{"/api/v1/ncpl/simplekb/getarticle:\"{\\\"articleId\\\":10200,\\\"categoryId\\\":89}\"":{"body":{"Id":10200,"FriendlyId":"","ArticleTypeId":0,"Title":"How to secure your SSH login","ArticleName":"How to secure your SSH login","ArticleSummary":null,"PreponedSummary":false,"Approved":true,"Body":"V2hlbiBkZWFsaW5nIHdpdGggYSBWUFMgb3IgYSBEZWRpY2F0ZWQgc2VydmVyLCB5b3Ugd2lsbCB1c2UgU2VjdXJlIFNoZWxsIHRvIGFjY2VzcyB0aGUgc2VydmVyIHRvIG1hbmFnZSBldmVyeWRheSB0YXNrcy4gSWYgeW91IGFjY2VzcyB5b3VyIHNlcnZlciByZW1vdGVseSAodXNpbmcgU1NIKSwgaXQncyBhIGdvb2QgaWRlYSB0byBwcm90ZWN0IHlvdXJzZWxmIGFnYWluc3QgYXR0YWNrcy4gSGVyZSBhcmUgc29tZSByZWNvbW1lbmRhdGlvbnMgb24gaG93IHRvIHNlY3VyZSB5b3VyIFNTSCBsb2dpbjo8YnIgLz48YnIgLz48cD48YSBocmVmPSIjRGlzYWJsaW5nIHJvb3QgbG9naW5zIj5EaXNhYmxpbmcgcm9vdCBsb2dpbnM8L2E+PC9wPjxwPjxhIGhyZWY9IiNDaGFuZ2luZyBkZWZhdWx0IFNTSCBwb3J0Ij5DaGFuZ2luZyBkZWZhdWx0IFNTSCBwb3J0PC9hPjwvcD48dWw+PGxpPjxwPjxhIGhyZWY9IiNHZW5lcmF0ZSBTU0gga2V5cyI+R2VuZXJhdGUgU1NIIGtleXM8L2E+PC9wPjwvbGk+PC91bD48cD48L3A+PHA+PC9wPjxwPjxhIGhyZWY9IiNBY2Nlc3NpbmcgdGhlIHNlcnZlciB2aWEgU1NIIGtleXMiPkFjY2Vzc2luZyB0aGUgc2VydmVyIHZpYSBTU0gga2V5czwvYT48L3A+PHA+PGEgaHJlZj0iI2FkZGl0aW9uYWxfaW5mbyI+QWRkaXRpb25hbCBpbmZvcm1hdGlvbjwvYT48L3A+PHA+PC9wPjxiciAvPjxkaXY+PGJyIC8+PC9kaXY+TGV04oCZcyBoYXZlIGEgY2xvc2VyIGxvb2sgYXQgdGhlc2UgcmVjb21tZW5kYXRpb25zOjxiciAvPjxiciAvPjxiciAvPjxwPjxhIG5hbWU9IkRpc2FibGluZyByb290IGxvZ2lucyI+PGI+RGlzYWJsaW5nIHJvb3QgbG9naW5zPC9iPjwvYT48L3A+PGJyIC8+PGJyIC8+U2luY2UgdGhlIHJvb3QgdXNlciBpcyBncmFudGVkIGFsbCB0aGUgcHJpdmlsZWdlcyBvbiB0aGUgc2VydmVyLCBhbmQgZXhwb3NpbmcgdGhlIHJvb3QgbG9naW4gcG9zc2VzcyBhIHRocmVhdCB0byB5b3VyIGVudGlyZSBzeXN0ZW0sIGl0IG1heSBiZSBhIHdpc2UgZGVjaXNpb24gdG8gZGlzYWJsZSByb290IGxvZ2lucy48YnIgLz5IZXJlIGlzIGhvdyB0byBkbyBpdC48YnIgLz48YnIgLz48Yj5QcmVwYXJhdGlvbiBzdGFnZTwvYj46IE1ha2Ugc3VyZSB0byBjcmVhdGUgYSB1c2VyIHdpdGggPGI+U3VwZXJ1c2VyPC9iPiBBS0E6IDxpPnN1ZG88L2k+IHJpZ2h0cyB0byBwZXJmb3JtIGFsbCB0aGUgbmVjZXNzYXJ5IGFkbWluaXN0cmF0aXZlIGFjdGlvbnMuIE9uY2UgeW91IGFyZSBsb2dnZWQgaW4gdG8gdGhlIHNlcnZlciwgZm9sbG93IHRoZXNlIHN0ZXBzOjxiciAvPsKgPGJyIC8+MS4gVG8gY3JlYXRlIGEgbmV3IHVzZXIsIHJ1biB0aGUgZm9sbG93aW5nIGNvbW1hbmQ6PGJyIC8+PGJyIC8+PGRpdj48aT51c2VyYWRkIC1tIC1zIC9iaW4vYmFzaCAtYyAiQWRtaW4iwqAgdGVjaHVzZXI8L2k+PC9kaXY+PGRpdj48YnIgLz48L2Rpdj48ZGl2PjxpbWcgY2xhc3M9ImtiLWltYWdlIiBzcmM9Imh0dHBzOi8vTmFtZWNoZWFwLnNpbXBsZWtiLmNvbS9TaXRlQ29udGVudHMvMi03QzIyRDUyMzZBNDU0M0VCODI3RjNCRDg5MzZFMTUzRS9tZWRpYS9TU0hzZWN1cmUucG5nIiAvPjwvZGl2PjxkaXY+PGJyIC8+PC9kaXY+PGRpdj5XaGVyZTo8YnIgLz48YnIgLz48Yj5Vc2VyYWRkPC9iPiBpcyBhbiBhY3R1YWwgY29tbWFuZCB0byBjcmVhdGUgYSB1c2VyPGJyIC8+PGI+LW08L2I+IC0gYW4gYXJndW1lbnQgd2hpY2ggY3JlYXRlcyBhIHVzZXIgd2l0aCBhIGRlZmF1bHQgaG9tZSBkaXJlY3RvcnkgaW4gdGhlIGZvcm1hdCAvaG9tZS91c2VyIChpbiB0aGlzIGNhc2UgaG9tZS90ZWNodXNlcikuPGJyIC8+PGJyIC8+SWYgeW91IHdvdWxkIGxpa2UgdG8gdXNlIGEgZGlmZmVyZW50IGFyZ3VtZW50IHRoYW4gdGhlIGRlZmF1bHQgZGlyZWN0b3J5LCB1c2UgPGI+LWQ8L2I+IGFyZ3VtZW50IGluc3RlYWQgb2YgPGI+LW08L2I+LCBhbmQgc3BlY2lmeSB0aGUgZGVzaXJlZCBkaXJlY3RvcnkgZS5nLiA8aT4vZXhhbXBsZS9ob21lL3VzZXI8L2k+KTxiciAvPjxiciAvPjxiPi1zPC9iPsKgIC0gYWxsb3dzIHNwZWNpZnlpbmcgdGhlIHNoZWxsIGZvciB0aGUgdXNlciAoaW4gdGhpcyBjYXNlIHRoZSBzaGVsbCBpcyAvYmluL2Jhc2gpPGJyIC8+PGI+LWM8L2I+IC0gY29tbWVudCBhZGRpdGlvbi4gVGhlIGFjdHVhbCBjb21tZW50IGhlcmUgaXMg4oCYQWRtaW7igJkgPGJyIC8+PGI+dGVjaHVzZXI8L2I+IC0gYW4gZXhhbXBsZSB1c2VybmFtZS4gSW5zdGVhZCBvZiA8aT50ZWNodXNlcjwvaT4geW91IGNhbiB1c2UgYW55IHVzZXJuYW1lIHlvdSBsaWtlLCBqdXN0IGJlIHN1cmUgdG8gbW9kaWZ5IGFsbCB0aGUgY29tbWFuZHMgYWJvdmUgYWNjb3JkaW5nbHkpLjxiciAvPjxiciAvPlNldCBhIHBhc3N3b3JkIGZvciB0aGUgbmV3bHkgY3JlYXRlZCB1c2VyIChtYWtlIHN1cmUgeW91IHNldCA8YSBocmVmPSJodHRwczovL3d3dy5uYW1lY2hlYXAuY29tL3N1cHBvcnQva25vd2xlZGdlYmFzZS9hcnRpY2xlLmFzcHgvOTUxNy80NS93aGF0LWlzLWEtc2VjdXJlLXBhc3N3b3JkLWFuZC13aHktaXMtaXQtaW1wb3J0YW50LXRvLWhhdmUtb25lIiBsaW5rdGV4dD0iYSBzdHJvbmcsIHNlY3VyZSBwYXNzd29yZCIgbGlua3R5cGU9IkN1c3RvbSIgdGFyZ2V0PSJfcGFyZW50Ij5hIHN0cm9uZywgc2VjdXJlIHBhc3N3b3JkPC9hPikuPGJyIC8+PGJyIC8+PGI+Tk9URTwvYj46IFdoaWxlIHR5cGluZyB0aGUgbmV3IHBhc3N3b3JkIHlvdSB3b27igJl0IHNlZSBhbnkgc3ltYm9scyBhcHBlYXIsIGFzIGhpZGRlbiBmaWVsZHMgZG9u4oCZdCBzaG93IGFueXRoaW5nIGF0IGFsbC4gSWYgeW91IGhlc2l0YXRlIGFib3V0IHlvdXIgcGFzc3dvcmQgeW91IGNhbiBwcmVzcyA8Yj5DdHJsICsgVTwvYj4gdG8gZW1wdHkgdGhlIGZpZWxkIGFuZCB0aGVuIHN0YXJ0IGZyb20gc2NyYXRjaC48YnIgLz48YnIgLz48aT5wYXNzd2QgdGVjaHVzZXI8L2k+PGJyIC8+PGJyIC8+PC9kaXY+PHA+PC9wPjxkaXY+PGltZyBjbGFzcz0ia2ItaW1hZ2UiIHNyYz0iaHR0cHM6Ly9OYW1lY2hlYXAuc2ltcGxla2IuY29tL1NpdGVDb250ZW50cy8yLTdDMjJENTIzNkE0NTQzRUI4MjdGM0JEODkzNkUxNTNFL21lZGlhL1NTSHNlY3VyZTIucG5nIiAvPjwvZGl2PjxkaXY+PGJyIC8+PC9kaXY+PGRpdj5PbmNlIHlvdSBlbnRlcmVkIHRoZSBwYXNzd29yZCwgeW91IHNob3VsZCByZWNlaXZlIHRoZSBmb2xsb3dpbmcgb3V0cHV0OjwvZGl2PjxkaXY+PGJyIC8+PC9kaXY+PHA+PC9wPjxkaXY+PGltZyBjbGFzcz0ia2ItaW1hZ2UiIHNyYz0iaHR0cHM6Ly9OYW1lY2hlYXAuc2ltcGxla2IuY29tL1NpdGVDb250ZW50cy8yLTdDMjJENTIzNkE0NTQzRUI4MjdGM0JEODkzNkUxNTNFL21lZGlhL1NTSHNlY3VyZTMucG5nIiAvPjwvZGl2PjxkaXY+PGJyIC8+PC9kaXY+PGRpdj5Ob3cgeW91IG5lZWQgdG8gYXNzaWduIHN1ZG8gKFN1cGVydXNlcikgcmlnaHRzIHRvIHlvdXIgdXNlci4gVGhpcyBwcm9jZXNzIHZhcmllcyBkZXBlbmRpbmcgb24gdGhlIExpbnV4IGRpc3RyaWJ1dGlvbiB5b3UgYXJlIHVzaW5nLjxiciAvPjxiciAvPkRlYmlhbiAoYWxzbyBVYnVudHUpOjwvZGl2PjxkaXY+PGk+PGJyIC8+PC9pPjwvZGl2PjxkaXY+PGk+dXNlcm1vZCAtYUcgc3VkbyB0ZWNodXNlcjwvaT48YnIgLz48YnIgLz48L2Rpdj48cD48L3A+PGRpdj48aW1nIGNsYXNzPSJrYi1pbWFnZSIgc3JjPSJodHRwczovL05hbWVjaGVhcC5zaW1wbGVrYi5jb20vU2l0ZUNvbnRlbnRzLzItN0MyMkQ1MjM2QTQ1NDNFQjgyN0YzQkQ4OTM2RTE1M0UvbWVkaWEvU1NIc2VjdXJlNC5wbmciIC8+PC9kaXY+PGRpdj48YnIgLz48L2Rpdj48ZGl2PkNlbnRPUy9BbG1hTGludXgvQ2xvdWRMaW51eDo8L2Rpdj48ZGl2PjxiciAvPjwvZGl2PjxkaXY+PGk+dXNlcm1vZCAtYUcgd2hlZWwgdGVjaHVzZXI8L2k+PC9kaXY+PGRpdj48YnIgLz48L2Rpdj48cD48L3A+PGRpdj48aW1nIGNsYXNzPSJrYi1pbWFnZSIgc3JjPSJodHRwczovL05hbWVjaGVhcC5zaW1wbGVrYi5jb20vU2l0ZUNvbnRlbnRzLzItN0MyMkQ1MjM2QTQ1NDNFQjgyN0YzQkQ4OTM2RTE1M0UvbWVkaWEvU1NIc2VjdXJlNS5wbmciIC8+PC9kaXY+PGRpdj48YnIgLz48L2Rpdj5Ob3cgeW91IGNhbiB0ZXN0IGlmIHlvdXIgbmV3bHkgY3JlYXRlZCB1c2VyIGhhcyBzdWRvIHJpZ2h0czo8YnIgLz5Td2l0Y2ggdG8gdGhlIG5ldyB1c2VyIHlvdSd2ZSBjcmVhdGVkOjxiciAvPjxkaXY+PGJyIC8+PC9kaXY+PGRpdj48aT5zdSAtIHRlY2h1c2VyPC9pPjwvZGl2PjxiciAvPjxwPjwvcD48ZGl2PjxpbWcgY2xhc3M9ImtiLWltYWdlIiBzcmM9Imh0dHBzOi8vTmFtZWNoZWFwLnNpbXBsZWtiLmNvbS9TaXRlQ29udGVudHMvMi03QzIyRDUyMzZBNDU0M0VCODI3RjNCRDg5MzZFMTUzRS9tZWRpYS9TU0hzZWN1cmU2LnBuZyIgLz48L2Rpdj48ZGl2PjxiciAvPjwvZGl2PjxkaXY+UHJlcGVuZCBjb21tYW5kcyB0aGF0IHJlcXVpcmUgU3VwZXJ1c2VyIGFjY2VzcyB3aXRoIHN1ZG86PGJyIC8+Rm9yIGluc3RhbmNlOiA8aT5zdWRvIGxzIC1sYSAvcm9vdDwvaT48YnIgLz48YnIgLz5Zb3Ugd2lsbCBiZSBwcm9tcHRlZCB0byBlbnRlciBhIHBhc3N3b3JkIGZvciB5b3VyIHVzZXIgd2hpY2ggd2lsbCBiZSB1c2VkIHRvIGxvZyBpbiB0byB0aGUgc3lzdGVtIGFuZCBjb25maXJtIHN1ZG8gYWN0aW9ucyB3aGVuZXZlciB0aGV5IGFyZSByZXF1aXJlZCBieSB0aGUgc3lzdGVtLiA8YnIgLz5JZiB5b3UgZGlkIGV2ZXJ5dGhpbmcgY29ycmVjdGx5LCBpdCB3aWxsIGdpdmUgeW91IHRoZSBmaWxlIG91dHB1dDo8YnIgLz48L2Rpdj48YnIgLz48cD48L3A+PGRpdj48aW1nIGNsYXNzPSJrYi1pbWFnZSIgc3JjPSJodHRwczovL05hbWVjaGVhcC5zaW1wbGVrYi5jb20vU2l0ZUNvbnRlbnRzLzItN0MyMkQ1MjM2QTQ1NDNFQjgyN0YzQkQ4OTM2RTE1M0UvbWVkaWEvU1NIc2VjdXJlNy5wbmciIC8+PC9kaXY+PGRpdj48YnIgLz48L2Rpdj48ZGl2Pkhvd2V2ZXIsIElmIHlvdSBhcmUgdXNpbmcgV0hNL2NQYW5lbCwgeW91IGNhbiBhc3NpZ24gc3VkbyByaWdodHMgdG8gYW55IGNQYW5lbCB1c2VyLsKgIEl0IGlzIHByZWZlcmFibGUgdG8gdXNpbmcgdGhlIDxpPnVzZXJhZGQ8L2k+IGNvbW1hbmQuIFRvIGRvIHNvLCBvbmNlIGEgY1BhbmVsIGFjY291bnQgaXMgY3JlYXRlZCwgeW91IGNhbiBnbyB0byB5b3VyIDxiPldITTwvYj4gJmd0OyZndDsgPGI+U2VjdXJpdHkgQ2VudGVyPC9iPiAmZ3Q7Jmd0OyA8Yj5NYW5hZ2Ugd2hlZWwgZ3JvdXA8L2I+ICZndDsmZ3Q7wqAgPGI+QWRkIGEgdXNlciB0byB0aGUgd2hlZWwgZ3JvdXA8L2I+LiA8YnIgLz48L2Rpdj48ZGl2PjxiciAvPjwvZGl2PjxkaXY+Q2hvb3NlIHlvdXIgY1BhbmVsIHVzZXJuYW1lIGZyb20gdGhlIGxpc3QsIGFuZCBjbGljayA8Yj5BZGQgdG8gR3JvdXA8L2I+LjxiciAvPjwvZGl2PjxiciAvPjxwPjwvcD48ZGl2PjxpbWcgY2xhc3M9ImtiLWltYWdlIiBzcmM9Imh0dHBzOi8vTmFtZWNoZWFwLnNpbXBsZWtiLmNvbS9TaXRlQ29udGVudHMvMi03QzIyRDUyMzZBNDU0M0VCODI3RjNCRDg5MzZFMTUzRS9tZWRpYS9XSE0yMS5wbmciIC8+PC9kaXY+PGRpdj48YnIgLz48L2Rpdj48ZGl2PjIuIERpc2FibGUgU1NIIGxvZ2luIG9wdGlvbiBmb3Igcm9vdDo8YnIgLz48YnIgLz5Ob3cgb3BlbiA8aT4vZXRjL3NzaC9zc2hkX2NvbmZpZzwvaT4uIFlvdSBjYW4gdXNlIG5hbm8gdGV4dCBlZGl0b3IgZm9yIHRoaXM6PGJyIC8+PC9kaXY+PGRpdj48YnIgLz48L2Rpdj48ZGl2PjxpPnN1ZG8gbmFubyAvZXRjL3NzaC9zc2hkX2NvbmZpZzwvaT48YnIgLz48YnIgLz48L2Rpdj48cD48L3A+PGRpdj48aW1nIGNsYXNzPSJrYi1pbWFnZSIgc3JjPSJodHRwczovL05hbWVjaGVhcC5zaW1wbGVrYi5jb20vU2l0ZUNvbnRlbnRzLzItN0MyMkQ1MjM2QTQ1NDNFQjgyN0YzQkQ4OTM2RTE1M0UvbWVkaWEvU1NIc2VjdXJlOS5wbmciIC8+PC9kaXY+PGRpdj48YnIgLz48L2Rpdj5UaGVuIGZpbmQgKGVpdGhlciB3aXRoIG9yIHdpdGhvdXQg4oCcI+KAnSBpbiB0aGUgYmVnaW5uaW5nIG9mIHRoZSBsaW5lKTo8YnIgLz48ZGl2PjxiciAvPjwvZGl2PjxkaXY+PGk+I1Blcm1pdFJvb3RMb2dpbiB5ZXM8L2k+PC9kaXY+PGJyIC8+PHA+PC9wPjxkaXY+PGltZyBjbGFzcz0ia2ItaW1hZ2UiIHNyYz0iaHR0cHM6Ly9OYW1lY2hlYXAuc2ltcGxla2IuY29tL1NpdGVDb250ZW50cy8yLTdDMjJENTIzNkE0NTQzRUI4MjdGM0JEODkzNkUxNTNFL21lZGlhL1NTSHNlY3VyZTEwLnBuZyIgLz48L2Rpdj48ZGl2PjxiciAvPjwvZGl2PjxkaXY+SW5zdGVhZCBzZXQgaXQgdG8gdGhpczo8YnIgLz48aT48YnIgLz48L2k+PC9kaXY+PGRpdj48aT5QZXJtaXRSb290TG9naW4gbm88L2k+PGJyIC8+PGJyIC8+PC9kaXY+PHA+PC9wPjxkaXY+PGltZyBjbGFzcz0ia2ItaW1hZ2UiIHNyYz0iaHR0cHM6Ly9OYW1lY2hlYXAuc2ltcGxla2IuY29tL1NpdGVDb250ZW50cy8yLTdDMjJENTIzNkE0NTQzRUI4MjdGM0JEODkzNkUxNTNFL21lZGlhL1NTSHNlY3VyZTExLnBuZyIgLz48L2Rpdj48ZGl2PjxiciAvPjwvZGl2PjxkaXY+TWFrZSBzdXJlIHRoZSBlZGl0ZWQgbGluZSBkb2Vzbid0IGJlZ2luIHdpdGggPGI+IzwvYj4sIGFzIGl0IHdpbGwgYmUgY29uc2lkZXJlZCBqdXN0IGFzIGEgY29tbWVudCBhbmQgd2lsbCBub3QgdGFrZSBhbnkgZWZmZWN0LjxiciAvPjxiciAvPllvdSBjYW4gZWRpdCB5b3VyIGRlZmF1bHQgU1NIIHBvcnQgaW4gdGhpcyBmaWxlIGFzIHdlbGwuIFNlZSBob3cgdG8gbWFrZSB0aGVzZSBjaGFuZ2VzIGJlbG93LjxiciAvPjxiciAvPjxiciAvPjxwPjxhIG5hbWU9IkNoYW5naW5nIGRlZmF1bHQgU1NIIHBvcnQiPjxiPkNoYW5naW5nIGRlZmF1bHQgU1NIIHBvcnQ8L2I+PC9hPjwvcD48YnIgLz48YnIgLz5CeSBkZWZhdWx0LCB0aGUgU1NIIHBvcnQgaXMgc2V0IHRvIDIyLiA8YnIgLz5Mb2NhdGUgdGhlIGZvbGxvd2luZyBsaW5lIGluIHRoZSBzYW1lIGZpbGUgPGk+L2V0Yy9zc2gvc3NoZF9jb25maWc8L2k+OjxiciAvPjxiciAvPjwvZGl2PjxwPjwvcD48ZGl2PjxpbWcgY2xhc3M9ImtiLWltYWdlIiBzcmM9Imh0dHBzOi8vTmFtZWNoZWFwLnNpbXBsZWtiLmNvbS9TaXRlQ29udGVudHMvMi03QzIyRDUyMzZBNDU0M0VCODI3RjNCRDg5MzZFMTUzRS9tZWRpYS9TU0hzZWN1cmUxMi5wbmciIC8+PC9kaXY+PGRpdj48YnIgLz48L2Rpdj48ZGl2PlJlbW92ZSA8Yj4jPC9iPiBhbmQgY2hhbmdlPGI+IDIyPC9iPiB0byB5b3VyIGRlc2lyZWQgcG9ydCBudW1iZXIuIFRob3VnaCBtYWtlIHN1cmUgeW91IGRvIG5vdCB1c2UgdGhlIHBvcnRzIHdoaWNoIGFyZSB1c2VkIGJ5IG90aGVyIHN5c3RlbXMgKCBpLmUuIDQ2NSw5OTMgd2hpY2ggYXJlIG1haWwgcG9ydHMgZXRjKS48YnIgLz48L2Rpdj48ZGl2PjxiciAvPjwvZGl2PjxkaXY+RS5nOjxiciAvPjxiciAvPjwvZGl2PjxwPjwvcD48ZGl2PjxpbWcgY2xhc3M9ImtiLWltYWdlIiBzcmM9Imh0dHBzOi8vTmFtZWNoZWFwLnNpbXBsZWtiLmNvbS9TaXRlQ29udGVudHMvMi03QzIyRDUyMzZBNDU0M0VCODI3RjNCRDg5MzZFMTUzRS9tZWRpYS9TU0hzZWN1cmUxMy5wbmciIC8+PC9kaXY+PGRpdj48YnIgLz48L2Rpdj48ZGl2PkluIG9yZGVyIHRvIGtlZXAgdGhlIGN1c3RvbSBwb3J0LCBtYWtlIHN1cmUgdGhhdCB0aGUgbmV3IHBvcnQgeW91IHNldCB1cCBpcyB3b3JraW5nLiBGb3IgdGhlIG1ham9yaXR5IG9mIGZpcmV3YWxscywgdGhlIHBvcnRzIHVwIHRvIDEwMDAgYXJlIG9wZW4gYnkgZGVmYXVsdC4gSWYgeW91IHdpbGwgYmUgdXNpbmcgaGlnaGVyIG51bWJlcnMsIG1ha2Ugc3VyZSB0byBvcGVuIHRoZW0gbWFudWFsbHksIGFkZGluZyBhIGNvcnJlc3BvbmRpbmcgcnVsZSB0byB0aGUgZmlyZXdhbGwgc2V0dGluZ3MuPGJyIC8+wqA8YnIgLz5Gb3IgaW5zdGFuY2UsIGl0IGNhbiBiZSBpbXBsZW1lbnRlZCB2aWEgdGhlIENTRiBwbHVnaW4gZm9yIHNlcnZlcnMgd2l0aCBXSE0uIFBsZWFzZSBmb2xsb3cgPGEgaHJlZj0iaHR0cHM6Ly93d3cubmFtZWNoZWFwLmNvbS9zdXBwb3J0L2tub3dsZWRnZWJhc2UvYXJ0aWNsZS5hc3B4Lzk2NjIvNDgvaG93LXRvLXdvcmstd2l0aC10aGUtY3NmLXBsdWdpbi8iPnRoaXMgZ3VpZGU8L2E+LjxiciAvPkluIG9yZGVyIHRvIHRlc3QgdGhlIHNldHRpbmdzIHlvdSBzaG91bGQgbGVhdmUgMiBwb3J0cyBvcGVuZWQ6PGJyIC8+PGI+UG9ydCAyMjwvYj48YnIgLz48Yj5Qb3J0IDIyMzQ1PC9iPjxiciAvPk9uY2UgeW91IGxvZyBvdXQgYW5kIGxvZyBpbiBhZ2FpbiB1c2luZyB5b3VyIGN1c3RvbSBwb3J0LCBhbmQgaGF2ZSBtYWRlIHN1cmUgaXQgaXMgYWxsb3dpbmcgeW91IHRvIGNvbm5lY3QsIHlvdSBtYXkgY29tbWVudCAoIHB1dHRpbmcgPGI+IzwvYj4gYXQgdGhlIGJlZ2lubmluZyBvZiB0aGUgbGluZSkgb3IgZGVsZXRlIHRoZSBzdHJpbmcgd2l0aCBQb3J0IDIyLiA8YnIgLz48YnIgLz48YnIgLz5TYXZlIHRoZSBjaGFuZ2VzIGFuZCBjbG9zZSB0aGUgZmlsZS4gUHJlc3MgPGI+Q3RybCArIE88L2I+IHRvIHNhdmUuIFR5cGUgPGI+Q3RybCArIFg8L2I+IHRvIGV4aXQuPGJyIC8+PGJyIC8+VG8gYXBwbHkgdGhlIHNldHRpbmdzLCB0aGUgU1NIIHNlcnZpY2UgbmVlZHMgdG8gYmUgcmVzdGFydGVkLiBJZiB5b3UgYXJlIGxvZ2dlZCBpbiBhcyBhIHRlY2h1c2VyIChvciB5b3VyIGN1c3RvbSBjcmVhdGVkIG9uZSB0byByZXBsYWNlIHJvb3QpLCB5b3Ugd2lsbCBuZWVkIHRvIHVzZSB0aGUgc3VkbyBjb21tYW5kIHRvIHBlcmZvcm0gdGhpcyBhY3Rpb24uPGJyIC8+PGJyIC8+RGVwZW5kaW5nIG9uIHlvdXIgZGlzdHJvIGFuZCBpdHMgdmVyc2lvbiwgdGhlIHJlcXVpcmVkIGNvbW1hbmQgbWF5IGJlIGRpZmZlcmVudCwgYXMgd2VsbCBhcyB0aGUgbmFtZSBvZiBTU0ggc2VydmljZSAoc3NoZCBmb3IgQ2VudG9zIGFuZCBDbG91ZExpbnV4IGFuZCBzc2ggZm9yIFVidW50dSkuPGJyIC8+SW4gdGhlIGV4YW1wbGUgYmVsb3cgd2UgdXNlIHN1ZG8gc3lzdGVtY3RsIHJlc3RhcnQgc3NoZCBhcyB3ZSBydW4gQ2VudE9TIDcvQWxtYUxpbnV4LjxiciAvPjxiciAvPjwvZGl2PjxwPjwvcD48ZGl2PjxpbWcgY2xhc3M9ImtiLWltYWdlIiBzcmM9Imh0dHBzOi8vTmFtZWNoZWFwLnNpbXBsZWtiLmNvbS9TaXRlQ29udGVudHMvMi03QzIyRDUyMzZBNDU0M0VCODI3RjNCRDg5MzZFMTUzRS9tZWRpYS9TU0hzZWN1cmUxNC5wbmciIC8+PC9kaXY+PGRpdj48YnIgLz48L2Rpdj48ZGl2Pk90aGVyIHZhcmlhbnRzIGlmIHlvdSBydW4gc29tZSBvdGhlciBkaXN0cm8gb3IgdmVyc2lvbiAoZS5nLiBDZW50b3MgNiwgVWJ1bnR1IDE0LjA0IGFuZCBvbGRlciB2ZXJzaW9ucyk6IDxiciAvPjwvZGl2PjxkaXY+PGJyIC8+PC9kaXY+PGk+c3VkbyAvZXRjL2luaXQuZC9zc2hkIHJlc3RhcnQ8YnIgLz5zdWRvIHNlcnZpY2Ugc3NoZCByZXN0YXJ0PGJyIC8+c3VkbyByZXN0YXJ0IHNzaDwvaT48YnIgLz48YnIgLz48YnIgLz5JZiB5b3UgaGF2ZSB0dXJuZWQgb2ZmIHJvb3QgbG9naW4gb24gcHJldmlvdXMgc3RhZ2VzLCB5b3Ugd2lsbCBzdGlsbCBiZSBhYmxlIHRvIGxvZyBpbiB0byB5b3VyIGNvbnRyb2wgcGFuZWwgd2l0aCByb290IGRldGFpbHMuIDxiciAvPklmIHlvdSB1c2UgYSBjUGFuZWwgbGljZW5zZSBmb3IgeW91ciBzZXJ2ZXIsIHlvdSBjYW4gZGlzYWJsZSBwYXNzd29yZCBhdXRoZW50aWNhdGlvbiB1c2luZyB0aGUgU1NIIFBhc3N3b3JkIEF1dGhvcml6YXRpb24gVHdlYWsgbWVudSBpbiB0aGUgV0hNIHBhbmVsLiA8YnIgLz48YnIgLz48Yj5OT1RFPC9iPjogT25jZSB5b3UgcHJlc3MgPGI+RGlzYWJsZSBQYXNzd29yZCBBdXRoPC9iPiwgYWxsIGNQYW5lbCB1c2VycyB3aWxsIGJlIGFibGUgdG8gYWNjZXNzIFNTSCBvbmx5IHZpYSBTU0ggS2V5cy4gPGJyIC8+PGJyIC8+PHA+PC9wPjxpbWcgY2xhc3M9ImtiLWltYWdlIiBzcmM9Imh0dHBzOi8vTmFtZWNoZWFwLnNpbXBsZWtiLmNvbS9TaXRlQ29udGVudHMvMi03QzIyRDUyMzZBNDU0M0VCODI3RjNCRDg5MzZFMTUzRS9tZWRpYS9XSE0yMi5wbmciIC8+PHA+PC9wPjxkaXY+PGJyIC8+PC9kaXY+PGRpdj48YnIgLz48L2Rpdj48ZGl2PjxwPjxhIG5hbWU9IkdlbmVyYXRlIFNTSCBrZXlzIj48Yj5HZW5lcmF0ZSBTU0gga2V5czxiciAvPjwvYj48L2E+PC9wPg0KT24geW91ciBsb2NhbCBtYWNoaW5lLCB5b3UgbmVlZCB0byBoYXZlIGEgcGFpciBvZiBTU0gga2V5cyAob25lIHB1YmxpYyBhbmQgb25lIHByaXZhdGUpLjwvZGl2PjxiciAvPkdlbmVyYXRlIFNTSCBrZXlzIG9uIHlvdXIgbG9jYWwgbWFjaGluZSAoYXBwbGljYWJsZSBmb3IgTGludXggYW5kIE1hY09TKTo8YnIgLz48ZGl2PjxiciAvPjwvZGl2PjxkaXY+PGk+c3NoLWtleWdlbiAtdCByc2E8L2k+PC9kaXY+PGJyIC8+PGJyIC8+WW91IHdpbGwgc2VlIHRoaXMgbWVzc2FnZTo8YnIgLz4mZ3Q7IDxpPkdlbmVyYXRpbmcgcHVibGljL3ByaXZhdGUgcnNhIGtleSBwYWlyPC9pPi48YnIgLz48YnIgLz5XaGVuIHlvdSdyZSBwcm9tcHRlZCB0byA8aT5FbnRlciBmaWxlIGluIHdoaWNoIHRvIHNhdmUgdGhlIGtleTwvaT4sIHByZXNzIDxiPkVudGVyPC9iPi4gVGhpcyBhY2NlcHRzIHRoZSBkZWZhdWx0IGZpbGUgbG9jYXRpb24gYW5kIG5hbWUuIEp1c3QgYmUgc3VyZSBub3QgdG8gb3ZlcndyaXRlIHlvdXIgZXhpc3RpbmcgU1NIIGtleXMuIFlvdSBjYW4gZmluZCB0aGVtIHVzaW5nIHRoZSBjb21tYW5kICh5b3UgY2FuIGNhbmNlbCB0aGUgY3JlYXRpb24gb2YgU1NIIGtleXMgYnkgdXNpbmcgPGI+Q3RybCArIEM8L2I+IHNob3J0Y3V0IGFuZCB0aGVuIHJ1biB0aGUgY29tbWFuZCBiZWxvdyB0byBzZWUgaWYgeW91IGhhdmUgYW55IGtleXMgYWxyZWFkeSk6PGJyIC8+PGRpdj48YnIgLz48L2Rpdj48ZGl2PjxpPmxzIC1sYSB+Ly5zc2gvPC9pPjwvZGl2PjxiciAvPiZndDsgPGk+RW50ZXIgZmlsZSBpbiB3aGljaCB0byBzYXZlIHRoZSBrZXk8L2k+ICgvaG9tZS95b3UvLnNzaC9pZF9yc2EpOiBQcmVzcyA8Yj5FbnRlcjwvYj4uPGJyIC8+PGJyIC8+QXQgdGhlIHByb21wdCwgdHlwZSBhIHNlY3VyZSBwYXNzcGhyYXNlLiBGb3IgbW9yZSBpbmZvcm1hdGlvbiwgc2VlIDxhIGhyZWY9Imh0dHBzOi8vaGVscC5naXRodWIuY29tL2VuL2dpdGh1Yi9hdXRoZW50aWNhdGluZy10by1naXRodWIvd29ya2luZy13aXRoLXNzaC1rZXktcGFzc3BocmFzZXMiIGxpbmt0ZXh0PSJXb3JraW5nIHdpdGggU1NIIGtleSBwYXNzcGhyYXNlcyIgbGlua3R5cGU9IkN1c3RvbSIgdGFyZ2V0PSJfcGFyZW50Ij5Xb3JraW5nIHdpdGggU1NIIGtleSBwYXNzcGhyYXNlczwvYT4uPGJyIC8+PGI+PGJyIC8+RW50ZXIgcGFzc3BocmFzZTwvYj4gKGVtcHR5IGZvciBubyBwYXNzcGhyYXNlKTogVHlwZSBhIHBhc3NwaHJhc2U8YnIgLz48Yj5FbnRlciBzYW1lIHBhc3NwaHJhc2UgYWdhaW48L2I+OiBUeXBlIHBhc3NwaHJhc2UgYWdhaW48YnIgLz48YnIgLz5UaGUgcGFzc3BocmFzZSBpcyB1c2VkIHRvIHByb3RlY3QgeW91ciBrZXkuIFlvdSB3aWxsIGJlIGFza2VkIGZvciBpdCB3aGVuIHlvdSBjb25uZWN0IHZpYSBTU0guIEdlbmVyYXRpbmcgU1NIIGtleXMgd2l0aCBubyBwYXNzcGhyYXNlIGlzIG5vdCByZWNvbW1lbmRlZCBmb3Igc2VjdXJpdHkgcmVhc29ucy48YnIgLz5Zb3UgY2FuIGNoZWNrIHRoZSBwcm9jZXNzIG9mIGdlbmVyYXRpbmcgc3NoIGtleXMgYmVsb3c6PGJyIC8+PGJyIC8+PGRpdj48aW1nIGNsYXNzPSJrYi1pbWFnZSIgc3JjPSJodHRwczovL05hbWVjaGVhcC5zaW1wbGVrYi5jb20vU2l0ZUNvbnRlbnRzLzItN0MyMkQ1MjM2QTQ1NDNFQjgyN0YzQkQ4OTM2RTE1M0UvbWVkaWEvU1NIc2VjdXJlMTYucG5nIiAvPjwvZGl2PjxkaXY+PGJyIC8+PC9kaXY+PGRpdj5PbmNlIHlvdSBoYXZlIGdlbmVyYXRlZCB5b3VyIFNTSCBrZXksIHlvdSB3aWxsIGJlIHByb3ZpZGVkIHdpdGggdHdvIGtleXMuIFlvdSBjYW4gY2hlY2sgdGhlbSBpbiB5b3VyIGhvbWUgZm9sZGVyIGluIGEgZGlyZWN0b3J5IGNhbGxlZCAuc3NoOjxiciAvPjwvZGl2PjxkaXY+PGJyIC8+PC9kaXY+PGRpdj48aT5scyAtbGEgfi8uc3NoLzxiciAvPmlkX3JzYcKgIGlkX3JzYS5wdWI8L2k+PGJyIC8+PGJyIC8+PC9kaXY+PHA+PC9wPjxkaXY+PGltZyBjbGFzcz0ia2ItaW1hZ2UiIHNyYz0iaHR0cHM6Ly9OYW1lY2hlYXAuc2ltcGxla2IuY29tL1NpdGVDb250ZW50cy8yLTdDMjJENTIzNkE0NTQzRUI4MjdGM0JEODkzNkUxNTNFL21lZGlhL1NTSHNlY3VyZTE3LnBuZyIgLz48L2Rpdj48ZGl2PjxiciAvPjwvZGl2PjxkaXY+Rm9yIFdpbmRvd3MgdGhlcmUgYXJlIHZhcmlvdXMgcGllY2VzIG9mIHNvZnR3YXJlIHdoaWNoIGVuYWJsZSB5b3UgdG8gZ2VuZXJhdGUgU1NIIGtleXM6PC9kaXY+PGRpdj48YnIgLz48L2Rpdj48ZGl2PldTTCAoV2luZG93cyAxMCkgcHJvdmlkZXMgYW4gZXhwZXJpZW5jZSBzaW1pbGFyIHRvIHlvdXIgcmVndWxhciBMaW51eCBkaXN0cm8sIHlvdSBqdXN0IG5lZWQgdG8gYWN0aXZhdGUgV1NMLCBpbnN0YWxsIHRoZSBkaXN0cm8gc29mdHdhcmUgeW91IGxpa2UgZnJvbSBXaW5kb3dzIFN0b3JlLCBhbmQgcnVuIGl0IHVzaW5nIHRoZXNlIGluc3RydWN0aW9ucy4gT25jZSB5b3UgaW5zdGFsbCBhbmQgcnVuIGl0LCB5b3UgY2FuIGNyZWF0ZSBTU0gga2V5IHBhaXIgaW4gdGhlIHNhbWUgd2F5IHlvdSBjYW4gb24gTGludXggKGFzIHNob3duIGluIHByZXZpb3VzIHN0ZXBzKS48L2Rpdj48ZGl2PjxiciAvPjwvZGl2PjxkaXY+TW9iYVh0ZXJtLCBDb25FbXUsIGFuZCBzaW1pbGFyIGFsc28gYWxsb3cgeW91IHRvIHNpbXVsYXRlIExpbnV4IFNoZWxsIHNvIHRoYXQgeW91IGNhbiB1c2UgU1NIIHByb2dyYW1zIGluIHRoZSBzYW1lIHdheSB5b3UgZG8gaXQgb24gTGludXggKGFuZCBXU0wpLjwvZGl2PjxkaXY+PGJyIC8+PC9kaXY+PGRpdj5QdVRUWSBpcyBhbiBTU0ggY2xpZW50IHRoYXQgYWxsb3dzIHlvdSB0byBjb25uZWN0IHJlbW90ZWx5IHRvIFNTSCBzZXJ2ZXJzLCBidXQgaXQgZG9lc27igJl0IHNpbXVsYXRlIHNoZWxsIGVudmlyb25tZW50LCBzbyBnZW5lcmF0aW5nIFNTSCBrZXlwYWlyIGhlcmUgaXMgYSBkaWZmZXJlbnQgcHJvY2Vzcy4gRm9yIHRoaXMsIHlvdSB3aWxsIG5lZWQgUHVUVFlnZW4gdGhhdCBpcyBpbnN0YWxsZWQgYWxvbmcgd2l0aCBQdVRUWTo8YnIgLz48L2Rpdj48ZGl2PjxiciAvPjwvZGl2PjxkaXY+MS4gR28gdG8gV2luZG93cyA8Yj5TdGFydDwvYj4gbWVudSAmZ3Q7Jmd0OyA8Yj5BbGwgUHJvZ3JhbXMgPC9iPiZndDsmZ3Q7IDxiPlB1VFRZPC9iPiAmZ3Q7Jmd0OyA8Yj5QdVRUWWdlbjwvYj4uPGJyIC8+PC9kaXY+PGJyIC8+PHA+PC9wPjxkaXY+PGltZyBjbGFzcz0ia2ItaW1hZ2UiIHNyYz0iaHR0cHM6Ly9OYW1lY2hlYXAuc2ltcGxla2IuY29tL1NpdGVDb250ZW50cy8yLTdDMjJENTIzNkE0NTQzRUI4MjdGM0JEODkzNkUxNTNFL21lZGlhL1NTSHNlY3VyZTE4LnBuZyIgLz48L2Rpdj48ZGl2PjxiciAvPjwvZGl2PjxkaXY+Mi4gQ2xpY2sgb24gPGI+R2VuZXJhdGU8L2I+IGFuZCBzdGFydCBtb3ZpbmcgdGhlIG1vdXNlIHJhbmRvbWx5IHdpdGhpbiB0aGUgUHVUVFlnZW4gd2luZG93LjxiciAvPjMuIE9wdGlvbmFsOiBlbnRlciBhIGtleSBjb21tZW50LCB3aGljaCB3aWxsIGlkZW50aWZ5IHRoZSBrZXkgKHVzZWZ1bCB3aGVuIHlvdSB1c2Ugc2V2ZXJhbCBTU0gga2V5cykuPGJyIC8+NC4gVHlwZSBpbiB0aGUgcGFzc3BocmFzZSBhbmQgY29uZmlybSBpdC4gVGhlIHBhc3NwaHJhc2UgaXMgdXNlZCB0byBwcm90ZWN0IHlvdXIga2V5LiBZb3Ugd2lsbCBiZSBhc2tlZCBmb3IgaXQgd2hlbiB5b3UgY29ubmVjdCB2aWEgU1NILjxiciAvPjUuIENsaWNrIDxiPlNhdmUgcHJpdmF0ZSBrZXk8L2I+IGFuZCA8Yj5TYXZlIHB1YmxpYyBrZXk8L2I+IHRvIHNhdmUgeW91ciBrZXlzIGFjY29yZGluZ2x5LjxiciAvPjxiciAvPjwvZGl2PjxwPjwvcD48ZGl2PjxpbWcgY2xhc3M9ImtiLWltYWdlIiBzcmM9Imh0dHBzOi8vTmFtZWNoZWFwLnNpbXBsZWtiLmNvbS9TaXRlQ29udGVudHMvMi03QzIyRDUyMzZBNDU0M0VCODI3RjNCRDg5MzZFMTUzRS9tZWRpYS9TU0hzZWN1cmUxOS5wbmciIC8+PC9kaXY+PGRpdj48YnIgLz48L2Rpdj48ZGl2PllvdSBjYW4gY29weSBhIHB1YmxpYyBrZXkgdG8geW91ciByZW1vdGUgU1NIIHNlcnZlciByaWdodCBmcm9tIHRoZSBQdVRUWWdlbiB3aW5kb3cgYXMgc2hvd24gaW4gdGhlIHNjcmVlbnNob3QuPGJyIC8+PGJyIC8+PGJyIC8+PHA+PGI+Q29weWluZyBwdWJsaWMga2V5IHRvIHlvdXIgU1NIIHNlcnZlcjwvYj48L3A+PGJyIC8+WW91IG5lZWQgdG8gY29weSB5b3VyIHB1YmxpYyBrZXkgdG8gdGhlIHNlcnZlciB0byBhIGZpbGUgY2FsbGVkIDxpPmF1dGhvcml6ZWRfa2V5czwvaT4gbG9jYXRlZCBpbiB0aGUgc2FtZSAuc3NoIGZvbGRlciBvZiB5b3VyIHJlbW90ZSB1c2VyIG9uIHRoZSBzZXJ2ZXIuIFRoZXJlIGlzIGEgY29tbWFuZCBpbiBMaW51eCBhbmQgTWFjT1MgeW91IGNhbiB1c2UgdG8gZG8gdGhpcyBhdXRvbWF0aWNhbGx5OjxiciAvPjxiciAvPjxpPnNzaC1jb3B5LWlkIC1wIHlvdXJfY3VzdG9tX3BvcnRfbnVtYmVyIHRlY2h1c2VyQHlvdXJzZXJ2ZXJJUDwvaT48YnIgLz48YnIgLz5PciB5b3UgY2FuIG1hbnVhbGx5IGNvcHkgY29udGVudHMgb2YgPGk+aWRfcnNhLnB1YjwvaT4gKGl04oCZcyBpbXBvcnRhbnQgdG8gY29weSBjb250ZW50cyBvZiB5b3VyIHB1YmxpYyBrZXksIE5PVCB0aGUgcHJpdmF0ZSBvbmUpOjxiciAvPjxiciAvPjwvZGl2PjxwPjwvcD48aW1nIGNsYXNzPSJrYi1pbWFnZSIgc3JjPSJodHRwczovL05hbWVjaGVhcC5zaW1wbGVrYi5jb20vU2l0ZUNvbnRlbnRzLzItN0MyMkQ1MjM2QTQ1NDNFQjgyN0YzQkQ4OTM2RTE1M0UvbWVkaWEvU1NIc2VjdXJlMjAucG5nIiAvPjxwPjwvcD48ZGl2PjxiciAvPjwvZGl2PjxkaXY+QW5kIHRoZW4gcGFzdGUgaXQgaW4gdGhlIGF1dGhvcml6ZWRfa2V5cyBmaWxlIG9uIHlvdXIgc2VydmVyIChlYWNoIG5ldyBrZXkgYmVnaW5zIG9uIGEgbmV3IGxpbmUsIGluIGNhc2UgeW91IG5lZWQgdG8gYWRkIG11bHRpcGxlIGtleXMgaW4gdGhlIGZ1dHVyZSkuPC9kaXY+PGJyIC8+VG8gZWRpdCB0aGUgYXV0aG9yaXplZF9rZXlzIGZpbGUgb24geW91ciByZW1vdGUgc2VydmVyIHlvdSBjYW4gdXNlIHRoaXMgY29tbWFuZCBvbmNlIHlvdSBhcmUgY29ubmVjdGVkIGJhY2sgdG8gdGhlIHNlcnZlcjo8YnIgLz48ZGl2PjxiciAvPjwvZGl2PjxkaXY+PGk+bmFubyB+Ly5zc2gvYXV0aG9yaXplZF9rZXlzPC9pPjwvZGl2PjxiciAvPjxkaXY+PGltZyBjbGFzcz0ia2ItaW1hZ2UiIHNyYz0iaHR0cHM6Ly9OYW1lY2hlYXAuc2ltcGxla2IuY29tL1NpdGVDb250ZW50cy8yLTdDMjJENTIzNkE0NTQzRUI4MjdGM0JEODkzNkUxNTNFL21lZGlhL1NTSHNlY3VyZTIxLnBuZyIgLz48L2Rpdj48ZGl2PjxiciAvPjwvZGl2PjxkaXY+T25jZSBjaGFuZ2VzIGFyZSBkb25lLCBwcmVzcyA8Yj5DdHJsICsgTzwvYj4gdG8gc2F2ZS4gVHlwZSA8Yj5DdHJsICsgWDwvYj4gdG8gZXhpdDxiciAvPllvdSB3aWxsIHByb2JhYmx5IHNlZSBhbGwgdGhlIHBhc3RlZCB0ZXh0IGluIGEgc2luZ2xlIGxpbmUsIHNvIGl0IG1heSBhcHBlYXIgZGlmZmVyZW50bHkgb24geW91ciBzY3JlZW4uPGJyIC8+PGJyIC8+SWYgeW91IGhhdmUgYSBjUGFuZWwgbGljZW5zZSwgaXQgaXMgcG9zc2libGUgdG8gc2V0IHVwIFNTSCBLZXlzIHVzaW5nIFdITSBvciBjUGFuZWwuPGJyIC8+PC9kaXY+PGRpdj48YnIgLz48L2Rpdj48ZGl2PldITTwvZGl2PjxkaXY+PGJyIC8+PC9kaXY+PGRpdj4xLkxvZyBpbnRvIHlvdXIgV0hNIHBhbmVsIGFzIHJvb3QuPGJyIC8+Mi4gR28gdG8gPGI+U2VjdXJpdHkgQ2VudGVyPC9iPiAmZ3Q7Jmd0OyA8Yj5NYW5hZ2Ugcm9vdOKAmXMgU1NIIEtleXM8L2I+ICZndDsmZ3Q7IDxiPkdlbmVyYXRlIGEgTmV3IEtleTwvYj46PGJyIC8+PGJyIC8+PC9kaXY+PHA+PC9wPjxkaXY+PGltZyBjbGFzcz0ia2ItaW1hZ2UiIHNyYz0iaHR0cHM6Ly9OYW1lY2hlYXAuc2ltcGxla2IuY29tL1NpdGVDb250ZW50cy8yLTdDMjJENTIzNkE0NTQzRUI4MjdGM0JEODkzNkUxNTNFL21lZGlhL1dITTIzLnBuZyIgLz48L2Rpdj48ZGl2PjxiciAvPjwvZGl2PjxkaXY+My5TcGVjaWZ5IHRoZSBrZXkgc2V0dGluZ3M6PC9kaXY+PGRpdj48YnIgLz48L2Rpdj48cD48L3A+PGRpdj48aW1nIGNsYXNzPSJrYi1pbWFnZSIgc3JjPSJodHRwczovL05hbWVjaGVhcC5zaW1wbGVrYi5jb20vU2l0ZUNvbnRlbnRzLzItN0MyMkQ1MjM2QTQ1NDNFQjgyN0YzQkQ4OTM2RTE1M0UvbWVkaWEvV0hNMjQucG5nIiAvPjwvZGl2PjxkaXY+PGJyIC8+PC9kaXY+PGRpdj48Yj5LZXkgTmFtZTwvYj46IGVudGVyIHlvdXIgdW5pcXVlIGtleSAoaW4gdGhpcyBleGFtcGxlIHdlIHVzZWQgbmNzdGVzdCk8YnIgLz48Yj5LZXkgcGFzc3dvcmQ8L2I+OiBlaXRoZXIgZW50ZXIgb3IgaGl0IEdlbmVyYXRlIEtleTxiciAvPjxiPlBhc3N3b3JkIGFnYWluOiByZS1lbnRlciB0aGUgcGFzc3dvcmQgPGJyIC8+Q2hvb3NlIHRoZSB0eXBlPC9iPjogUlNBIChzbG93ZXIgdG8gZ2VuZXJhdGUgYnV0IGZhc3RlciB0byB2YWxpZGF0ZSkgb3IgRFNBIChmYXN0ZXIgdG8gZ2VuZXJhdGUgYnV0IHNsb3dlciB0byB2YWxpZGF0ZSk8YnIgLz48Yj5LZXkgU2l6ZTwvYj46IGNob29zZSB0aGUgS2V5IHNpemUgKHRoZSBoaWdoZXIgdGhlIG51bWJlciwgdGhlIG1vcmUgc2VjdXJpdHksIGJ1dCBzbG93ZXIgYXV0aGVudGljYXRpb24gc3BlZWQpPGJyIC8+QW5kIHByZXNzIDxiPkdlbmVyYXRlIEtleTwvYj4uIDxiciAvPjxiciAvPk9uY2UgaXQgaXMgZG9uZSwgYSBwYWlyIG9mIHB1YmxpYyBhbmQgcHJpdmF0ZSBrZXlzIGFyZSBnZW5lcmF0ZWQuPGJyIC8+SW4gb3JkZXIgdG8gdXNlIGl0IGZvciBhIGxvZ2luIHlvdSBuZWVkIHRvIEF1dGhvcml6ZSB0aGUgcHVibGljIGtleS4gVG8gZG8gc28sIHBsZWFzZSA8Yj5SZXR1cm4gdG8gU1NIIG1hbmFnZXI8L2I+ICZndDsmZ3Q7IDxiPnB1YmxpY19rZXlzPC9iPiAmZ3Q7Jmd0OyBmaW5kIG91dCB5b3VyIGtleXMgYW5kIGdvIHRvIDxiPk1hbmFnZSBBdXRob3JpemF0aW9uPC9iPi48YnIgLz48YnIgLz48L2Rpdj48cD48L3A+PGRpdj48aW1nIGNsYXNzPSJrYi1pbWFnZSIgc3JjPSJodHRwczovL05hbWVjaGVhcC5zaW1wbGVrYi5jb20vU2l0ZUNvbnRlbnRzLzItN0MyMkQ1MjM2QTQ1NDNFQjgyN0YzQkQ4OTM2RTE1M0UvbWVkaWEvU1NIc2VjdXJlMjQucG5nIiAvPjwvZGl2PjxkaXY+PGJyIC8+PC9kaXY+PGRpdj5PbiB0aGUgcHJvbXB0ZWQgd2luZG93LCBwcmVzcyA8Yj5BdXRob3JpemU8L2I+LjxiciAvPjwvZGl2PjxiciAvPjxwPjwvcD48ZGl2PjxpbWcgY2xhc3M9ImtiLWltYWdlIiBzcmM9Imh0dHBzOi8vTmFtZWNoZWFwLnNpbXBsZWtiLmNvbS9TaXRlQ29udGVudHMvMi03QzIyRDUyMzZBNDU0M0VCODI3RjNCRDg5MzZFMTUzRS9tZWRpYS9TU0hzZWN1cmUyNS5wbmciIC8+PC9kaXY+PGRpdj48YnIgLz48L2Rpdj48ZGl2PlRoZW4sIHByZXNzIDxiPlJldHVybiB0byBTU0ggTWFuYWdlcjwvYj4gZmluZCB0aGUgcHJpdmF0ZSBrZXkgeW91IGhhdmUganVzdCBjcmVhdGVkIGFuZCBjb3B5IGl0LjxiciAvPjwvZGl2PjxiciAvPjxwPjwvcD48ZGl2PjxpbWcgY2xhc3M9ImtiLWltYWdlIiBzcmM9Imh0dHBzOi8vTmFtZWNoZWFwLnNpbXBsZWtiLmNvbS9TaXRlQ29udGVudHMvMi03QzIyRDUyMzZBNDU0M0VCODI3RjNCRDg5MzZFMTUzRS9tZWRpYS9TU0hzZWN1cmUyNi5wbmciIC8+PC9kaXY+PGRpdj48YnIgLz48L2Rpdj48ZGl2PklmIHlvdSB3aWxsIGJlIHVzaW5nIFBVVFRZLCB5b3Ugd2lsbCBuZWVkIHRvIGNvbnZlcnQgaXQgdG8gUFBLIGZvcm1hdC4gSW4gb3JkZXIgdG8gZG8gc28sIGVudGVyIHRoZSBwYXNzd29yZCBmb3IgeW91ciB1c2VyIGFuZCBwcmVzcyBjb252ZXJ0LiA8YnIgLz48YnIgLz5UbyBpbXBvcnQgZXhpc3Rpbmcga2V5cywgeW91IGNhbiBnbyBiYWNrIHRvIFNTSCBtYW5hZ2VyLCBhbmQgZmluZCB0aGU8Yj4gSW1wb3J0IEtleTwvYj4gb3B0aW9uLjxiciAvPjxiciAvPjwvZGl2PjxwPjwvcD48aW1nIGNsYXNzPSJrYi1pbWFnZSIgc3JjPSJodHRwczovL05hbWVjaGVhcC5zaW1wbGVrYi5jb20vU2l0ZUNvbnRlbnRzLzItN0MyMkQ1MjM2QTQ1NDNFQjgyN0YzQkQ4OTM2RTE1M0UvbWVkaWEvU1NIc2VjdXJlMjcucG5nIiAvPjxwPjwvcD4NCgkJSW1wb3J0IEtleSB3aWxsIHJlZGlyZWN0IHlvdSB0byB0aGUgZm9sbG93aW5nIHdpbmRvdy4gUGxlYXNlIGNob29zZSBhIG5hbWUgZm9yIHRoaXMga2V5IGFuZCBwYXN0ZSBhIGRlc2lyZWQgKHByaXZhdGUgb3IgcHVibGljKSBrZXkgeW91IHRvIGltcG9ydC4gSXQgd2lsbCBhbHNvIGJlIHBvc3NpYmxlIHRvIGltcG9ydCBhIFBQSyBrZXkuIElmIHlvdSBkb27igJl0IHVzZSBvbmUsIHlvdSBtYXkgbGVhdmUgdGhpcyBmaWVsZCBlbXB0eS4gPGJyIC8+PGJyIC8+PGRpdj48aW1nIGNsYXNzPSJrYi1pbWFnZSIgc3JjPSJodHRwczovL05hbWVjaGVhcC5zaW1wbGVrYi5jb20vU2l0ZUNvbnRlbnRzLzItN0MyMkQ1MjM2QTQ1NDNFQjgyN0YzQkQ4OTM2RTE1M0UvbWVkaWEvU1NIc2VjdXJlMjgucG5nIiAvPjwvZGl2PjxkaXY+PGJyIC8+PC9kaXY+PGRpdj5BbHNvLCB5b3UgY2FuIGdlbmVyYXRlIFNTSCBrZXlzIGRpcmVjdGx5IGZyb20gdGhlIGNQYW5lbC4gPGJyIC8+PC9kaXY+PGRpdj48YnIgLz48L2Rpdj48ZGl2PjxiciAvPjwvZGl2PjxkaXY+PHA+PGEgbmFtZT0iQWNjZXNzaW5nIHRoZSBzZXJ2ZXIgdmlhIFNTSCBrZXlzIj48Yj5BY2Nlc3NpbmcgdGhlIHNlcnZlciB2aWEgU1NIIGtleXM8L2I+PC9hPjwvcD48YnIgLz48L2Rpdj48ZGl2PkZlZWwgZnJlZSB0byBjaGVjayBvbiBob3cgdG8gdXNlIHRoZSBleHBvcnRlZCBwYWlyIG9mIGtleXMgeW91IGNyZWF0ZWQgaW4gPGEgaHJlZj0iaHR0cHM6Ly93d3cubmFtZWNoZWFwLmNvbS9zdXBwb3J0L2tub3dsZWRnZWJhc2UvYXJ0aWNsZS5hc3B4Lzk0MjgvODkvaG93LXRvLWNvbm5lY3QtdmlhLXNzaC11c2luZy1rZXlzIzRiIiBsaW5rdGV4dD0idGhpcyBhcnRpY2xlIiBsaW5rdHlwZT0iQ3VzdG9tIiB0YXJnZXQ9Il9wYXJlbnQiPnRoaXMgYXJ0aWNsZTwvYT4uPGJyIC8+PGJyIC8+PHA+PGEgbmFtZT0iYWRkaXRpb25hbF9pbmZvIj48Yj5BZGRpdGlvbmFsIGluZm9ybWF0aW9uPC9iPjwvYT48L3A+PGJyIC8+RmVlbCBmcmVlIHRvIHVzZSB0aGVzZSBhcnRpY2xlcyBpbiBhZGRpdGlvbiBmb3IgcmVmZXJlbmNlOjxiciAvPjxhIGhyZWY9Imh0dHBzOi8vZG9jcy5jcGFuZWwubmV0L2tub3dsZWRnZS1iYXNlL3NlY3VyaXR5L2hvdy10by1zZWN1cmUtc3NoLyI+SG93IHRvIFNlY3VyZSBTU0g8L2E+OzxiciAvPjxhIGhyZWY9Imh0dHBzOi8vZG9jcy5jcGFuZWwubmV0L2tub3dsZWRnZS1iYXNlL3NlY3VyaXR5L3RpcHMtdG8tbWFrZS15b3VyLXNlcnZlci1tb3JlLXNlY3VyZS8iPlRpcHMgdG8gTWFrZSBZb3VyIFNlcnZlciBNb3JlIFNlY3VyZTwvYT4uPGJyIC8+PGJyIC8+PGJyIC8+VGhhdOKAmXMgaXQuPGJyIC8+PGJyIC8+PGJyIC8+PGRpdiBhbGlnbj0iY2VudGVyIj7CoMKgwqDCoCBOZWVkIGFueSBoZWxwPyBDb250YWN0IG91ciA8YSBocmVmPSJodHRwczovL3d3dy5uYW1lY2hlYXAuY29tL3N1cHBvcnQvbGl2ZS1jaGF0L2dlbmVyYWwvIiBsaW5rdGV4dD0iSGVscERlc2siIGxpbmt0eXBlPSJDdXN0b20iIHRhcmdldD0iX3BhcmVudCI+SGVscERlc2s8L2E+PGJyIC8+PC9kaXY+PGJyIC8+PC9kaXY+PHA+PC9wPg==","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"2024-04-26T09:56:31.0000000","LiveDateTime":"1754-02-02T00:00:00.0000000","CreatedDateTime":"2020-01-10T09:29:45.0000000","ApprovalDatetime":"2020-01-20T12:44:02.0000000","RequestCount":25264,"MarkedAsNew":false,"MarkedAsFeatured":false,"RatingValue":0,"CategoryPaths":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryPathDto","Level":1,"CategoryId":12,"CategoryName":"Hosting"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryPathDto","Level":2,"CategoryId":89,"CategoryName":"SSH Access"}],"AssociatedCategories":[{"CategoryId":89,"CategoryName":"SSH Access","CategoryDisplayName":"HostingSSH Access"}],"AssociatedTags":[{"TagId":81892,"Tag":"SSH secure SSH login"}],"RelatedArticles":[],"AssociatedMedias":[],"PreferredCategoryId":0,"RootParentCategoryName":"","RootParentCategoryId":0},"status":200,"statusText":"OK"},"/api/v1/ncpl/simplekb/getcategorybycategoryid:\"{\\\"categoryId\\\":89}\"":{"body":{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryDto","Description":"VGhlc2UgYXJ0aWNsZXMgZGVzY3JpYmUgYmFzaWMgc3RlcHMgcmVxdWlyZWQgdG8gYWNjZXNzIHlvdXIgaG9zdGluZyBhY2NvdW50IHVzaW5nIHRoZSBzZWN1cmUgU1NIIGNvbm5lY3Rpb24uIEhlcmUgeW91IGNhbiBmaW5kIHRoZSBleGFtcGxlcyBvZiB1c2luZyB0aGUgbW9zdCB3aWRlbHkgdXNlZCBsaW51eCBjb21tYW5kcy48YnIgLz4=","ParentCategoryId":12,"Parent_Category_Name":"Hosting","FriendlyId":null,"ApprovedYN":true,"TreatAsTopicYN":false,"CreatedDateTime":"11/13/2010 09:44:40","CurrentCategoryPaths":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryPathDto","Level":1,"CategoryId":12,"CategoryName":"Hosting"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryPathDto","Level":2,"CategoryId":89,"CategoryName":"SSH Access"}],"RelatedCategories":[],"AssociatedArticles":[{"ArticleId":1015,"Title":"How to find information about commands","ArticleName":"How to find information about commands","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"03/26/2024"},{"ArticleId":10123,"Title":"Using CXS scan via SSH","ArticleName":"Using CXS scan via SSH","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"08/18/2025"},{"ArticleId":10200,"Title":"How to secure your SSH login","ArticleName":"How to secure your SSH login","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"04/26/2024"},{"ArticleId":1007,"Title":"What is SSH?","ArticleName":"What is SSH?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"05/25/2016"},{"ArticleId":131,"Title":"Do you provide SSH? If yes, under what conditions?","ArticleName":"Do you provide SSH? If yes, under what conditions?","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"07/19/2024"},{"ArticleId":1022,"Title":"How to get an SSH client","ArticleName":"How to get an SSH client","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/05/2019"},{"ArticleId":1016,"Title":"How to access a hosting account via SSH","ArticleName":"How to access a hosting account via SSH","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/25/2024"},{"ArticleId":9428,"Title":"How to connect via SSH using keys","ArticleName":"How to connect via SSH using keys","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"05/09/2025"},{"ArticleId":1020,"Title":"How to create a new file","ArticleName":"How to create a new file","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"05/25/2016"},{"ArticleId":1021,"Title":"How to edit a file","ArticleName":"How to edit a file","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"05/25/2016"},{"ArticleId":9571,"Title":"How to download a file via SSH","ArticleName":"How to download a file via SSH","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"12/15/2021"},{"ArticleId":1012,"Title":"How to remove a file","ArticleName":"How to remove a file","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"05/25/2016"},{"ArticleId":1019,"Title":"How to create a new directory","ArticleName":"How to create a new directory","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"05/25/2016"},{"ArticleId":1018,"Title":"How to change a working directory","ArticleName":"How to change a working directory","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"05/25/2016"},{"ArticleId":1013,"Title":"How to remove a directory","ArticleName":"How to remove a directory","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"11/12/2015"},{"ArticleId":1010,"Title":"How to find a current working directory","ArticleName":"How to find a current working directory","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"05/25/2016"},{"ArticleId":1017,"Title":"How to get a list of files and directories","ArticleName":"How to get a list of files and directories","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"05/25/2016"},{"ArticleId":1011,"Title":"How to change permissions for files and directories","ArticleName":"How to change permissions for files and directories","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"09/25/2024"},{"ArticleId":9606,"Title":"How to create a backup of your files via SSH","ArticleName":"How to create a backup of your files via SSH","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"12/21/2021"},{"ArticleId":9184,"Title":"How to import and export a database via SSH","ArticleName":"How to import and export a database via SSH","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"04/29/2025"},{"ArticleId":1249,"Title":"How to remotely connect to a MySQL database located on our shared server","ArticleName":"How to remotely connect to a MySQL database located on our shared server","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"12/02/2021"},{"ArticleId":9586,"Title":"How to deal with Git on our Shared servers","ArticleName":"How to deal with Git on our Shared servers","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"05/27/2019"},{"ArticleId":1008,"Title":"SCP and SFTP - Secure File Transfer Using SSH","ArticleName":"SCP and SFTP - Secure File Transfer Using SSH","LiveDateTime":"02/02/1754 00:00:00","NewTillDate":null,"FeaturedTillDate":null,"ModifiedDateTime":"05/25/2016"}],"AssociatedTags":[],"CategoryId":89,"CategoryName":"SSH Access"},"status":200,"statusText":"OK"},"/api/v1/ncpl/simplekb/getcategories:\"{\\\"parentCategoryId\\\":0,\\\"getTree\\\":true}\"":{"body":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2216,"CategoryName":"Spam Protection"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2217,"CategoryName":"Renewal"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2218,"CategoryName":"cPanel SSL Plugin"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2219,"CategoryName":"PHP Configuration"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2221,"CategoryName":"Multi-Domain SSL Certificates"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2222,"CategoryName":"Cancellation"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2223,"CategoryName":"Browser errors"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2224,"CategoryName":"Site Seal, Logo"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2225,"CategoryName":"SEO"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2226,"CategoryName":"Email Migration"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2211,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2227,"CategoryName":"SSL Resellers"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":true,"Description":"","ImageUrl":"/assets/img/pictograms/150/cloud-red.png","ShortDesc":"","CategoryId":2228,"CategoryName":"Apps","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2228,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2251,"CategoryName":"Supersonic CDN"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2228,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2298,"CategoryName":"Site Maker"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2228,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":177,"CategoryName":"Google Workspace (formerly G Suite)"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2211,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2229,"CategoryName":"Hosting Resellers"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2232,"CategoryName":"DNSSEC"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2234,"CategoryName":"Google Workspace (formerly G Suite)"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2237,"CategoryName":"Host records setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2238,"CategoryName":"SSL installation errors"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/easywp-red.png","ShortDesc":"","CategoryId":2239,"CategoryName":"EasyWP","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2280,"CategoryName":"Getting Started"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2279,"CategoryName":"General Information"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2281,"CategoryName":"WordPress Migration"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2282,"CategoryName":"Plugins and Themes"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2284,"CategoryName":"WordPress Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2285,"CategoryName":"SFTP and Database access"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2286,"CategoryName":"Domains questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2288,"CategoryName":"Billing questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2287,"CategoryName":"SSL questions"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2228,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2251,"CategoryName":"Supersonic CDN"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2252,"CategoryName":"InterWorx questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2253,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2254,"CategoryName":"Domains How-To"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2253,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2255,"CategoryName":"Hosting How-To"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2253,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2257,"CategoryName":"Sales & Payments How-To"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2253,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2258,"CategoryName":"cPanel Email How-To"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2260,"CategoryName":"Private Email Contacts and Calendars Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2253,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2262,"CategoryName":"EasyWP How-To"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"https://download.namecheap.com/assets/img/domainvault-red@2x.png","ShortDesc":"","CategoryId":2289,"CategoryName":"Domain Vault","SubCategories":[]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2290,"CategoryName":"CSR code"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2291,"CategoryName":"Webuzo questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2292,"CategoryName":"Browser Extensions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2293,"CategoryName":"Automated SSL management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2228,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2298,"CategoryName":"Site Maker"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":27,"CategoryName":"Getting Started"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/support-red.png","ShortDesc":"","CategoryId":5,"CategoryName":"General & Support","SubCategories":[]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":7,"CategoryName":"Billing FAQ"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2209,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":8,"CategoryName":"Transfer Information"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":22,"CategoryName":"Hosting Information"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":38,"CategoryName":"SSL General"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":9,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":45,"CategoryName":"Account Security"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":46,"CategoryName":"Domain Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2211,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":63,"CategoryName":"Namecheap API"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2228,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":177,"CategoryName":"Google Workspace (formerly G Suite)"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2179,"CategoryName":"Private Email: General Information"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2274,"CategoryName":"General"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2280,"CategoryName":"Getting Started"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2279,"CategoryName":"General Information"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2215,"CategoryName":"Private Email: Mailbox Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2211,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2196,"CategoryName":"WHMCS module for SSL"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/savings-red.png","ShortDesc":"","CategoryId":2200,"CategoryName":"Checkout & Billing","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":7,"CategoryName":"Billing FAQ"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2201,"CategoryName":"Domains Billing"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":21,"CategoryName":"Hosting Billing"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":71,"CategoryName":"SSL Certificates Billing"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2177,"CategoryName":"Private Email"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2201,"CategoryName":"Domains Billing"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":67,"CategoryName":"Activation"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2209,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":83,"CategoryName":"Transfer to Namecheap"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":9,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":43,"CategoryName":"Profile Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":10,"CategoryName":"DNS Questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":29,"CategoryName":"cPanel questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":21,"CategoryName":"Hosting Billing"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":11,"CategoryName":"Dynamic DNS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":9,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":44,"CategoryName":"Account Access"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2209,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":84,"CategoryName":"Transfer to another provider"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":68,"CategoryName":"Validation"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2182,"CategoryName":"cPanel: Software Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2214,"CategoryName":"Email Forwarding"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2270,"CategoryName":"Routers"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2281,"CategoryName":"WordPress Migration"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2282,"CategoryName":"Plugins and Themes"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2272,"CategoryName":"TV"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2187,"CategoryName":"cPanel: WordPress"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2209,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":219,"CategoryName":"Canceled Transfers"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":71,"CategoryName":"SSL Certificates Billing"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2176,"CategoryName":"Private Email: DNS Settings"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":69,"CategoryName":"Installation"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/reseller-red.png","ShortDesc":"","CategoryId":34,"CategoryName":"Domains","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2232,"CategoryName":"DNSSEC"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2234,"CategoryName":"Google Workspace (formerly G Suite)"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2237,"CategoryName":"Host records setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":46,"CategoryName":"Domain Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":10,"CategoryName":"DNS Questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":11,"CategoryName":"Dynamic DNS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":35,"CategoryName":"Registrations"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2207,"CategoryName":"Renewal questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":36,"CategoryName":"Domains with extended attributes"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":51,"CategoryName":"FreeDNS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":15,"CategoryName":"Namecheap Market"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2208,"CategoryName":"3rd Party Services Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2278,"CategoryName":"Handshake TLDs"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":35,"CategoryName":"Registrations"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":70,"CategoryName":"Reissuance"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/protection-red.png","ShortDesc":"","CategoryId":37,"CategoryName":"Domain Privacy Protection","SubCategories":[]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2200,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2177,"CategoryName":"Private Email"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2178,"CategoryName":"Private Email: Webmail Features"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2207,"CategoryName":"Renewal questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2210,"CategoryName":"cPanel Add-ons"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2273,"CategoryName":"Gaming Consoles"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2284,"CategoryName":"WordPress Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2285,"CategoryName":"SFTP and Database access"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2268,"CategoryName":"macOS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2175,"CategoryName":"Private Email: Client Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/status-red.png","ShortDesc":"","CategoryId":2209,"CategoryName":"Domain Transfers","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2209,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":8,"CategoryName":"Transfer Information"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2209,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":83,"CategoryName":"Transfer to Namecheap"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2209,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":84,"CategoryName":"Transfer to another provider"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2209,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":219,"CategoryName":"Canceled Transfers"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":48,"CategoryName":"VPS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":36,"CategoryName":"Domains with extended attributes"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":true,"Description":"","ImageUrl":"/assets/img/pictograms/150/server-red.png","ShortDesc":"","CategoryId":12,"CategoryName":"Hosting","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2219,"CategoryName":"PHP Configuration"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2225,"CategoryName":"SEO"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2252,"CategoryName":"InterWorx questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2291,"CategoryName":"Webuzo questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":27,"CategoryName":"Getting Started"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":22,"CategoryName":"Hosting Information"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":29,"CategoryName":"cPanel questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2182,"CategoryName":"cPanel: Software Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2187,"CategoryName":"cPanel: WordPress"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2210,"CategoryName":"cPanel Add-ons"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":48,"CategoryName":"VPS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2188,"CategoryName":"Dedicated Server"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":30,"CategoryName":"WHM questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":32,"CategoryName":"DNS settings"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":103,"CategoryName":"LVE (CloudLinux)"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":89,"CategoryName":"SSH Access"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":205,"CategoryName":"FTP questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2180,"CategoryName":"MySQL questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2199,"CategoryName":"Hosting Migration"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2194,"CategoryName":"Tips & Tricks"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":239,"CategoryName":"WHMCS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":33,"CategoryName":"SSL Installation"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2171,"CategoryName":"Private Email: Active Sync (Exchange) Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2188,"CategoryName":"Dedicated Server"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2269,"CategoryName":"iOS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2286,"CategoryName":"Domains questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2288,"CategoryName":"Billing questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2271,"CategoryName":"Linux"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":30,"CategoryName":"WHM questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":31,"CategoryName":"cPanel Email FAQs"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":51,"CategoryName":"FreeDNS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/email-red.png","ShortDesc":"","CategoryId":93,"CategoryName":"Email service","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2216,"CategoryName":"Spam Protection"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2226,"CategoryName":"Email Migration"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2260,"CategoryName":"Private Email Contacts and Calendars Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2179,"CategoryName":"Private Email: General Information"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2215,"CategoryName":"Private Email: Mailbox Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2214,"CategoryName":"Email Forwarding"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2176,"CategoryName":"Private Email: DNS Settings"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2178,"CategoryName":"Private Email: Webmail Features"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2175,"CategoryName":"Private Email: Client Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2171,"CategoryName":"Private Email: Active Sync (Exchange) Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":31,"CategoryName":"cPanel Email FAQs"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2186,"CategoryName":"cPanel Email: Client Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2204,"CategoryName":"Private Email: Video Overview"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":32,"CategoryName":"DNS settings"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":15,"CategoryName":"Namecheap Market"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2186,"CategoryName":"cPanel Email: Client Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2266,"CategoryName":"Windows"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2239,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2287,"CategoryName":"SSL questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2267,"CategoryName":"Android"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2208,"CategoryName":"3rd Party Services Setup"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":93,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2204,"CategoryName":"Private Email: Video Overview"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/security-red.png","ShortDesc":"","CategoryId":14,"CategoryName":"SSL Certificates","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2217,"CategoryName":"Renewal"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2218,"CategoryName":"cPanel SSL Plugin"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2221,"CategoryName":"Multi-Domain SSL Certificates"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2222,"CategoryName":"Cancellation"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2223,"CategoryName":"Browser errors"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2224,"CategoryName":"Site Seal, Logo"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2238,"CategoryName":"SSL installation errors"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2290,"CategoryName":"CSR code"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2293,"CategoryName":"Automated SSL management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":38,"CategoryName":"SSL General"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":67,"CategoryName":"Activation"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":68,"CategoryName":"Validation"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":69,"CategoryName":"Installation"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":14,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":70,"CategoryName":"Reissuance"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":true,"Description":"","ImageUrl":"/assets/img/pictograms/150/performance-red.png","ShortDesc":"","CategoryId":9,"CategoryName":"My Account","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":9,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":45,"CategoryName":"Account Security"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":9,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":43,"CategoryName":"Profile Management"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":9,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":44,"CategoryName":"Account Access"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":34,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2278,"CategoryName":"Handshake TLDs"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":103,"CategoryName":"LVE (CloudLinux)"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/affiliates-red.png","ShortDesc":"","CategoryId":55,"CategoryName":"Affiliates","SubCategories":[]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":89,"CategoryName":"SSH Access"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/tools-red.png","ShortDesc":"","CategoryId":2211,"CategoryName":"API & Resellers","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2211,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2227,"CategoryName":"SSL Resellers"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2211,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2229,"CategoryName":"Hosting Resellers"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2211,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":63,"CategoryName":"Namecheap API"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2211,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2196,"CategoryName":"WHMCS module for SSL"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/timer-red.png","ShortDesc":"","CategoryId":2212,"CategoryName":"Legacy Products","SubCategories":[]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":205,"CategoryName":"FTP questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2180,"CategoryName":"MySQL questions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2199,"CategoryName":"Hosting Migration"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"/assets/img/pictograms/150/premiumdns-red.png","ShortDesc":"","CategoryId":2231,"CategoryName":"PremiumDNS","SubCategories":[]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2194,"CategoryName":"Tips & Tricks"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":0,"TreatAsTopicYN":false,"Description":"","ImageUrl":"https://static.nc-img.com/live-resource/icons/knowledgebase/fastVPN_icon-150px.png","ShortDesc":"","CategoryId":2265,"CategoryName":"FastVPN","SubCategories":[{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2292,"CategoryName":"Browser Extensions"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2274,"CategoryName":"General"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2270,"CategoryName":"Routers"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2272,"CategoryName":"TV"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2273,"CategoryName":"Gaming Consoles"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2268,"CategoryName":"macOS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2269,"CategoryName":"iOS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2271,"CategoryName":"Linux"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2266,"CategoryName":"Windows"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":2265,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":2267,"CategoryName":"Android"}]},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":239,"CategoryName":"WHMCS"},{"__type":"Nc:SimpleKB:Abstractions:Dtos:CategoryItemDto","ParentCategoryId":12,"TreatAsTopicYN":false,"Description":"","ImageUrl":"","ShortDesc":"","CategoryId":33,"CategoryName":"SSL Installation"}],"status":200,"statusText":"OK"}}Accessing the server via SSH keys
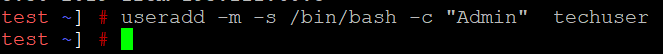
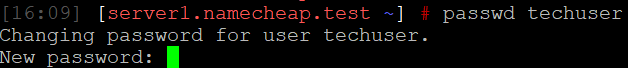


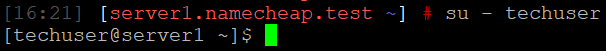
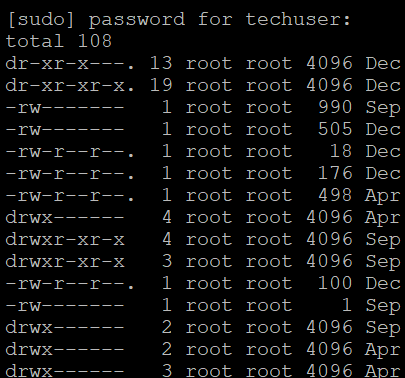

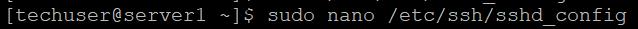
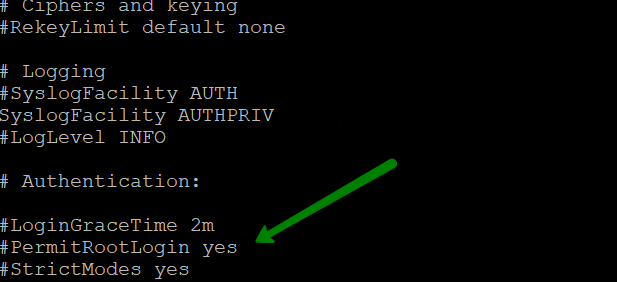

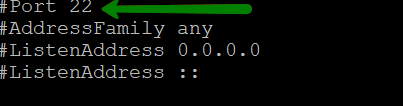
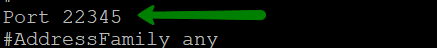
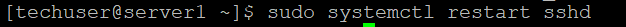
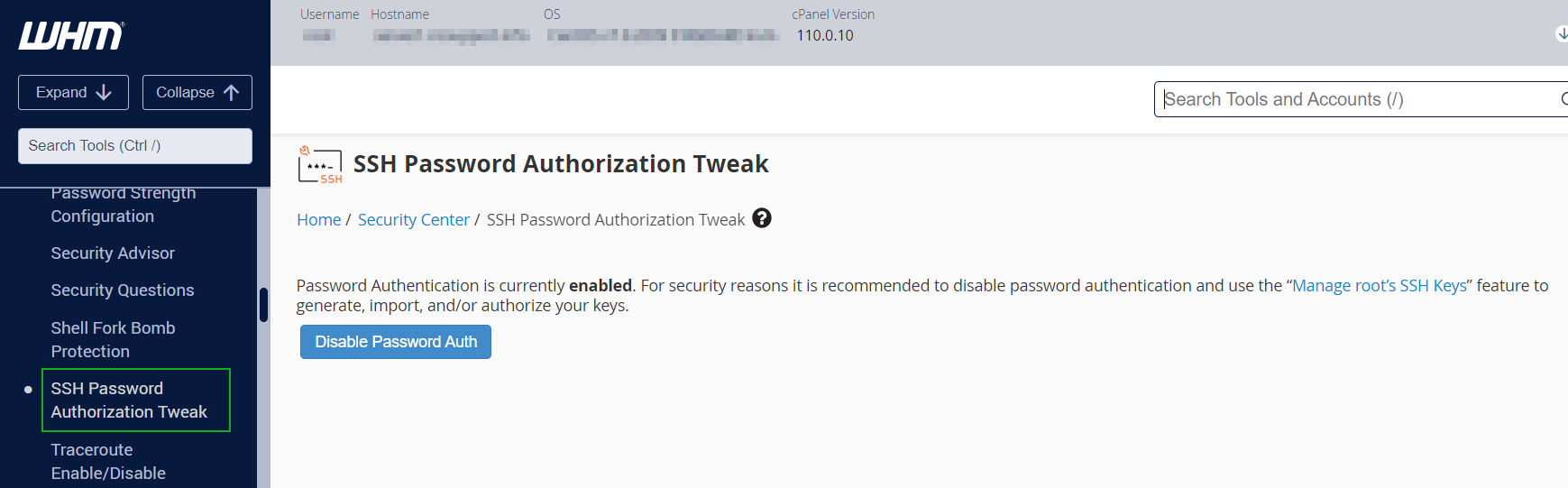
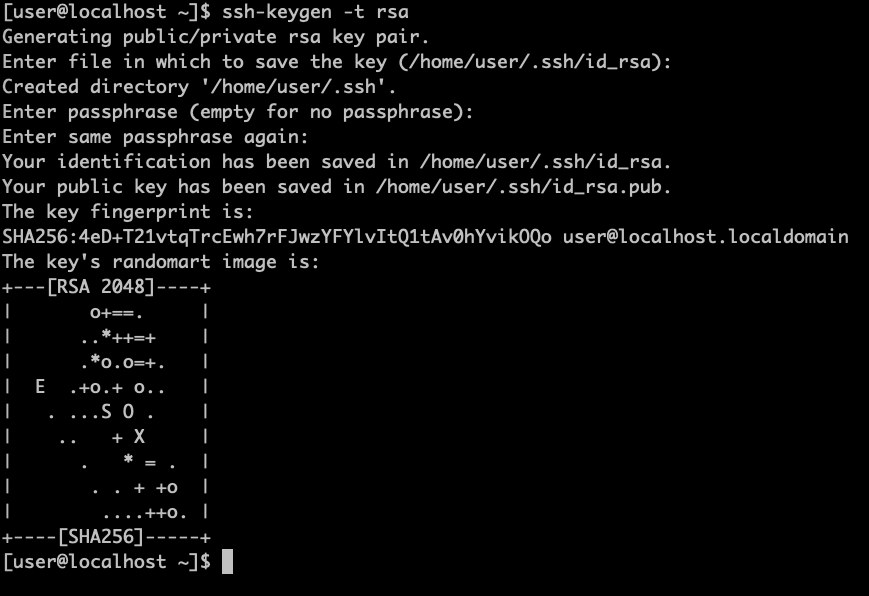
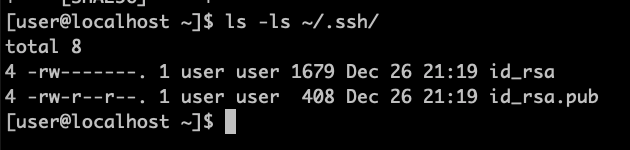
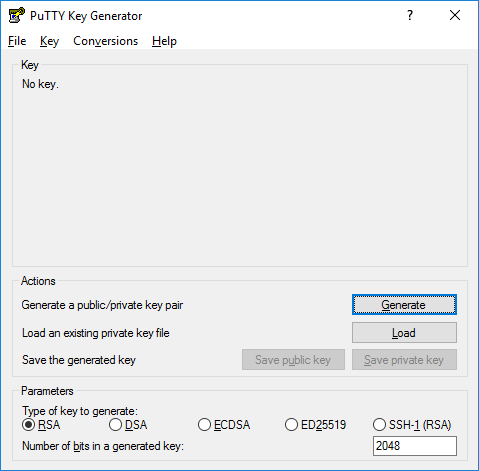
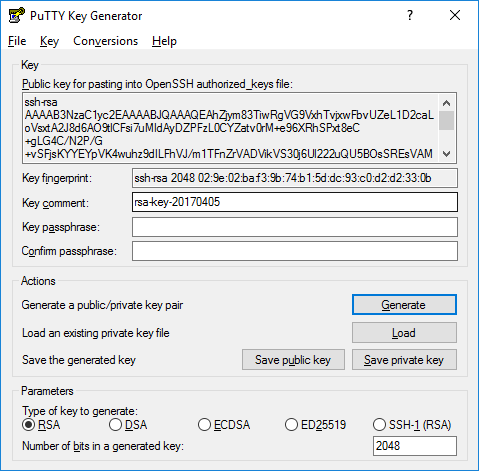
Copying public key to your SSH server
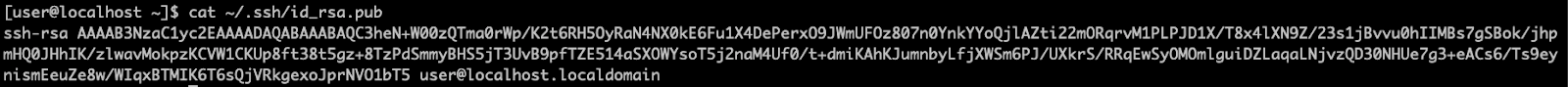
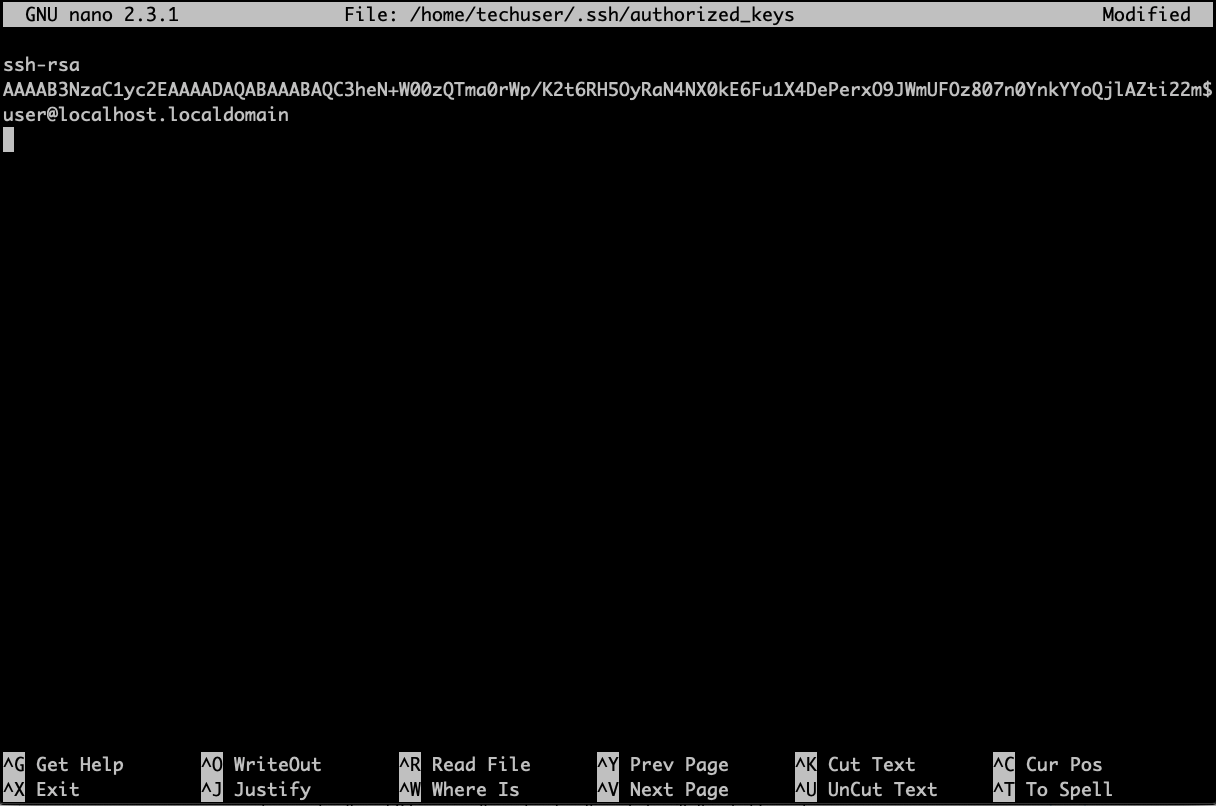

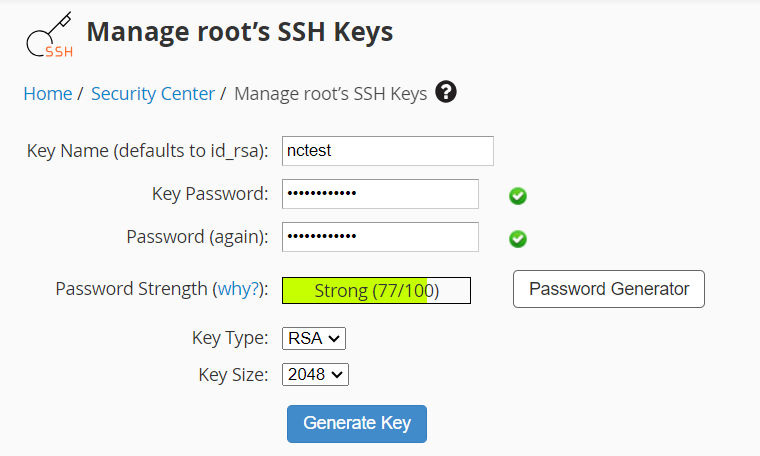

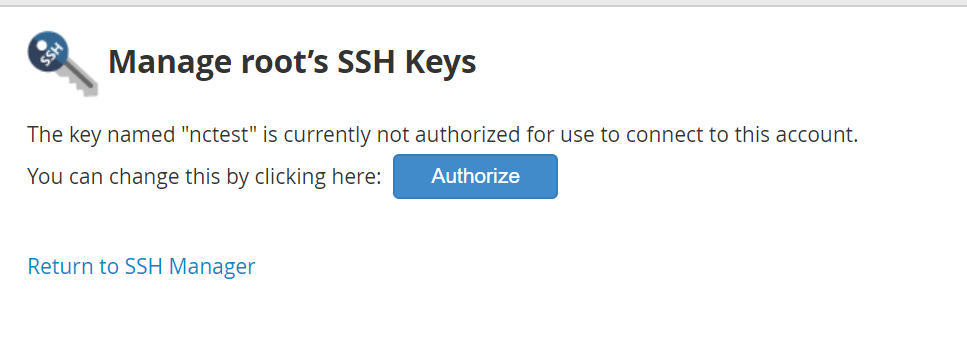
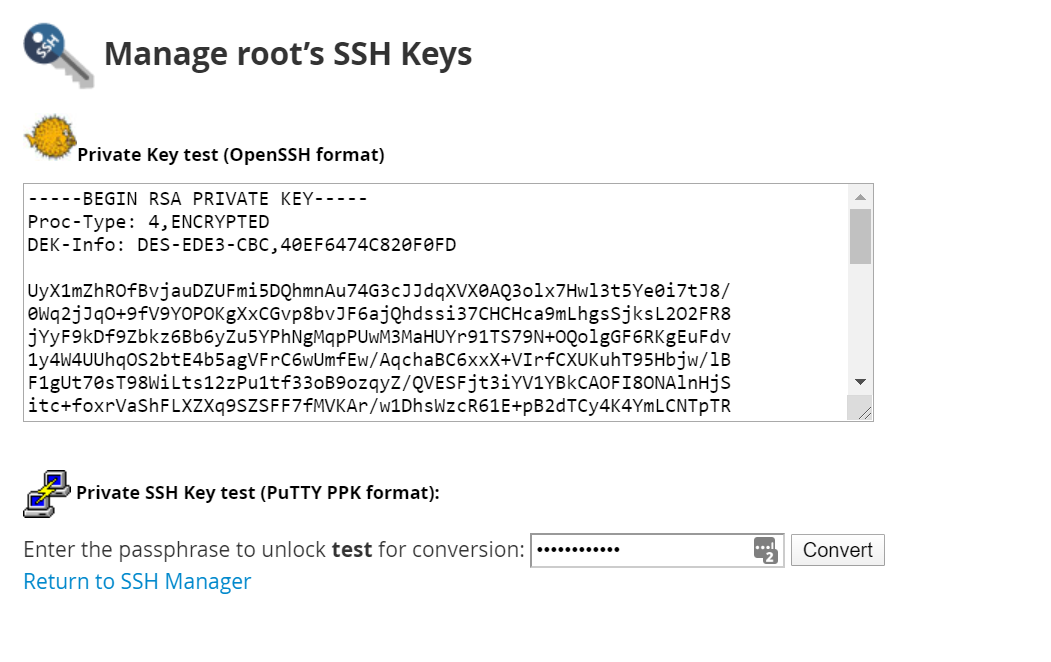
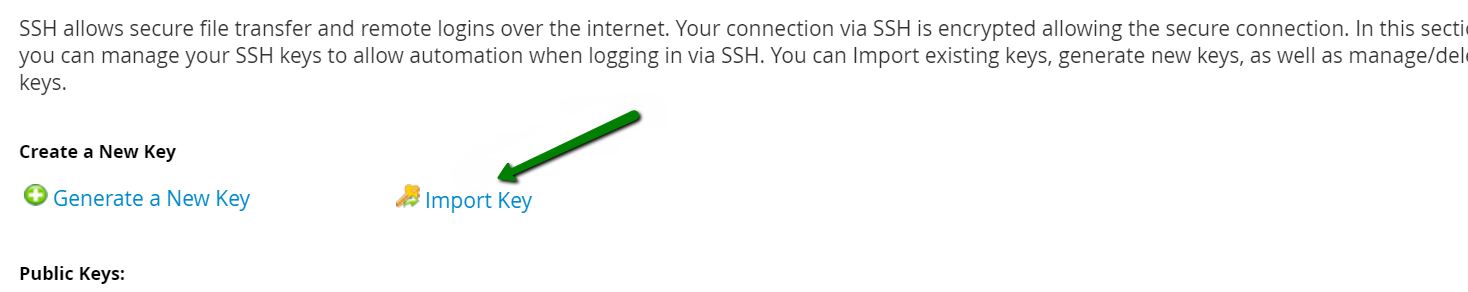 Import Key will redirect you to the following window. Please choose a name for this key and paste a desired (private or public) key you to import. It will also be possible to import a PPK key. If you don’t use one, you may leave this field empty.
Import Key will redirect you to the following window. Please choose a name for this key and paste a desired (private or public) key you to import. It will also be possible to import a PPK key. If you don’t use one, you may leave this field empty. 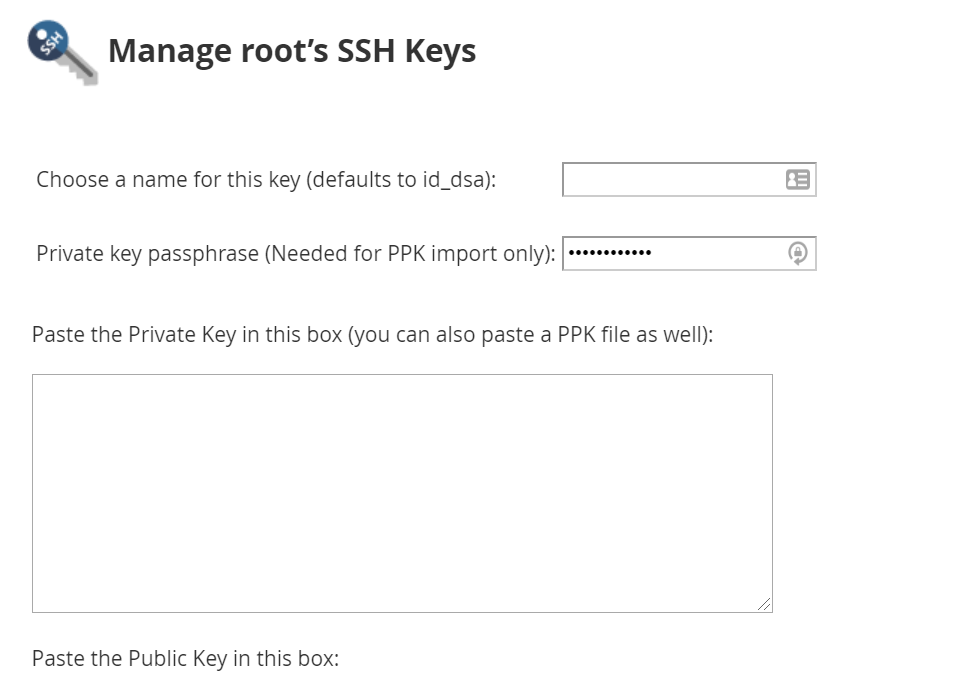
Need help? We're always here for you.