To ensure a proper work of FastVPN with a pfSense router, you will need:
- A secure FastVPN connection (Don’t have one? Sign up here!);
- An internet connection;
- Access to you FastVPN Account Panel.
- pfSense hardware (this guide uses pfSense v2.4.5 version for demonstration purposes).
- In your PfSense device click on System >> Cert manager >> CAs and then click on +Add
- Give the CA a name (it can be whatever you want, lets say “CA_NCVPN_CERT”).
- Chose to Import an existing Certificate Authority. Copy and paste the certificate from here into the Certificate data field.
- Click on Save.
2. Add a VPN connection:
3. Firewall setup
pfSense
is a system with good security level; for this reason you have to set
some rules to enable users to connect with vpn and to the other systems
in lan:
- Move to Firewall –> Rules –> WAN
- Add this rule:
Protocol IPv4 TCP
Source *
Port 1194
Destination This Firewall
Port 1194
Gw *
Queue none - To enable OpenVPN clients to connect to LAN ip move to Firewall –> Rules –> OpenVPN
- Add this rule:
Protocol IPv4 TCP
Source *
Port *
Destination *
Port *
Gw *
Queue none
Since
OpenVPN is not the default router, it’s mandatory that every connected
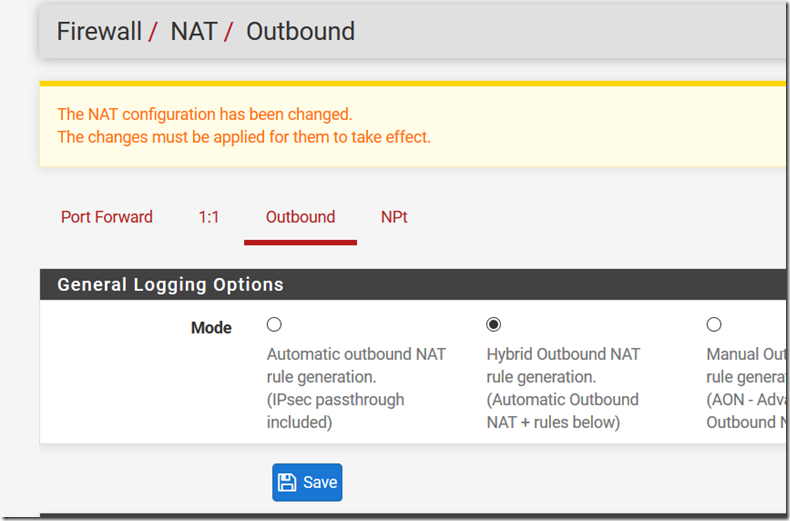
client must be masquerade by firewall IP. Move to Firewall –> NAT
–> OpenVPN then configure Outbound Mode Hybrid.
Add
masquerading rules from every client connecting. This is because every
server in LAN has a default gw rule pointing to the edge. For this
reason the only way to connect is using the pfSense IP which has a LAN
IP.
The simplest way to distribute client-to-lan vpn to users is:
1. Issue new user in System -> User manager -> Users.
2. Share configuration data for OpenVPN client.
We suggest to install opnevpn-client-export package to speed-up VPN client delivery process
Test
the VPN simply downloading OpenVPN client and export configuration (or
download a packaged version directly from VPN –> OpenVPN –> Client
Export) and connecting with it’s option under OpenVPN client connection
option.
That’s it! pfSense VPN setup is complete, and you should now have a FastVPN connection.
If you need any further assistance, please contact our
Support Team.