you have a dedicated IP address, the common name mismatch will be shown because the https request via an IP address does not contain the server name (domain/subdomain name) itself, therefore there is no way to avoid the warning trying to access the site via an IP address, as a regular certificate is issued for a domain/subdomain name.
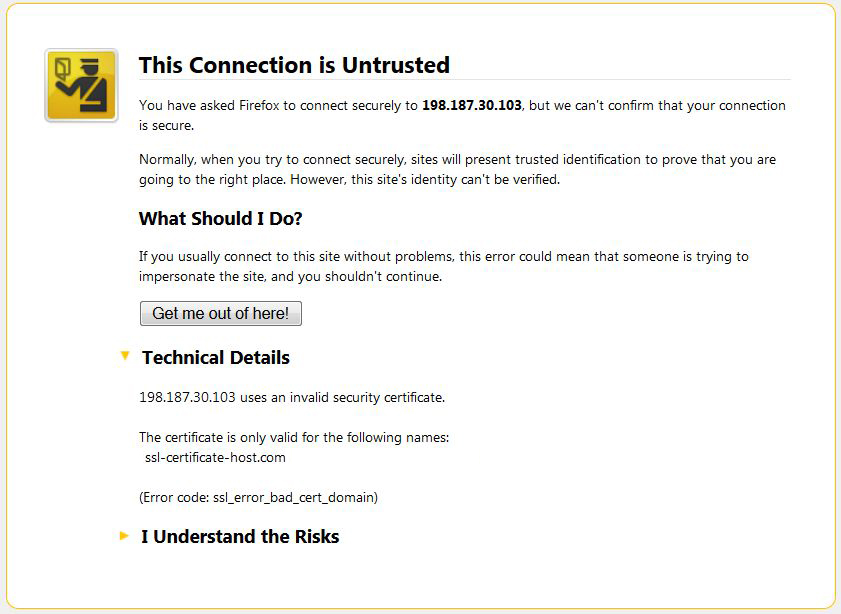
Solution: Please access your web page using the hostname, not an IP address.
The error can appear also with a wildcard certificate, if you are trying to access a subdomain of the fourth or a higher level, while a wildcard certificate is valid for the main domain and subdomains of the third level.
If a wildcard certificate was issued for *.ssl-certificate-host.com, it is valid for ssl-certificate-host.com and all the subdomains of the third level, like sub1.ssl-certificate-host.com, sub2.ssl-certificate-host.com, sub3.ssl-certificate-host.com etc., but it does not cover subdomains of the fourth or higher levels (like sub2.sub1.ssl-certificate-host.com or sub3.sub2.sub1.example.com)
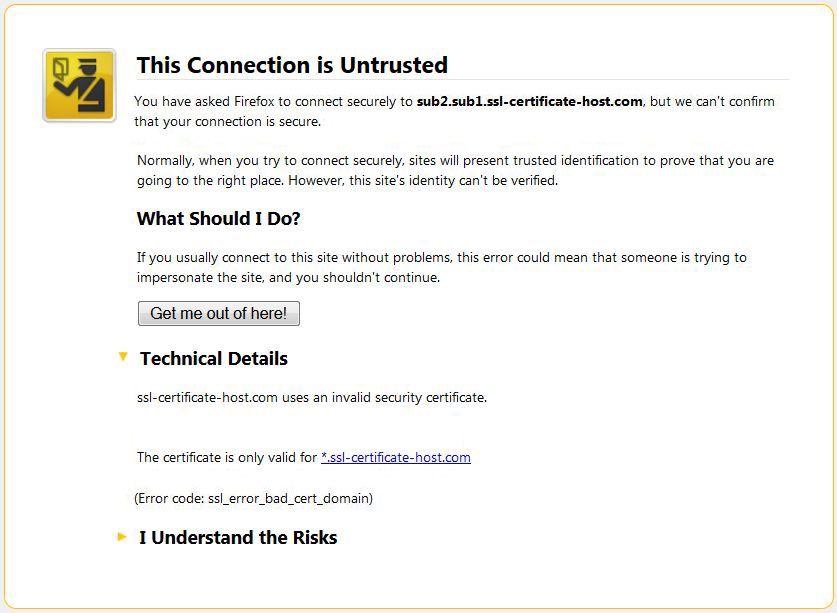
Solution: To cover several levels of subdomains you may either issue several different Wildcard certificates or a UCC certificate.
The Common Name mismatch may occur if the IP address your domain name is pointed to has been recently changed. If you ordered a dedicated IP and the certificate has been installed shortly after that, there is a high possibility that there is DNS propagation and the domain still resolves to the previous IP address, while the certificate is under the new one. There may be a certificate for another domain installed on the previous IP address, which is why the error occurs.
Solution: No actions are required; please allow some time for the DNS records to be updated.
If you have not found a solution for your issue in this article or still have any questions, please contact our SSL Support Team.
Need help? We're always here for you.