Hardening anti-spam security policies on the server
exim -bpc
exim -bp
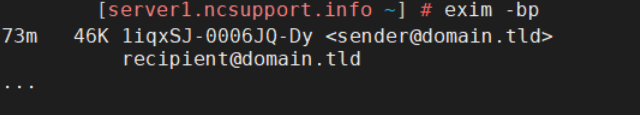
By the way, if the email queue is large, you can pipe the result of “exim -bp” to “less” command to avoid cluttering:
exim -bp | less
exim -Mvh Exim ID exim -Mvb Exim ID exim -Mvl Exim ID
exim -Mrm Exim ID
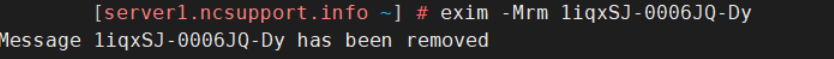
exim -M Exim ID
exiqgrep -f sender@domain.tld
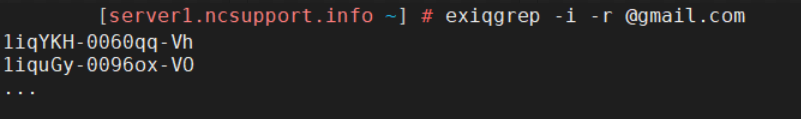
exiqgrep -i -r @gmail.com
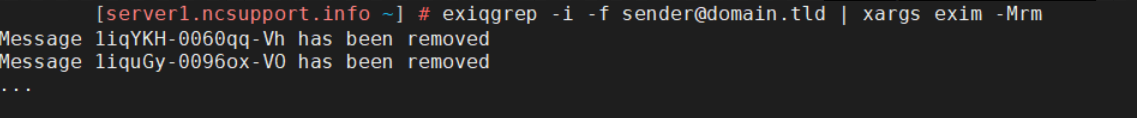
exiqgrep -i -f sender@domain.tld | xargs exim -Mrm
exim -bp|grep "<"|awk {'print $3'}|xargs exim -Mrm
grep cwd=/ /var/log/exim_mainlog | cut -d = -f 2 | cut -d " " -f 1 | sort | uniq -c | sort -n
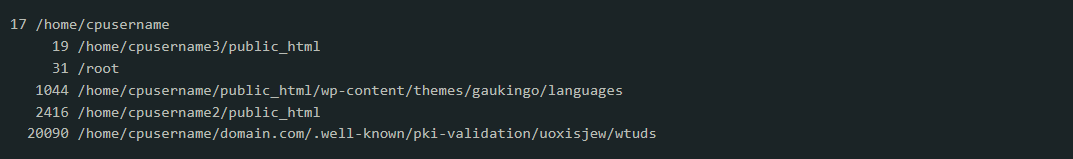
ls -lat /home/cpusername1/domain.tld/.well-known/pki-validation/ksdjgfkls/wtuds/
chmod 000 /home/cpusername1/domain.tld/.well-known/pki-validation/ksdjgfkls/wtuds/pdyihizr.php
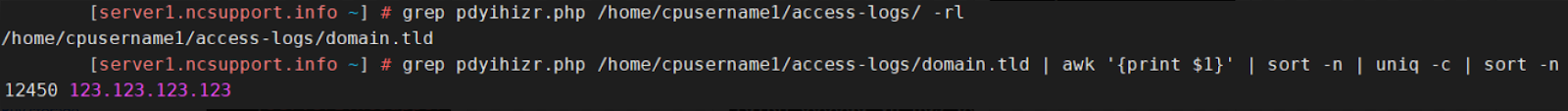
grep pdyihizr.php /home/cpusername1/access-logs/ -rl
grep pdyihizr.php /home/cpusername1/access-logs/domain.tld | awk '{print $1}' | sort -n | uniq -c | sort -n
grep X-PHP-Script /var/spool/exim/input/*/*-H | awk '{print $3}' | sort | uniq -c | sort -nr
The command above will screen the active mail queue on the server only.awk -F"T=\"" '/<=/ {print $2}' /var/log/exim_mainlog | cut -d\" -f1 | sort | uniq -c | sort -n
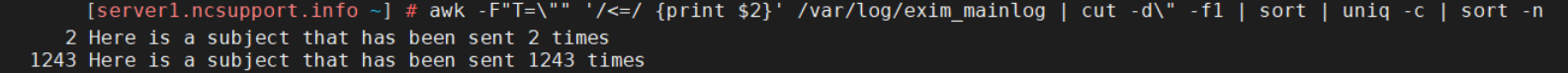
grep "Here is a subject that has been sent 1243 times" /var/log/exim_mainlog | awk '{print $5}' | sort | uniq -c | sort -n
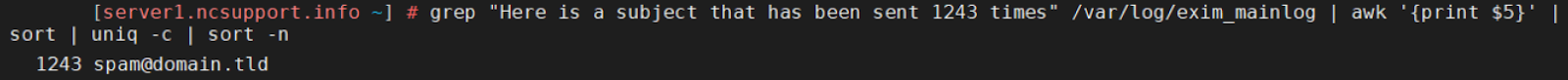
grep "<= spam@domain.tld" /var/log/exim_mainlog | grep "Here is a subject that has been sent 1243 times" | grep -o "\[[0-9.]*\]" | sort -n | uniq -c | sort -n
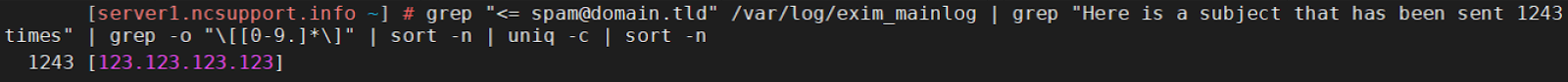
cd /usr/local/src/ wget http://www.rfxn.com/downloads/maldetect-current.tar.gz tar -xzf maldetect-current.tar.gz cd maldetect-* sh ./install.sh
ln -s /usr/local/cpanel/3rdparty/bin/clamscan /usr/local/bin/clamscan ln -s /usr/local/cpanel/3rdparty/bin/freshclam /usr/local/bin/freshclam
nano /usr/local/maldetect/conf.maldet
Need help? We're always here for you.